Since the Covid crisis, we’ve seen an increase in the frequency of cyberattacks on the industrial sector. Between 2019 and 2020, the number of such attacks has quadrupled, taking the form of ransomware in 80% of the cases[1], and potentially leading to significant economic consequences.
This trend can be explained by a desire to digitalize factories and develop connected industry that has rarely been accompanied by the modernization of the associated industrial systems: attacks are made simpler, their consequences stronger. And in the case of ransomware, a lack of authentication is often the starting point of the kill-chain: too weak or based on shared authentication factors between operators, accounts become susceptible to phishing attacks.
This observation can also be found by analyzing the “Industrial Cyber IS incident files”[2] shared by Clusif. These include the takeover of the production system of a German steel mill, which could have been avoided if a second authentication factor had been required when carrying out critical actions on the industrial site.
The need to secure and modernize authentication methods for blue-collar workers is therefore crucial, in order to limit the risk of theft of these often poorly protected accounts, without adversely affecting the overall productivity of on-site operators.
The aim of this article is therefore, after going into more detail on the current context and the constraints linked to these populations, to compare the different solutions available today for these uses, to analyze the obstacles to the democratization of the methods deemed the most promising, and to share our vision and recommendations for catching up as best we can.
What is authentication?
Authentication means certifying your identity to a computer system before you can access secure resources. Throughout this article, we’ll be talking about multi-factor authentication when at least two of the four authentication factors below are combined:
- What I know (password, PIN, scheme, etc.)
- What I have (personal device, USB key, smart card, badge, etc.)
- What I am (facial recognition, fingerprint, vein network, etc.)
- What I do (eye movement, signature, typing dynamics, etc.)
Note: the level of security depends on the robustness of the factors and their independence when combined[3].
Blue-collar workers: a diverse range of uses…
When we talk about the blue-collar population, we mean all manual workers who don’t have their own professional workstation (e.g. mechanical, industrial and personal care professions). These populations have different authentication requirements to the so-called white-collar populations, as they mostly use an office information system with multiple devices shared between different employees:
- Mobile workstations and tablets (access to production management software (MES), etc.)
- Fixed control workstations (machine tool control, management, etc.)
- Shared office workstations (time and attendance, training, etc.)
Operators must therefore be able to authenticate themselves on control stations, for example directly connected to the machine tools using a network card, but also independently of their location within the site on mobile stations.
… with multiple constraints
In order to make the best possible assessment of the various authentication solutions available to blue-collar workers, it is important to bear in mind their specific professional constraints.
These can be broken down into three main areas:
- Pace constraints: working under automatic cadence and complying with production standards precludes the use of long or untimely processes.
- Constraints linked to the wearing of PPE (personal protective equipment) such as gloves or masks: these can prevent the use of certain biometric factors (facial recognition, fingerprint, etc.) or make the use of passwords less ergonomic (use of gloves on touch screens or keyboards).
- Constraints linked to regular changes of workstation: regularly changing workstation means having to authenticate several times a day on different workstations. What’s more, if this authentication is local, prior enrolment will have to be carried out for each of them.
Beyond blue-collar constraints, there are other factors to consider from an employer’s point of view.
There are also three main themes:
- An important issue of uniformity: all employees should be able to authenticate in the same way on all machines and software, in order to have a common user experience, a single process, support and documentation.
- Significant investment: an authentication solution is costly to acquire (e.g. badges, wristbands, sensors) but also to maintain (e.g. support & servers). These costs may be difficult to justify if employees don’t need to access sensitive resources.
- Physical security already in place: adding a second factor or hardening the first may seem pointless to companies that already physically secure their sites, and therefore assume that an individual with physical access to the device will be trustworthy.
What authentication methods are available on the market?
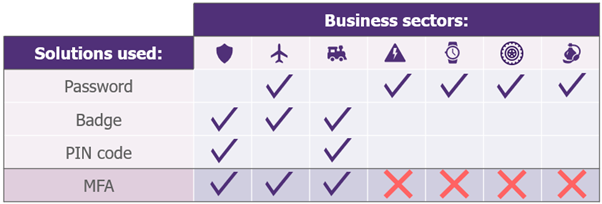
Two main categories stand out:
– “Mature” players, offering multi-factor authentication with a badge coupled with a password or a locally stored PIN code. This choice enables physical and logical access to be merged, for example, by authorizing access to devices controlling production lines via access badges integrating the FIDO2 standard.
– Less mature players, who maintain weak authentication using passwords only. They remain in the majority, and the accounts they use are often generic, to maximize authentication speed and thus productivity.
What authentication methods are needed to meet these challenges?
Several criteria to consider…
In order to compare the various possible methods, six criteria were considered, with particular emphasis on two main issues: user experience and security.
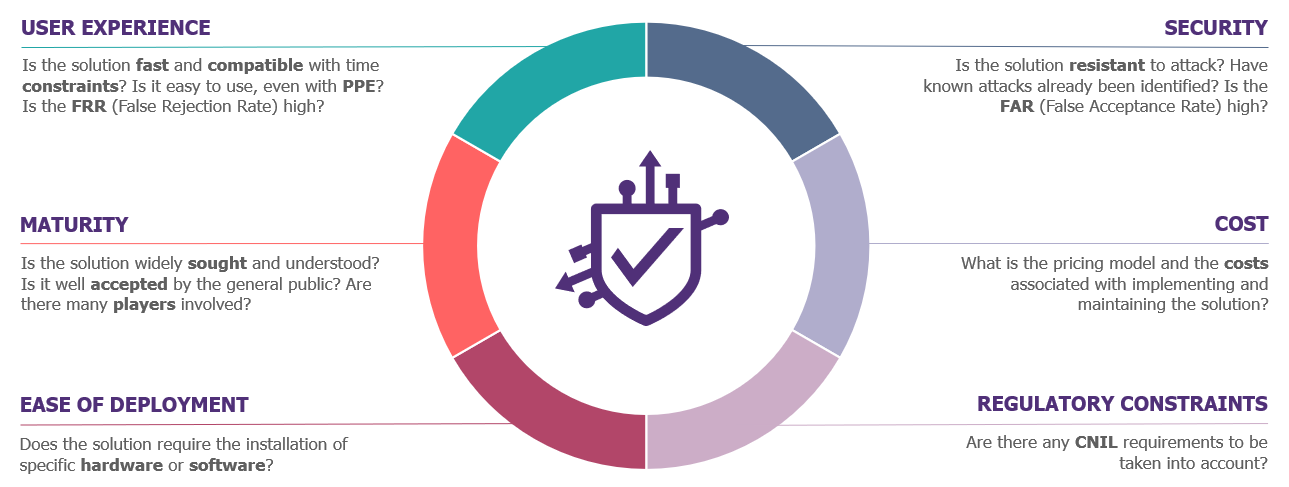
… to identify the most relevant authentication methods
Based on these criteria, the authentication methods considered relevant and viable for blue-collar workers can be distributed as follows:
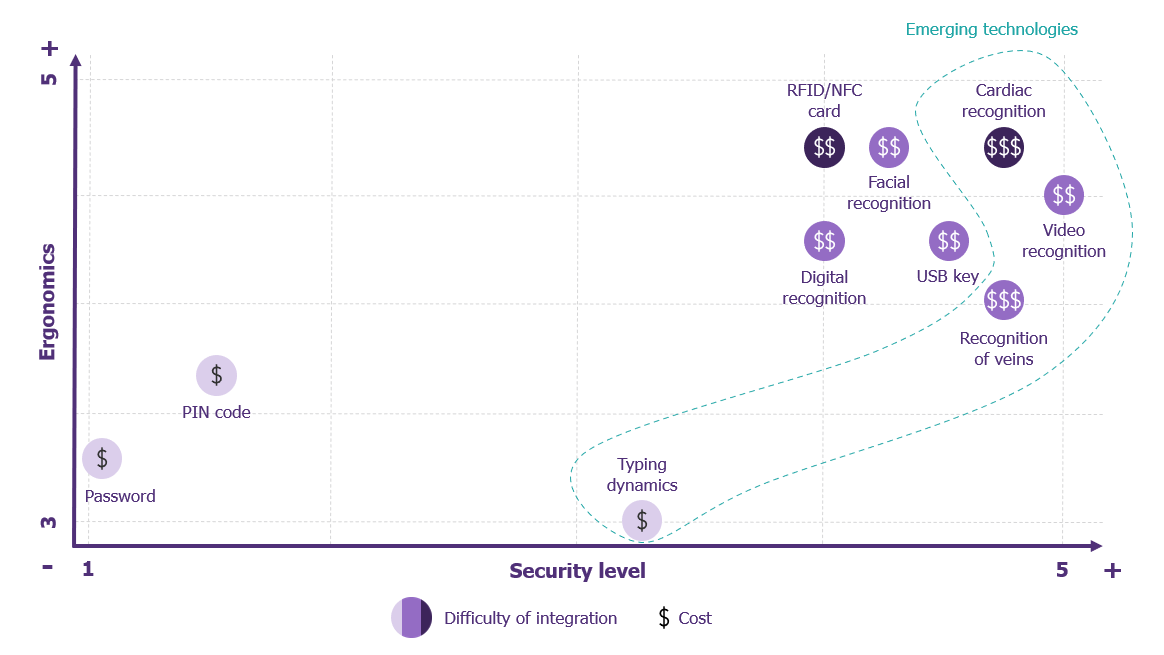
In addition to biometric solutions, which are heavily regulated in France by the CNIL, RFID/NFC cards (badges) are emerging as offering the best ergonomics for a satisfactory level of security. This is in line with what has been observed among “mature” players in this field.
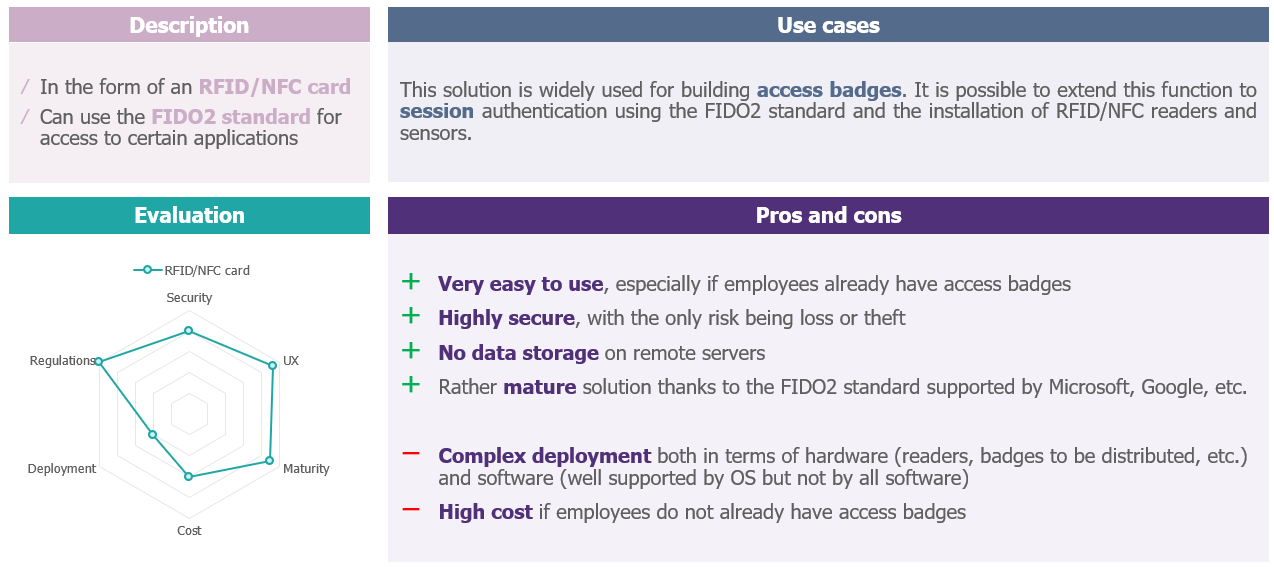
Coupled with a PIN code or password, it enables multi-factor authentication and, for most industrial players, represents an easy-to-use solution for increasing operator access security.
However, it may not be sufficient in particularly sensitive industries, where some innovative solutions may stand out:
The FIDO2 biometric key:

- Many machines have a USB port, and the FIDO2 standard ensures compatibility with a wide range of applications.
- The fingerprint replaces the PIN code, ensuring security even if the key is lost or stolen.
- No biometric images are saved, and no templates are stored anywhere other than in the key.
The biometric wristband is also based on the FIDO2 protocol (example of the “Nymi” wristband, not affiliated with Wavestone):

- Each employee receives a wristband and enrolls using his or her fingerprint.
- At the start of the day, each employee puts on their wristband and unlocks it with their fingerprint.
- As long as employees do not remove their wristbands, they simply pass them by equipment equipped with NFC sensors to authenticate themselves with the FIDO2 standard.
- The wristband is able to detect “life” and locks as soon as it is removed.
- No biometric image is saved, and no template is stored anywhere other than in the employee’s wristband.
These solutions are costly, but offer state-of-the-art security and ergonomics.
Democratization held back by several factors
Although solutions are available, blue-collar authentication is still lagging behind, due to a number of factors:
- Logical access sensitivity: this is not always sufficient to justify the cost of modernizing and strengthening authentication.
- Attackers’ priorities: management and office information systems are still the main targets of attackers, prompting companies to concentrate their security efforts on these areas.
- Software and infrastructure obsolescence: the machines and programs used on production lines may be obsolete. Companies are therefore reluctant to replace these functional resources, at the risk of running into compatibility problems.
- Imposed regulations: the CNIL does not encourage the development of biometric authentication systems in France[4].
However, modernization is set to accelerate thanks to new security requirements linked to the development of the IoT. The FIDO2 standard is also becoming increasingly popular, and innovative solutions are beginning to gain market momentum. Finally, it’s worth noting that some online operators use the same resources as the office population, so passwordless solutions such as Windows Hello for Business are both feasible and easy to implement, thanks to the sensors integrated into devices.
Is the convergence of logical and physical access the solution to trigger large-scale democratization?
Physical access for blue-collar workers is often already secure, since they work on sensitive sites. In most cases, a badge system is already in place for access to buildings and restricted areas, with biometric readers or other surveillance tools (video surveillance, etc.) installed on the most critical sites. This raises the question of capitalizing on and centralizing access control, and offering the same means of authentication for logical access as those already in place for physical access would offer clear advantages, while also raising new challenges:
- Improved user experience, with the same process for all accesses.
- Simplified and reinforced authorization management.
- Physical security teams need to be coordinated with the IT department, and strong governance issues need to be anticipated.
- A common infrastructure is required, with all networks controlling the accesses to be connected.
[1] Authentication Security Best Practices in the Manufacturing Industry, published by Chris Collier on the blog HYPR
[2] Industrial Cyber IS incident files, published by the Clusif
[3] Recommendations for multi-factor authentication and passwords, published by the ANSSI
[4] Biometric access control in the workplace , published by the CNIL


