FOCUS TECH
Bumblebee
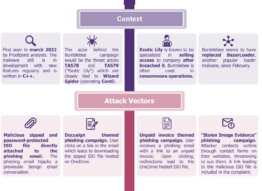
Initial Access(TA0001) |
Execution(TA0002) |
Persistence(TA0003) |
Privilege Escalation(TA0004) |
|
Phishing: Spearphishing Attachment |
Command and Scripting Interpreter: Visual Basic |
Scheduled Task/Job |
Process Injection: Dynamic-link Library Injection |
|
Phishing: Spearphishing Link |
Windows Management Instrumentation |
|
Process Injection: Asynchronous Procedure Call |
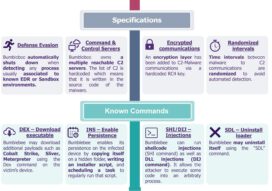
Defense Evasion(TA0005) |
Discovery(TA0007) |
Command and Control(TA0011) |
|
Process Injection: Dynamic-link Library Injection |
System Information Discovery |
Encrypted Channel: Symmetric Cryptography |
|
Process Injection: Asynchronous Procedure Call |
Process Discovery |
Ingress Tool Transfer |
|
Hide Artifacts: Hidden Files and Directories |
|
|
|
Indicator Removal on Host: File Deletion |
|
|
|
Virtualization/Sandbox Evasion |
|
|
|
Deobfuscate/Decode Files or Information |
|
|
SOURCES :
Bumblebee is still transforming, Proofpoint
[1] https://www.malware-traffic-analysis.net/2022/index.html
[2]https://isc.sans.edu/forums/diary/How+the+Contact+Forms+campaign+tricks+people/28142/
CERT-W: FROM THE FRONT LINE
The First Responder Word

Reading Of The Month
We recommend the article of Robert Lemos, a darkreading contributing writer about firms which suffers identity-related breaches.
80% of firms suffered identity-related breaches in last 12 months, Robert Lemos
SEE YOU NEXT MONTH!!