Enterprise demand for detection probes has been rising in recent years, particularly in the industrial sector. This can be for many reasons: regulatory or contractual constraints, need for incident detection capabilities on the industrial network, desire for greater visibility on industrial assets …
So, let’s answer the question: Should you embark on the OT probes journey? And if so, how could you achieve a successful probes service roll-out?
OT Probes: A tool for monitoring industrial networks
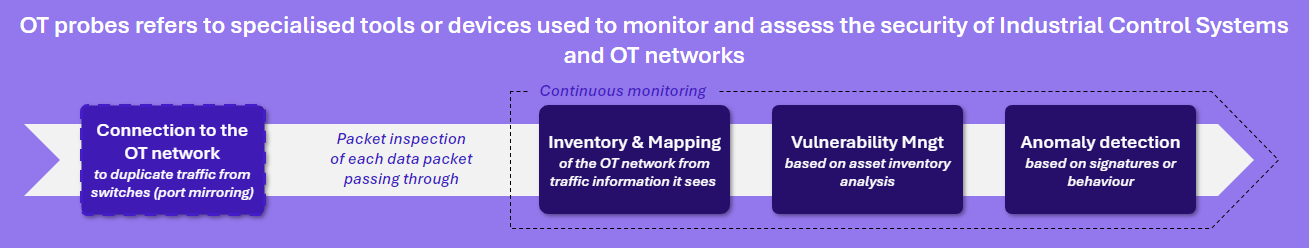
Figure 1: Listening to the network to assess and detect
A detection probe is a piece of equipment, virtual or physical, connected to the information system (IS) in order to map and monitor it. It consists of sensors distributed across the network to collect data. And typically, a central console to aggregate, correlate and analyse this data. Probes for industrial environments – which we will refer to simply as OT probes here – are characterized by their passive, non-invasive listening on the network, and their understanding of industrial protocols and behaviour. Many players are present on the market, you can find our market overview here: https://www.riskinsight-wavestone.com/2021/03/les-sondes-de-detection-en-milieu-industriel-notre-vision-du-marche/
All their probe solutions work on the same principle: network traffic is collected using flow duplication (SPAN, ERSPAN …) or physical duplicator like taps, etc. Packets are inspected in real time to provide several types of data: flow inventory and mapping, asset and vulnerability management, and finally anomaly and incident detection.
This variety of possible use cases of these data and the types of users involved (operational and business team, cybersecurity team, etc.) is what makes OT probes so popular.
However, procuring and deploying these solutions are costly. The organisation must have a clear understanding of their needs, a view of potential users and the exact added value required before embarking on such a project.
Let’s take two very different examples
Imagine two companies are considering deploying OT probes on their industrial sites.
1st Company: WavePetro
WavePetro is a company with a large sensitive site, which has a good level of cybersecurity maturity, as well as a segmented architecture. The company wants to deploy OT probes to be compliant with regulations and to improve its detection capabilities.
Considering its architecture and detection requirements, numerous listening points will be needed on the site. WavePetro can rely on its local teams for expertise and site knowledge to support this complexity.
2nd Company: RenewStone
RenewStone has numerous scattered and unmanned small sites with different cybersecurity maturity levels. The sites are connected to central Group infrastructure.
The company wants to deploy OT probes to gain visibility on its sites using inventory and vulnerability management features.
With this configuration, RenewStone needs to standardize a turnkey OT probe roll-out and run service with as little local complexity as possible.
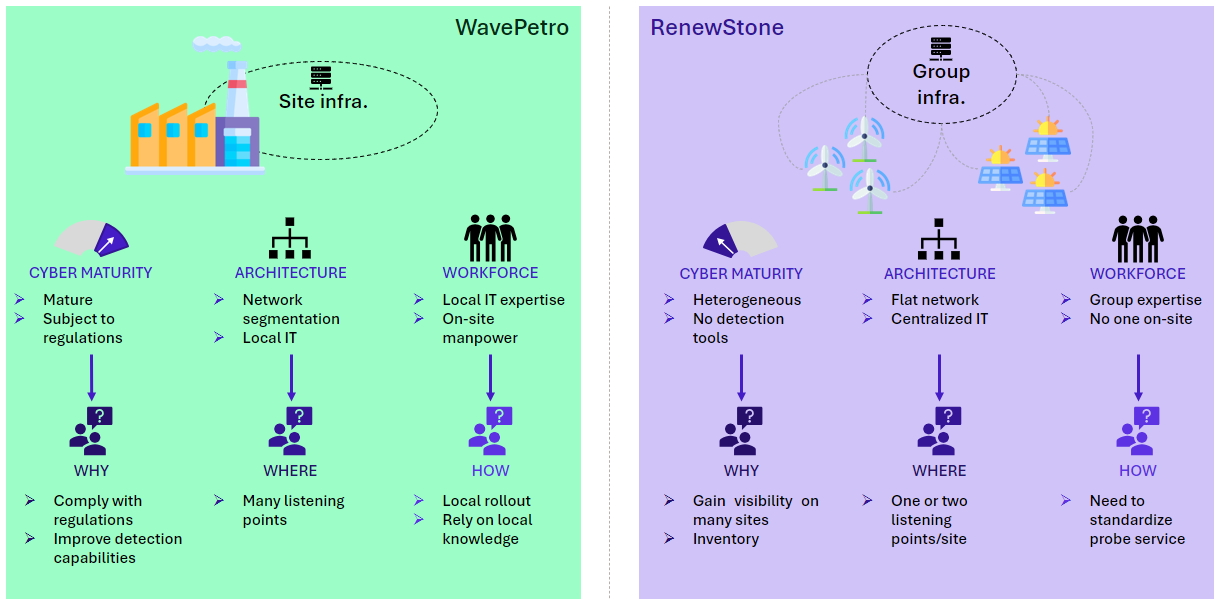
Figure 2: 2 companies, 2 reasons to deploy OT probes, 2 implementation plans
What is required for a successful roll-out?
Although these two companies have different drivers and maturities, they will go through the same 5 key stages, albeit with different approaches.
1.Perform a Proof of Concept
Let’s start with the first step: the proof of concept. The objective for both companies is to test the feasibility and challenge the value this tool brings to the organisation.
While WavePetro have to validate feasibility on a reduced perimeter in the factory, RenewStone has to validate OT probe added value validation on few different sites.
The PoC is key in identifying what can be valuable for both companies. To get the most of it, it is important to:
- Adapt vendors selection to your needs: The market is quite diversified between pure players, those specializing in industry or extending their IT solutions …
Do I want strong detection capabilities? Do I want a managed service? Do I want a unified solution for IT and OT? - Select the PoC scope: Identify a representative scope with resources to test on so that results can be reproduced at scale.
- Draft a target architecture before the PoC: This allows to test an architecture that will be representative of what would be deployed at scale, in order to validate the tests carried out.
PoC is an essential step to ensure that the tool provides value to your company, but also to be able to convince businesses to deploy especially when not constrained by regulations.
2.Build the associated operating model
Even from the early stages, before rollouts, it is important to remember that the end goal of the probes deployment will be to get value from its operation. To be able to do so, it is essential to:
- Define an operating model for handling alerts, managing the inventory and managing the probes themselves. While WavePetro can have an operating model heavily relying on local knowledge and expertise, RenewStone must build a central operation model to include group teams such as SOC, OT security, network, infrastructure and so on.
- Decide whether to call on a third party or manage your probes in-house: Few vendors also propose managed service, so you would need to create your own model, which could also rely – wholly or partly – on externalization.
- Create a RACI: Considering the different use cases and the number of players involved in using or maintaining probes, a RACI is key to ensuring that all stakeholders are involved.
This stage must be addressed upstream to facilitate the next steps.
3.Prepare the roll-out
Once the first step has demonstrated the added value of a probe and their operating model has been defined, let’s prepare for the roll-out. You need to define the final target:
- Where you will deploy: Especially if you have many diverse sites, like RenewStone, you need to be precise on, and prioritize, the scope: It will not be possible to deploy all sites at the same time.
- When you will deploy: Work on budget estimates, even if not accurate, as soon as possible so that sites are able to plan a roll-out on the following year. Probes are an expensive solution, not only in terms of hardware and licensing, but also in terms of the resources required to deploy and operate them.
- How you will deploy: In any case, you need to work on a standard architecture blueprint. But especially if you have many sites to deploy or very limited local resources, you should work on building a packaged service offer to deploy.
This preparation part is key to avoid wasting time with deployments and guarantee their success.
4.Deploy !
Let’s start deploying… The motto is the same for both companies: Start small and grow.
The difference lies in the scale:
- Gradually roll out across the site for WavePetro: It will take some time to be able to listen everywhere effectively. Focus on the expected data to prioritize where to place the probe at first and where to listen to the network.
- Learn and improve from one roll-out to the next for RenewStone: Rollouts are centralized and more standardized, so teams will learn and improve from one roll-out to the next. There should be a first ring of roll-out that is comprised of representative sites to test and improve the deployment model on.
- Include change management: in all cases, the deployment of a new tool must absolutely include awareness-raising and training if probes are to find their users.
Deploying OT probes can be a long and tedious process, but do not get discouraged, because there is still one big step left!
5.Fine-tune OT probe console
A probe roll-out is not a “1-and-done” kind of project. This is a tool for continuous improvement and needs to learn to deliver value. You should therefore dedicate time to:
- Fine-tune OT Probes dashboard: Take time to improve the detection model (whitelist some behaviors, prioritize sensitive assets …), the automatic asset inventory and mapping (enrich inventory, import data, tag VLANs …), and so on. This fine-tuning needs to be done by someone with site-specific knowledge.
- Integrate with other technologies: You can integrate OT probes consoles with your other solutions and tools such as the SIEM, firewalls or CMDBs to make the most of the data collected by the probes.
- Try adding features: once you have gained some maturity over the solution, you can go even further with the features available like performing active queries to enrich the inventory and go even further with the features available.
Fine-tuning enables the solution to reduce the amount of data it retrieves, so that it can focus on security data and alerts that will bring value to your company and its security level.
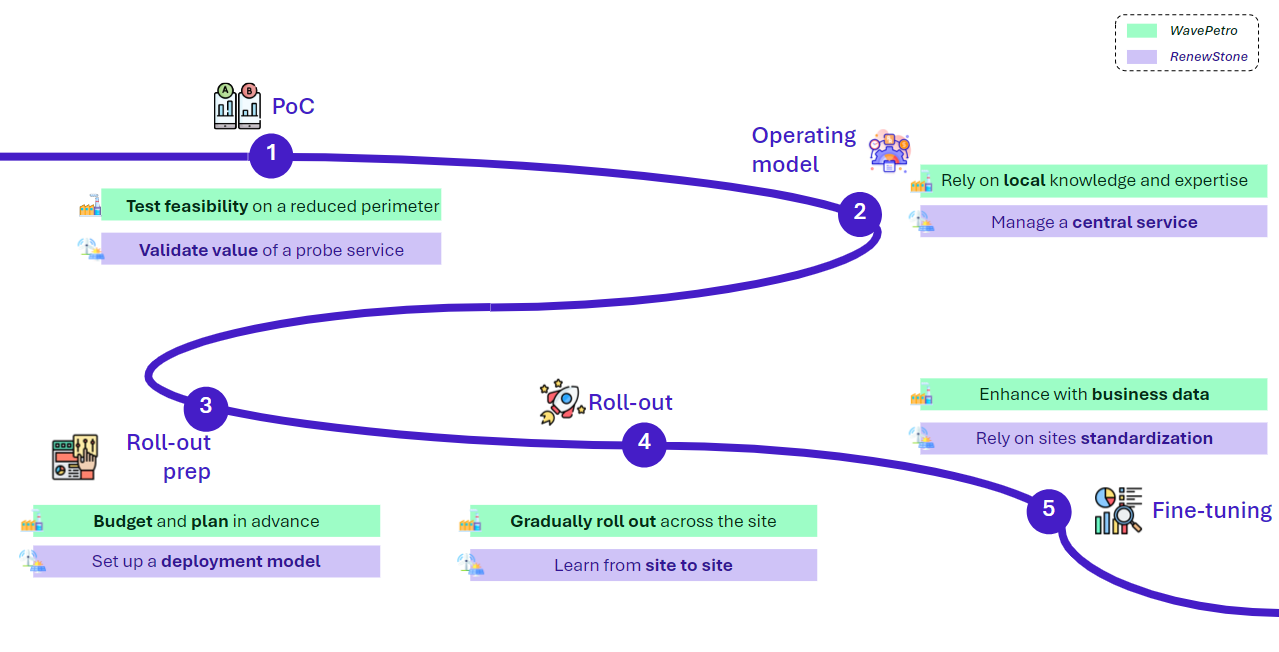
Figure 3: Takeaways from 5 key steps towards an OT probes service
Conclusion
These 2 examples have taught us a lot about OT probes, and the many challenges involved in deploying and using them. If tomorrow, I were facing a customer wondering what to do with this OT Probe project on his roadmap, I would pick out 3 main elements:
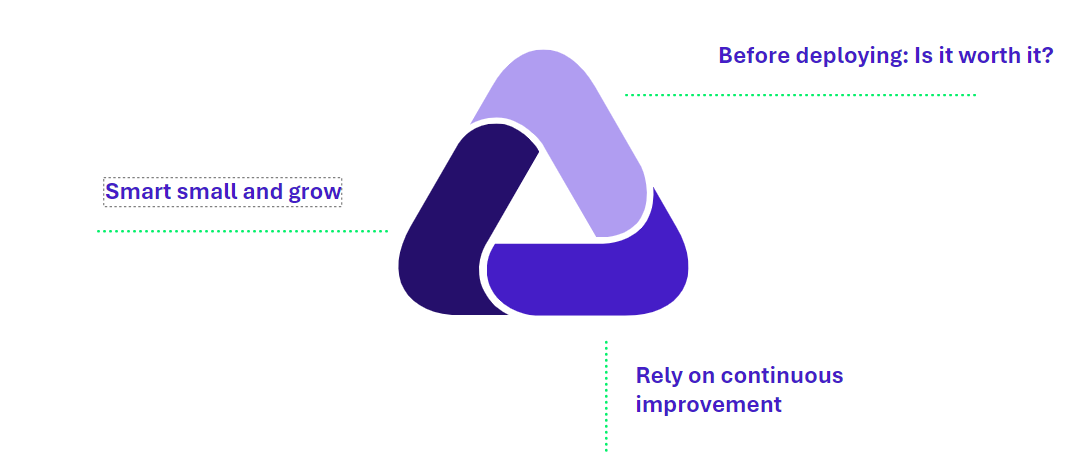
Figure 4: The 3 keys to a successful probe project
Before deploying: Is it worth it ?
Without clearly identified use cases and defined objectives, you may end up with probes providing unused or no real added value information. OT probes are expensive, both financially and in terms of time. You need to make sure they are worth it, and then gives you the means to fully exploit them.
To do this, take the time to evaluate the quality and value of the information provided by the OT probes with your different teams (cybersecurity, operations, business…).
Start small and grow
Don’t be afraid to start small and grow progressively, whether that is in the number of monitored sites, assets or use cases.
The long-term operation of OT probes is complex and builds over deployments. Take the time to take care of the solution adoption: if you want teams to use the solution, train them and demonstrate OT probes value!
Rely on continuous improvement
As for any robust cybersecurity process, continuous improvement should be at its core. Cyber threats are constantly evolving, from attacker techniques to OT exposure due to process digitalization.
In parallel OT Probes can provide a wide of capabilities from incident detection to cartography, vulnerability management and even more yet to be released by editors.
Focus first on capabilities that reduce your OT risks, progressively improving the services as it gains maturity!


