FOCUS TECH MAUI Sources: https://www.cisa.gov/uscert/ncas/alerts/aa22-187a https://stairwell.com/wp-content/uploads/2022/07/Stairwell-Threat-Report-Maui-Ransomware.pdf https://securelist.com/andariel-deploys-dtrack-and-maui-ransomware/107063/ Ransomware Activity Presentation of the figures collected by our tool on the data given by the RaaS platforms about their successful attacks. This graph gives an estimation of the number of victims…
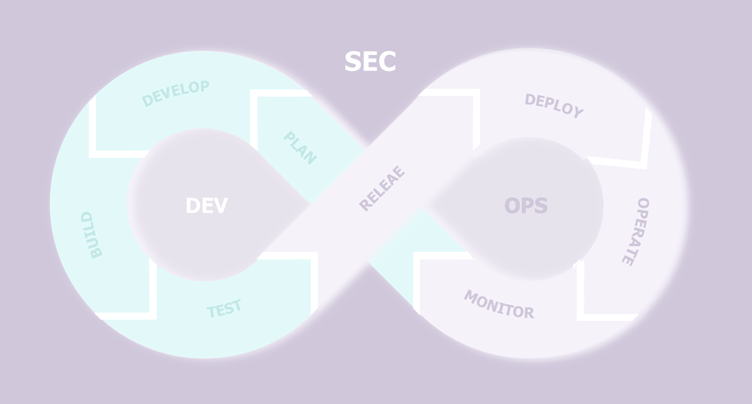
Is it necessary to engage in DevSecOps because projects work in Agile? A few questions need to be asked to get a clearer picture. In previous articles, we talked a lot about how security should be organised to accompany agile…
For the third consecutive time, the French city of Toulon hosted the French southernmost hacking event known as Barb'hack. We - two of Wavestone security auditors - have had the opportunity to attend the conference and participate in the Capture-the-Flag (CTF) event…
Today, many companies have initiated a migration to the public cloud, and this brings its share of benefits, but also new attack surfaces. In this article, we will look at how companies can best manage their security posture, by verifying…
The use of "guest" identities to facilitate collaboration externally The need for collaboration externally entails risks for companies Companies have always needed to collaborate with each other by sharing resources and exchanging data. To do this, their collaborators must…
The content of this article is taken from an interview conducted by Marc JACOB for Global Security Mag in March 2022, available here. The obviousness of IAM, and the difficulty of the transformations it implies Faced with the…
Introduction As stated in a previous article, this year, I had the opportunity to talk on the Main Stage at s4, a 3 day conference, dedicated to ICS cybersecurity, held in Miami South Beach from April 19th to April 21st…
We recently learned from AdvIntel researcher Yelisey Boguslavskiy that the Russian group Conti shut down its operation, thereby making the brand obsolete.[1] This announcement comes only a few months after it was the center of attention of the specialized press…
FOCUS TECH Bumblebee Initial Access (TA0001) Execution (TA0002) Persistence (TA0003) Privilege Escalation (TA0004) Phishing: Spearphishing Attachment T1566.001 Command and Scripting Interpreter: Visual Basic T1059.005 Scheduled Task/Job T1053 Process Injection: Dynamic-link Library Injection T1055.001 Phishing: Spearphishing Link T1566.002 Windows Management Instrumentation…
Since the beginning of its theorisation in the 1950s at the Dartmouth Conference[1] , Artificial Intelligence (AI) has undergone significant development. Today, thanks to advancements and progress in various technological fields such as cloud computing, we find it in various…