Introduction The ever-increasing threat of cyber-attacks on organisations around the world and their potentially devastating financial, reputational, or operational impact on the business means it has never been more important to position Cyber Security as a major issue in front…
Category: Cyberrisk Management & Strategy
Preparing for crisis management is now necessary for most companies and large organizations. Conscious of the risk or driven by regulations (the DORA regulation is a good example), crisis exercises and simulations have become an unmissable annual event. Even if…
Who would have known that locking your employees in a room for 15 minutes could become their new favorite way to learn about cybersecurity? In a never-ending quest to find innovative ways to raise awareness on cybersecurity topics, the Wavestone team…
Regularly rethinking your cyber strategy is a must for cybersecurity teams. Changes in the threat, regulations, business priorities, etc., necessitate an in-depth review of the action plan at least once every three years, or yearly, if necessary. To accomplish this,…
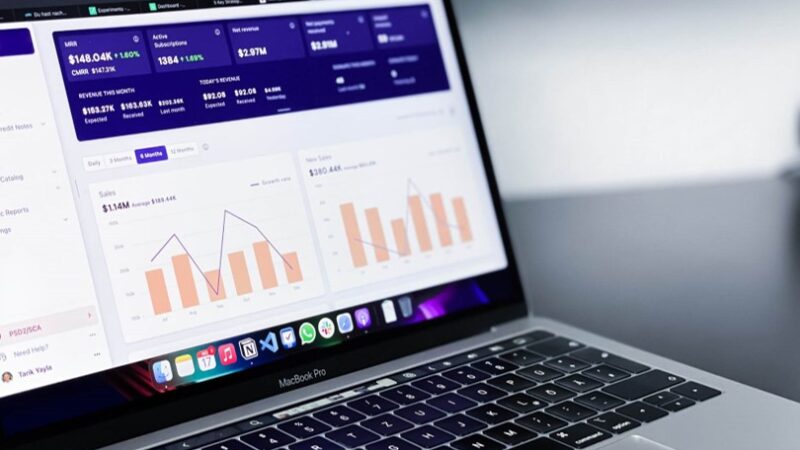
Dashboards are an essential tool for CISOs to measure and control risks in their scope, to steer their projects and to inform their management of the company’s cyber health evolution. However, according to Wavestone’s Cyber benchmark results from 2022, 47%…
Introduction Cyber Supply Chain attacks are a growing trend amongst cybercriminals where one attack can leave countless organizations vulnerable and potentially damaged. You’ve seen the headlines following a number of high-profile incidents in recent months. The European Union Agency for…
The multiple perks of establishing a cyber budget management For the past few years, companies have seen their cybersecurity budgets significantly increasing; according to the latest Gartner reports, they have increased by 51% since 2018. Chief Information Security Officers…
I often talk about cybersecurity awareness: I share concepts and best practices, but today I'm writing from another point of view: that of the person who has been made aware! Yes, experts are not exempt from awareness initiatives... let me…
Backup security is a topic of increasing concern to large accounts, often as part of initiatives to improve their cyber-resilience. When all the protection, detection and response measures have not been sufficient: the information system must be restored quickly from…
After having successfully mobilized its executive committee on cybersecurity, having made a realistic and concrete assessment of the situation, you had an agreement in principle to start a remediation program! A great victory, and the beginning of a multi-year…