The PIPL (Personal Information Protection Law) has emerged as an unprecedented first example of highly protective regulation of personal data, establishing an uncertain framework that reinforces China’s control. Despite recent clarifications from China’s authorities, the centralisation of information systems continues to be called into question.
This regulatory challenge extends well beyond China’s borders, raising fundamental questions about how to comply with divergent local regulations in the context of centralised global information systems.
In this article, we explore technological measures to address the concerns of many CIOs about the PIPL law.
1/ PIPL raises broader risks than just compliance risks, highlighting a trend towards decoupling operations
The PIPL is part of China’s digital sovereignty strategy and raises cross-functional issues that go far beyond IT and cyber security. We note that “80% of French companies operating in China have had to adapt their global operations by decoupling certain processes in China[1]“. At the root of this trend are risks such as espionage, compromise of intellectual property or regulatory non-compliance.
A decoupled business process must be accompanied by IT decoupling. IT decoupling is the act of separating a part of an IS to make it more flexible and modular. This allows the decoupled components to operate independently of the central system.
Before starting work to comply with the PIPL law, companies need to ask themselves 3 essential questions:
- Should we maintain a presence in China? A decision at Executive Committee level needs to be made in the light of a strategic analysis assessing the cost/benefit ratio in relation to the current risks. For example, some suppliers refuse to expand their activities in China to avoid losing control of their source code.
- If so, should I decouple my IT architecture to mitigate the risks? It is essential to highlight this study in relation to potential changes in the regulatory landscape to ensure long-term compliance.
- How do I operate and secure a decentralised system? IT and cyber restructuring should be planned according to the different architectural choices made: how should IAM be managed? How can SOC supervision be set up on a decentralised system?

2/ Putting in place a “privacy-by-design” IS architecture
The varied nature of the rules governing the storage and processing of personal data raises a question: is it possible to adapt an IS to facilitate compliance work? Is a “privacy-by-design” architecture realistic?
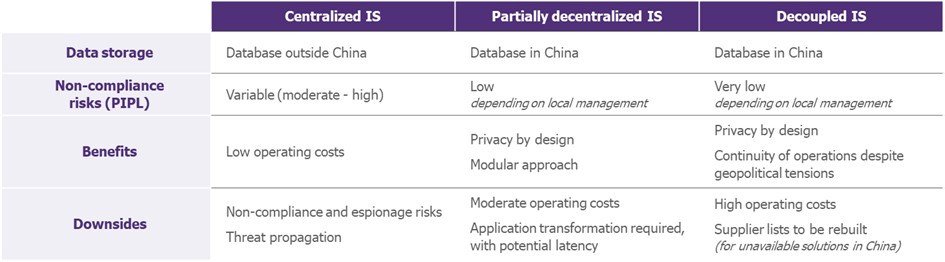
There are 3 possible scenarios, depending on the company’s risk appetite and strategic positioning:
- First, we have our centralised IS (the one we all know). By pooling resources, we can deliver the same service on the same scale and achieve economies of scale. However, Chinese data must be subject to a specific transfer, approved by the CAC (Cyberspace Administration of China). To control and monitor this transfer, all data flows in and out of China could pass through a single gateway (also facilitating emergency isolation, such as Red Buttons). The risk of regulatory non-compliance is controlled at the time of implementation, but can easily drift over time (operational change, application change, new Chinese amendment, etc.).
- Then we have a partially decentralised IS (where the Chinese application instance is decoupled). Data is stored and processed in China using a specific Cloud tenant or an on-premise infrastructure. Application links persist between China and the rest of the world, and data may be transferred from time to time (depending on the regulatory constraints in force). Chinese data is kept separate from the rest, making it easier to ensure the security and confidentiality of personal data.
- Finally, we have a decoupled IS, with an independent local authority. This option is certainly the most advanced, ensuring the highest level of compliance. However, it drastically increases operating costs (local teams, local infrastructure, etc.): this position is difficult to maintain if the company is committed to reducing IT and/or cyber costs. This architecture also provides significant resilience in the event of geopolitical crises, making it easier to execute an exit plan. Recent examples of geopolitical tensions include the Russian[2] [3] subsidiaries Carlsberg and Danone, which were nationalised by Russia, and the war in Ukraine, which led to numerous carve-outs, such as that of Heineken[4].
Should I choose a Cloud Service Provider (CSP) in China?
Alibaba Cloud has long been the preferred Cloud Provider because of the variety of services it offers compared with non-Chinese CSPs. Although this difference between Chinese and non-Chinese CSPs is tending to disappear, Alibaba Cloud could remain the preferred choice: as a Chinese provider, this CSP would be well advised to adapt quickly to any new Chinese regulatory requirements.
How should data transfer be managed?
In a centralised and partially decentralised architecture, data continues to be transferred. Depending on the sensitivity of the data transferred, we can implement data anonymisation or use confidential computing, an increasingly mature technology that guarantees data confidentiality during processing.
However, some cases do not necessarily require data to be transferred. This is the case with certain decentralised learning methods for AI that are “privacy-by-design” (e.g. bagging, federated learning, etc.): the systems are trained locally, and only the learning is transferred.
3/ What can we do in this climate of uncertainty, both in the short and long term?
Short term: a pragmatic risk-based approach
The compliance strategy must be the result of a pragmatic, risk-based approach, in order to minimise the impact on operations. The main steps are as follows:
- Make an inventory of all the data affected: what data and how is it used? How is the data stored, transferred, and processed? How are data access rights managed? Are there any external dependencies with suppliers?
- Assess the risks associated with the data and its use. The format and content of the study must comply with CAC standards.
- Arbitrate a compliance strategy: draw up a compliance strategy based on the 3 scenarios detailed in the previous sections, depending on the sensitivity and criticality of the application data in question.
- Implement technical measures: implement security and confidentiality measures (decoupling, encryption, pseudonymisation, anonymisation, access controls, etc.).
- Monitor and maintain compliance: establish a regular monitoring process to maintain compliance with the PIPL.
Long term: should I be preparing to decouple my IS in China?
PIPL compliance strategy should consider long-term trends, current geopolitical tensions and China’s increasing emphasis on data protection and sovereignty (and uncertainty of current laws).
The cybersecurity regulatory landscape has become denser and more complex in recent years, recalling one of the futures envisaged by the Cyber Campus[5]. Ultra-regulation, linked to the tightening of regulations with the aim of restoring digital confidence, could lead to regulatory incompatibilities and numerous non-compliances or fines.
Fortunately, we are not yet at this stage. However, we must anticipate this trend: PIPL compliance must be a case study forming part of an in-depth reflection on decoupling (with varying levels of separation depending on the situation). This trend towards decoupling could become essential on a wider scale in the next ten years.
[1] CCI France CHINE : Enquête sur les entreprises en Chine, Printemps 2022 https://www.ccifrance-international.org/le-kiosque/n/enquete-sur-les-entreprises-francaises-en-chine-printemps-2022.html#:~:text=Enqu%C3%AAte%20sur%20les%20entreprises%20fran%C3%A7aises%20en%20Chine%20%2D%20Printemps%202022,-25%20mai%202022&text=Avec%20p.
[2] Le Monde, 26/07/2023, « Danone : comment le piège russe s’est refermé sur le géant français des produits laitiers » https://www.lemonde.fr/economie/article/2023/07/26/danone-comment-le-piege-russe-s-est-referme-sur-le-geant-francais-des-produits-laitiers_6183438_3234.html
[3] Le Temps, 19 juillet 2023, « Après Danone et Carlsberg, la Russie se dirige vers la nationalisation d’autres filiales de groupes étrangers » https://www.letemps.ch/economie/apres-danone-et-carlsberg-la-russie-se-dirige-vers-la-nationalisation-d-autres-filiales-de-groupes-etrangers
[4] Les Echos, 25 août 2023, « Heineken se retire définitivement de Russie » https://www.lesechos.fr/industrie-services/conso-distribution/heineken-se-retire-definitivement-de-russie-1972549
[5] Horizon Cyber 2030 : perspectives et défis, Campus Cyber https://campuscyber.fr/resources/anticipation-des-evolutions-de-la-menace-a-venir/


