In the first article of this series, we explored the foundation of Microsoft’s Enterprise Access Model (EAM), focusing on the critical task of scoping the Control Plane to safeguard cloud administration. We delved into the evolving security landscape, where the traditional AD 3-tiers model is no longer sufficient for the complexities and dependencies of cloud environments. The shift to the cloud has introduced new risks, particularly the global compromise originating from a single weak point of the Control Plane. Then, we emphasized the importance of identifying and isolating key components whose compromise could lead to a global compromise of Entra ID.
In this second article, we will analyze practical attack scenarios that threaten the Control Plane and provide actionable recommendations to mitigate these risks. Specifically, we will explore three common attack scenarios that pose significant threats to the control plane: IT Support compromise, Control Plane Administrator Laptop compromise and CI/CD compromise. By understanding these attack vectors and implementing robust security measures, you can significantly enhance your cloud environment’s resilience against potential compromises.
IT support compromise
Imagine a scenario where the account of a member of the IT support is compromised. This might occur through a phishing attack, social engineering, or even a credential stuffing attempt. Such accounts often can reset passwords, including those of very high-privilege users, like Application Administrator or an Azure’s Owner at root level, thereby gaining unauthorized access to critical resources from Entra ID to the Cloud to On-premises to SaaS.
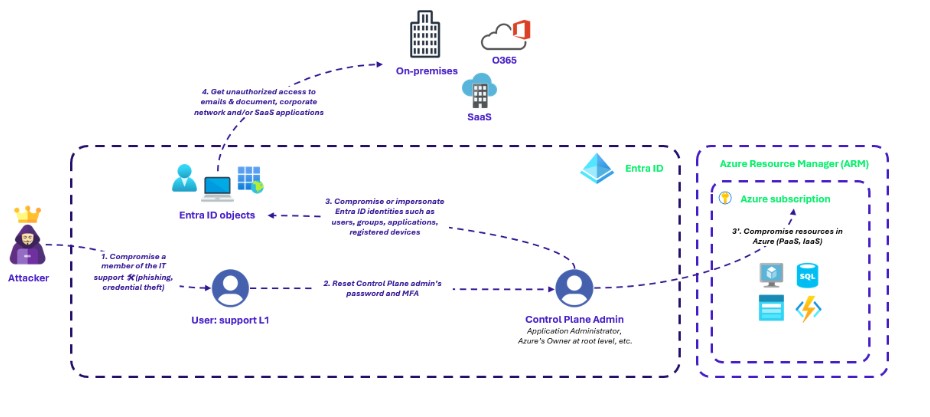
This type of attack illustrates a critical point we discussed in the first article: the need to scope and isolate the control plane effectively. The help desk, while essential for everyday operations, must be rigorously segregated from high-privilege administrative functions. The lack of such separation can allow an attacker to pivot from a compromised help desk account to a Global Admin role.
To mitigate this risk, organizations must implement a series of strategic defenses:
- First, isolating control plane accounts from those managed by IT support is essential. This ensures that even if a help desk account is compromised, it cannot be used to access or manipulate high-privilege accounts.
- Second, using cloud-only accounts dedicated to control plane tasks reduces the likelihood of legacy systems being exploited as an entry point.
- Third, coupling these accounts with phishing-resistant Multi-Factor Authentication (MFA), Just-In-Time admin (JIT), robust identity governance and conditional access policies, strict workstation conformity creates a multi-layered defense that significantly diminishes the risk of such an attack.
This scenario underscores the importance of viewing every account as a potential threat vector. By enforcing strict segregation and controls, you can ensure that your control plane remains secure, even if a lower-tier account is compromised.
Control Plane Admin’s Laptop compromise
Now, consider a situation where the attacker successfully compromises Intune’s Mobile Device Manager (MDM) admin account. With this access, the attacker gains control over Intune admin portal, allowing him to manipulate the laptop of a control plane admin. He can deploy malicious configurations, install backdoors, or directly connect to the admin’s laptop (Remote Help). This access turns the admin’s laptop into a powerful tool for further exploitation, granting the attacker the ability to execute commands, exfiltrate sensitive data, and manipulate cloud resources without the need for additional sophisticated hacking.
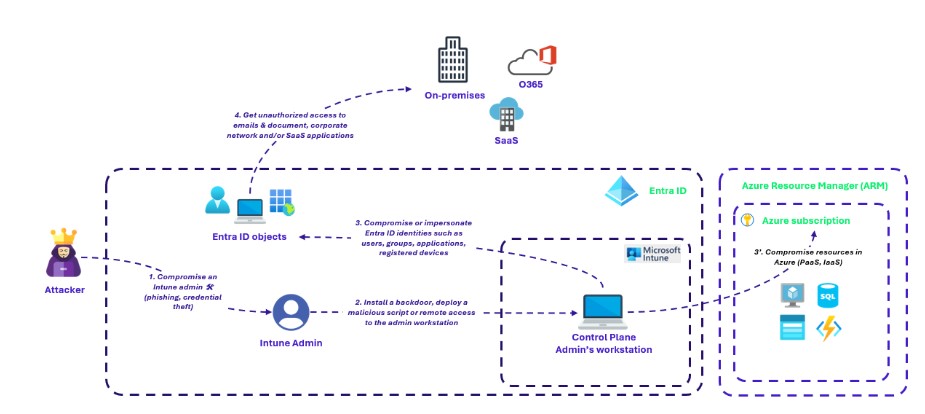
This scenario reminds us of a key principle from the first article: cloud security must be approached holistically. It is not just about securing identities but also ensuring that the devices used to access the Control Plane are secured. In this case, the Control Plane admin’s laptop becomes a critical asset that, if compromised, could undermine even the most sophisticated cloud defences.
To prevent such an outcome, organizations need to integrate admin workstations in the Control Plane. At a minimum, devices used for administrative tasks must be tightly controlled through dedicated MDM policies, ensuring strict access controls, encryption, and continuous monitoring. However, for higher-risk scenarios, leveraging Privileged Access Workstations (PAWs) is essential. PAWs are isolated, hardened machines dedicated solely to administrative activities. They operate under a far stricter security regime than standard devices—limited internet access, dedicated management, and enhanced monitoring—ensuring that they cannot easily become a tool for attackers.
This scenario demonstrates that endpoint security is inseparable from cloud security. By securing the very devices that control your cloud infrastructure, you reduce the chances of a breach originating from compromised endpoints, ensuring that your Control Plane remains protected against even the most sophisticated attacks.
CI/CD compromise
As cloud environments rely heavily on automation, CI/CD pipelines for managing infrastructure become prime targets for attackers. Imagine a scenario where an attacker gains access to a DevOps engineer’s account via phishing or credential theft. With this foothold, he pushes malicious Infrastructure as Code (IaC) change into a Git repository, knowing this will trigger an automated Azure pipeline. The pipeline validates, plans, and deploys the infrastructure on Azure, leading to the destruction or alteration of key Azure resources, i.e. the foundations of the Landing Zone. Alternatively, the attacker modifies the Azure Pipeline’s YAML configuration. By doing so, he causes the pipeline to leak a service principal secret in the logs or debug console, which is then used to make unauthorized Graph API calls. Abusing the overprivileged identity, the attacker can escalate its privilege, compromising Entra ID identities or Office 365 accounts. Runners also play a crucial role in the CICD pipeline. They are agents responsible for executing jobs in the pipeline. They can be hosted and maintained by the Cloud Provider or hosted on-premises. As with any server, their compromise can be used as a pivot point to bounce back to the Landing Zone (e.g., token stealing) or other associated services.
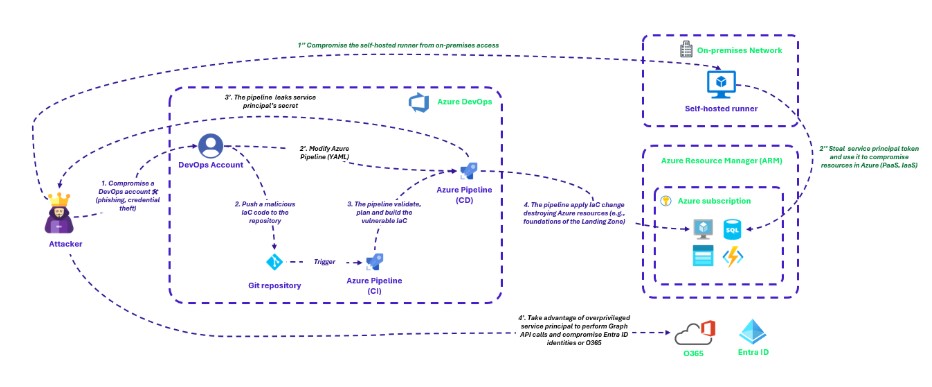
This scenario illustrates interconnectedness of cloud security. The CI/CD pipeline, often seen as a back-office function, is, in reality, deeply integrated with the Control Plane. Its compromise can lead to widespread, devastating consequences to the very foundation of your cloud operations.
To protect against such threat, it is crucial to isolate the Control Plane’s pipeline whose purpose is to build the Landing Zone from project pipelines. Then, one should apply the principle of least privilege, ensuring that accounts and runners within the pipeline have only the permissions they need to perform their tasks. For example, to limit runner permissions we can use federated identity and request OpenID Connect (OIDC) tokens, which provide scoped and temporary access to Cloud Services like Azure. Additionally, adopting automated security practices such as Configuration as Code (CaC) or Policy as Code (PaC), can help reduce human error and ensure consistent security across your deployments.
In cloud security, every process and every tool must be viewed through the lens of potential risk. The CI/CD pipeline is no exception. By securing this critical component, you not only protect your control plane but also ensure the stability and security of your entire cloud infrastructure. This holistic approach to cloud security is what will ultimately keep your operations running smoothly, even in the face of sophisticated attacks.
Synthesis
In this article, we have examined three attack scenarios that threaten the security of the control plane in cloud environments: IT support compromise, Control Plane Admin’s laptop compromise, and CI/CD pipeline compromise.
Each of these scenarios highlights the importance of a multi-layered security approach that includes both technical and organizational measures. We propose a four-step strategy designed to design your Control Plane and secure it against potential attacks:
- Step 1: define what is systemic for your infrastructure: identify the critical components and accounts within your control plane that, if compromised, could lead to a global disruption.
- Step 2: assess your current risk with a security audit: conduct regular security audits to evaluate the current state of your control plane security. This will help you identify vulnerabilities and prioritize remediation efforts.
- Step 3: define a roadmap to isolate and secure the assets most at risk: based on your audit findings, develop a clear roadmap for securing the most critical assets. This should include timelines, resource allocation, and specific actions to mitigate identified risks.
- Step 4: prepare for cloud eraser scenarios: consider worst-case scenarios where entire sections of your cloud infrastructure might be compromised or disabled. Develop contingency plans and ensure that backups and disaster recovery processes are in place.
By following these recommendations, you can build a robust defense against potential threats to your control plane, ensuring that your cloud environment remains secure and resilient.
Thank you to Louis CLAVERO for contributing to this article.


