>>FOCUS
Last year, the National Health Service England (NHS) faced its most important cybersecurity crisis due to the Wannacry ransomware attack. In October 2017, the National Audit Office (NAO) published a report showing that at least 34% of trusts in England were disrupted, and around 19,494 patient appointments canceled including canceled patient operations. This was mainly due to the fact that the information system managing the appointments, the patients’ records or test results were infected by the ransomware.
However, the report points out that medical devices such as MRI scanners (that have Windows XP embedded within them) were also locked by the ransomware. Only 1,220 devices were infected representing 1% of the overall amount, because several equipments were disconnected to avoid the ransomware propagation. So why the healthcare sector suffered from such an attack and how come the ransomware spread that easily?
Healthcare cybersecurity: Low maturity level
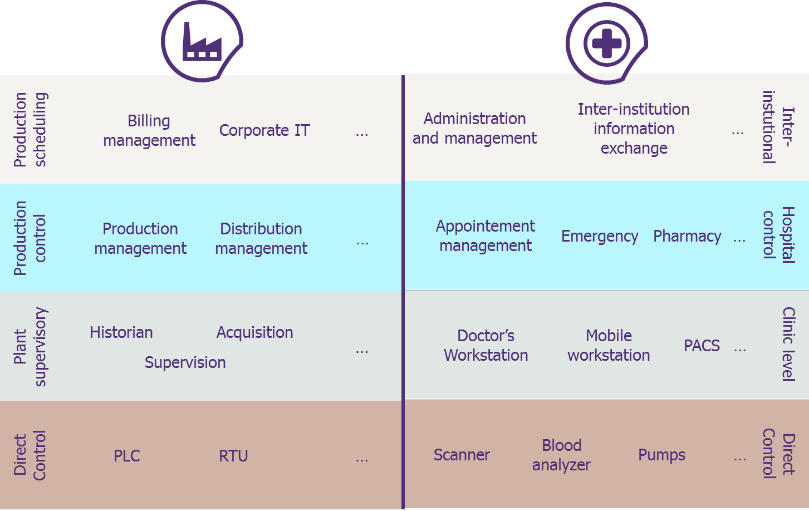
The NAO report highlighted the challenges that the NHS had to face to tackle the attack. These challenges seem similar to the ones that several industries and manufacturers have been facing showing that an analogy of the healthcare information systems and the industrial control systems (ICS) have the same weaknesses.
Indeed, both ICS and Health Information Systems (HIS)face the same cybersecurity challenges, among them:
- The wide use of legacy devices and operating systems (such as Windows XP);
- The length of the window of exposure of these systems (the window of exposure is the time between the vulnerability disclosure and the patching of the system): the vendors support or the quality guidelines and regulations may represent obstacles for a fast patching (a recent survey conducted on 3000 security professionals working for healthcare and pharmaceutical organizations, show that 57% of the respondents had experienced at least a data breach which was conducted after the exploitation of a vulnerability for which a patch had been previously released);
- Critical and unsecure devices directly connected to the Internet exposing the medical network. For example, McAfee published a report explaining how they exploited an unsecure and connected Picture Archiving and Communication System (PACS – device that stores and shares images coming from imaging devices such as scanners) to use personal medical data;
- Lack of security by design: several organizations and researchers have been alerting on several flows affecting medical devices such as pacemakers (Cyber-flaw affects 745,000 pacemakers – BBC), insulin pumps (J&J warns diabetic patients: Insulin pump vulnerable to hacking – Reuters) or infusion pumps (Black hat conference [PDF])
A growing threat on the healthcare sector
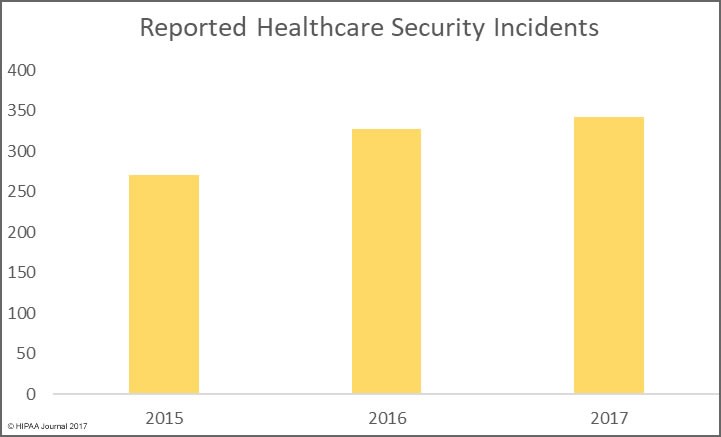
The low cybersecurity maturity level of the healthcare sector combined with the continuous interest of some actors on personal data or life threatening made the threat skyrocket these past few years. Indeed, several cybersecurity companies have been alerting on a growing number of cyber threat actors who are targeting healthcare sector, for example:
- In the last newsletter was reported that a US hospital was hit by Samsam ransomware in January 2018. Samsam is only one of the numerous ransomware that targeted hospitals among them Locky;
- In March 2018, Kaspersky researchers discovered that a Chinese-speaking group used PlugX malware (remote access tool which has been used previously by several groups since 2012) in pharmaceutical organizations for stealing information;
- In April 2018, Symantec identified a new attack group named Orangeworm. This group has been targeting healthcare sector companies (equipments manufactures, pharmaceutical, health organizations) for several years. Orangeworm has been using a backdoor called Kwampirs which collects data in the infected systems. This malware propagates easily in Windows XP devices.
Protecting against
In order to curb the number of security incidents in the healthcare sector, several measures can be, and in some cases have already been, implemented among them:
- Design of a global cybersecurity governance by implementing a cybersecurity policy;
- Conduction of awareness campaigns towards the hospital staff on the cybersecurity threats;
- Implementation of patch management procedure in order to reduce the window of exposure of the system (a combined work with the vendors and the regulation organizations may be required so the patching covers the largest amount of device as possible);
- Network segregation into several levels of protection matching the level of criticality (medical devices should be highly protected).
 Several governmental agencies and institutions have been publishing reports and guidelines in order to help healthcare organizations and the medical devices suppliers in securing their network or providing more secure medical devices. You will find here after some of the documents:
Several governmental agencies and institutions have been publishing reports and guidelines in order to help healthcare organizations and the medical devices suppliers in securing their network or providing more secure medical devices. You will find here after some of the documents:- Cyber security and resilience for Smart Hospitals – ENISA
- Security and Resilience in eHealth Infrastructures and Services – ENISA
- Guide Pratique : Règles pour les dispositifs connectés d’un Système d’Information de Santé – Agence des systèmes d’information partagés de santé [PDF]
- Information for Healthcare Organizations about FDA’s “Guidance for Industry: Cybersecurity for Networked Medical Devices Containing Off-The-Shelf (OTS) Software” – FDA
- The U.S Food & Drug Administration released its Medical Device Safety Action Plan in April 2018

>>Latest news
 |
Aerial tramway with security holes
Golem.de, April 19th Two white hackers found the control system of a new aerial tramway in the internet without any security measures. According to them, the commands were sent unencrypted, the authentication wasn’t provided and the web application was vulnerable to cross-site scritping and HTTP header injection attacks. Link to the article |
|
|
Patch Plugs More Than a Dozen Vulnerabilities Affecting Industrial Secure Router Series
Tripwire, April 16th Cisco Talos published a report revealing several vulnerabilities affecting the Moxa EDR-810 industrial secure router with firewall/NAT/VPN and manager layer 2 switch functions. This router sets perimetric security for critical assets such as pumping/treatment systems in water stations, Distributed Control Systems (DCS) in oil and gas stations … Many of the flaws received a CVSS score of 8.8. Moxa released an updated version of the firmware. Link to the article |
 |
Advisory: Hostile state actors compromising UK organisations with focus on engineering and industrial control companies
NCSC, April 5th The National Cyber Security Centre (NCSC) published an advisory revealing that several ongoing attacks have been targeting mainly engineering and industrial control companies since March 2017. The attacks are involving the harvesting of credentials using strategic web compromises and spear-phishing. The advisory also refers to the Department of Homeland Security (DHS) and FBI joint Technical Alert (see below for more information). Link to the advisory |
|
|
Sentryo Provides Anomaly Detection Technology to Siemens to Address the Cybersecurity Challenges of industrial infrastructures
Sentryo, April Siemens and Sentryo signed an agreement in which Siemens AG will provide Sentryo ICS CyberVision solution to its clients among Siemens products and services. Sentryo’s solution is an asset management and anomaly detection tool designed for Industrial Control Systems. Link to the press release [FR][PDF] |
 |
ISA announces newly published ISA/IEC 62443-4-1-2018 security standard
Automation.com, March 28th The international Society of Automation released the Part 4-1 of the ISA/IEC 62443 standard. This part tackles the Product Security Development Life-Cycle Requirements. “It defines a secure development life-cycle for developing and maintaining secure products.” This includes several concepts such as security by design, patch management and product end-of-life. Link to the article |
 |
Schneider Electric Launches Cybersecurity Virtual Academy
ISS Source, March 27th Schneider Electric launched the Cybersecurity Virtual Academy which is a website that provides several materials to raise the awareness of the cybersecurity risks in the industrial control systems. Link to the article |
 |
Threat landscape for industrial automation systems in H2 2017
Kaspersky lab, March 26th Kaspersky has published a report on the threat landscape over the industrial control systems during the second semester of 2017. In the report, Kaspersky analyses the vulnerabilities discovered by the ICS-CERT and the ones identified by Kaspersky Lab ICS Cert. Here are some figures given in the report:
The Kaspersky figures show also a certain decrease on the number of attacks on ICS systems between 2016 and 2017. This can be explained by the fact that more and more companies are training their employees and began implementing simple cybersecurity measures. Link to the report |
|
|
Draft NIST Special Publication 800-160 Volume 2, Systems Security Engineering: Cyber Resiliency Considerations for the Engineering of Trustworthy Secure Systems
NIST, March 21st The National Institute of Standards and Technology (NIST) released a public draft of the NIST SP 800-160 Volume 2, Systems Security Engineering: Cyber Resiliency Considerations for the engineering of Trustworthy Secure Systems. This document aims to provide guidelines to organizations on how to apply cyber resiliency concepts during the engineering of systems. These guidelines may be applied on new systems, modification of systems, Critical infrastructure systems … Link to the release | Link to the document [PDF] |
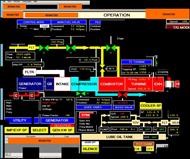 |
Russian Government Cyber Activity Targeting Energy and Other Critical Infrastructure Sectors
US-CERT, March 15th The Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) published a joint Technical Alert in which give details on how the Russian government targeted several American organizations operating in the energy, nuclear, water, commercial facilities aviation and critical manufacturing sectors (DHS and FBI have already warned about this threat in another alert published in October). The alert analyzed the attacks using the Lockheed Cyber Kill Chain (stage1:reconnaissance, stage 2: weaponization, stage 3: delivery, stage 4: exploitation, stage 5: installation, stage 6: command & control, stage 7: actions and objectives). The threat actors after gaining access to their victims information system, they conducted reconnaissance operations within the network. They mainly focused on identifying and browsing file servers. They viewed information and files regarding Industrial Control Systems (ICS) or Supervisory Control And Data Acquisition (SCADA) systems. Link to the alert |
 |
‘Cyber event’ disrupts power in Mich. – but don’t blame hackers
E&E News, March 8th An employee of a public utility that provides electricity in Michigan (Consumers Energy) inadvertently cut the electricity to about 15000 consumers. During an “internal testing” the employee overstepped his authority in a control center leading to the outage. The utility the event as a “cyber event” and reported it to the department of Energy even tought the outage had nothing to do with a malware or cyber attack. Since the event, the company adjusted the access controls. Link to the news |
 |
A Qualitative View of 2017 Across vulnerabilities, threats, and lessons learned in hunting and incident response
Dragos, March Dragos published 3 reports in which they reveal their findings and analysis regarding the industrial control systems vulnerabilities during 2017, the industrial threat landscape incident response and hunting lessons. Some of the results of these reports are the following:
Link to the Vulnerabilities report [PDF] |
|
|
Siemens report: Mideast’s oil and gas sector needs readiness boost as cyber risk grows
Siemens, March A recent report published by Siemens shows that the Middle East facing more and more attacks targeting Operational Technology (OT) (according to the report 30% of the attacks are targeting OT). The report gives the results of a survey on 176 individuals working in the Middle East who are responsible for overseeing the cybersecurity of their organisations. Here are some figures:
|
 |
NERC Full Notice of Penalty regarding Unidentified Registered Entity
NERC, February 28th The North American Electric Reliability Corporation (NERC) files a Notice of Penalty of two million seven hundred thousand dollars ($ 2,700,000), in accordance with the Federal Energy Regulatory Commission (FERC), regarding noncompliance by an Unidentified Registered Entity (URE). Indeed, a third-party URE contractor failed to comply with the information protection program and copied very sensitive data, including records associated with Critical Computer Assets (CCA), from the URE environment on its own unsecured environment. While the data was on the contractor’s network, a subset of data was available online without the need to enter a username or password for a total of 70 days. This exposed information increases the risk of a malicious attacker gaining both physical and remote access to URE’s systems and access to internal CCAs. Link to the article |

>>Main ICS vulnerabilities
| Date | CVSS v3 score | Equipment | Vulnerability | Link to the advisory |
| Apr. 17th | 9.8 | Schneider Electric InduSoft Web Studio and InTouch Machine Edition | Stack-based Buffer Overflow | Link |
| Apr. 17th | 10.0 | Schneider Electric Triconex Tricon | Improper Restriction of Operations within the Bounds of a Memory Buffer | Link |
| Apr. 17th | 9.8 | Rockwell Automation Stratix Services Router | Improper Input Validation, Improper Restriction of Operations within the Bounds of a Memory Buffer, Use of Externally-Controlled Format String | Link |
| Apr. 17th | 9.8 | Rockwell Automation Stratix and ArmorStratix Switches | Improper Input Validation, Resource Management Errors, Improper Restriction of Operations within the Bounds of a Memory Buffer, Use of Externally-Controlled Format String | Link |
| Apr. 17th | 9.8 | Rockwell Automation Stratix Industrial Managed Ethernet Switch | Improper Input Validation, Resource Management Errors, 7PK – Errors, Improper Restriction of Operations within the Bounds of a Memory Buffer, Use of Externally-Controlled Format String | Link |
| Apr. 5th
|
10.0 | Rockwell Automation MicroLogix | Improper Authentication | Link |
| Apr. 3rd
|
9.8 | Siemens Building Technologies Products (Update A) | Stack-based Buffer Overflows, Security Features, Improper Restriction of Operations within the Bounds of a Memory Buffer, NULL Pointer Dereference, XML Entity Expansion, Heap-based Buffer Overflow, Improper Access Control | Link |
| Mar. 29th
|
9.8 | Siemens TIM 1531 IRC | Missing Authentication for Critical Function | Link |
| Mar. 20th
|
9.8 | Geutebruck IP Cameras | Improper Authentication, SQL Injection, Cross-Site Request Forgery, Improper Access Control, Server-Side Request Forgery, Cross-site Scripting | Link |
| Mar. 13th
|
9.3 | OSIsoft PI Web API | Permissions, Privileges, and Access Controls; Cross-site Scripting | Link |
| Mar. 1st | 9.8 | Moxa OnCell G3100-HSPA Series | Reliance on Cookies without Validation and Integrity Checking, Improper Handling of Length Parameter Inconsistency, NULL Pointer Dereference | Link |

>>Upcoming ICS events
|
Jun. 30-1 |
Nuit du Hack
Paris, France |
|
Jun. 18 |
IEEE Workshop on Smart Industries (IEEE SIW)
Taormina, Italy |
|
Jun. 15 |
European Maritime Cyber Risk Management Summit
London, UK |
|
May. 22-23 |
Annual Nuclear Industrial Control Cybersecurity and Resilience Conference (ICCS)
Warrington, UK |
|
May. 3-4 |
Global Cyber Security in Healthcare & Pharma Summit
London, UK |