Over the past few years, companies have been rapidly adopting security tools to protect their applications across the development lifecycle, leveraging DevSecOps scanners such as SAST, DAST, SCA, and scanners for containers, Infrastructure-as-Code, and secrets. Progressively, the goal has shifted from simple vulnerability detection to seamless integration and automation within CI/CD pipelines.
This is where Application Security Posture Management (ASPM) steps in. Managing numerous applications and their associated security tools while maintaining comprehensive visibility is increasingly challenging. ASPM provides a logical response to the growing complexity of CI/CD toolchains, aiming to unify AppSec management under a single platform. It enables security teams to clearly view and assess the security posture of all their application perimeters.
The goal of this article is to briefly go over ASPM’s capabilities, and to confirm whether it is simply another take on vulnerability management or if the paradigm has shifted towards a new unique type of security tool. We will also debunk key factors that businesses should consider when selecting the right ASPM solution.
What is ASPM?
ASPM, or Application Security Posture Management, is one of the latest buzzwords in AppSec. Popularized after Gartner’s May 2023 insight document, ASPM refers to technology that consolidates all application security tools into a single interface. Over the past year, several startups and established AppSec vendors have rebranded or launched proprietary solutions to acquire part of this emerging market.
The definition provided by Gartner is as follows: “Application security posture management (ASPM) offerings continuously manage application risks through detection, correlation, and prioritization of security issues from across the software life cycle, from development to deployment. They act as a management and orchestration layer for security tools, enabling controls and the enforcement of security policies.”
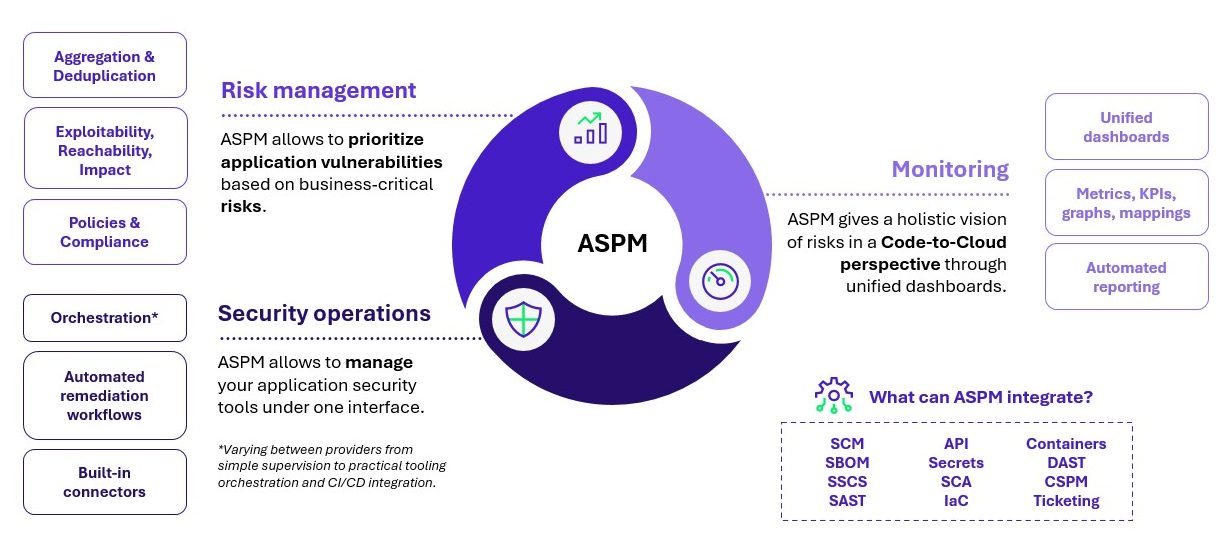
Fig 1 – Overview of ASPM features
The primary value of ASPM lies in delivering scalable security from code-to-cloud. ASPM enhances visibility at every stage by reducing false positives, minimizing alert fatigue, and providing a single source of truth for vulnerability ownership. This is key for organizations overwhelmed by thousands of alerts and struggling to allocate resources for remediation effectively.
How is ASPM unique compared to existing solutions?
Traditional vulnerability management tools aggregate and prioritize security issues detected by scanners. However, they are not exclusive to application security and often span broader IT perimeters in the information system.
If you are familiar with the topic, Application Security Orchestration & Correlation (ASOC) originally marked a shift by focusing specifically on managing application security issues. ASOC offered DevSecOps teams an interface to orchestrate tools and streamline remediation workflows.
ASPM on the other hand can be seen as an evolution of ASOC, extending its scope from simple code security to code-to-cloud. This includes analyzing not just application code but also the infrastructure and resources used in development and deployment. For example, ASPM can assess configurations, container images, and Infrastructure-as-Code (IaC) modules like Terraform scripts.
Other key differences between ASPM and ASOC include:
- Enhanced Prioritization: ASPM prioritizes business-critical risks over simple CVSS-based issues, often leveraging advanced algorithms for triaging.
- Compliance Support: ASPM allows organizations to triage vulnerabilities based on frameworks such as OWASP, ISO, and SOC2, helping organizations achieve compliance.
- Policy-as-Code: ASPM enables organizations to define policies, such as blocking deployments if risk scores exceed thresholds or if code reviews are incomplete.
Decisive factors in choosing a provider
If used right, ASPM can effectively help teams optimize their workflows and remediate security issues faster. Nevertheless, even if all ASPM providers have their own strengths and uniqueness, selecting the right solution is essential since not all of them will suit every organization.

Fig 2 – Non-exhaustive panel of ASPM providers
Each context brings its own unique decisive factors when choosing the right ASPM, some of which include:
- Can this solution integrate the tools I already have? How close to a plug-and-play experience will it be?
- How far can I integrate this ASPM in my CI/CD? How far can it automate remediation workflows?
- Who are the targeted end users? (Security team, Security champion, Devs & Ops)
- Is the ASPM leveraging a custom algorithm for prioritization or rather CVSS, EPSS?
- Is the interface aesthetically pleasing and easy to use? Can I customize it?
- How does the provider handle my data?
- Is the security of the ASPM itself up to my standards? Does it support SSO, MFA, RBAC?
- What is the support level provided by the editor?
- Are the proposed subscription plans adapted to my organization’s needs?
- What is concretely meant by the advertised use of Artificial Intelligence in the solution?
Some things to look out for
DevSecOps maturity
ASPM can therefore be defined as a useful yet somewhat “niche” solution for application security. While it can function as a relatively effective plug-and-play tool, ASPM still requires integration work and fine-tuning by security teams to maximize its potential. Organizations that lack a robust security stack or are still in the early stages of building a DevSecOps pipeline may benefit less from ASPM. For such organizations, focusing on foundational tools and processes before adopting ASPM might be a more practical approach.
Managing false positives and false negatives
One of ASPM’s promises is to reduce false positives, which is a common benefit of vulnerability management. In practice, however, while noise is minimized, it is rarely entirely eliminated. Security teams must still manually triage and address vulnerabilities that the system cannot confidently classify as false positives.
Another critical concern is the potential for false negatives. Some vendors claim their tools “reduce vulnerabilities by 99%”, though, unless the risk-scoring algorithms are fully transparent, there is a risk that genuine security issues might be overlooked. When algorithms classify certain vulnerabilities as insignificant without proper justification, this creates blind spots that could expose the organization to unaddressed risks.
Accordance with teams’ needs
Before committing to ASPM, it is necessary to ensure that the solution fits the organization’s specific requirements. Running a proof-of-concept (PoC) on a small scale— testing the platform with diverse teams operating under different dynamics— can provide valuable insights into its adaptability and usability.
Most ASPM solutions are offered as SaaS platforms, simplifying deployment for PoC and making it easier to evaluate the tool without significant initial investment.
Security
Given that ASPM often has access to sensitive data, such as source code and real configurations, organizations must thoroughly verify that the solution adheres to their security standards. Failure to do so could turn ASPM into a single point of failure within the security stack.
An alternate definition of ASPM?
Vulnerability managers and ASOC in their essence do not aim to incorporate built-in scanners, but simply to aggregate findings from other tools. Similarly, the core value of ASPM as it was defined by Gartner is to manage risk in Code-to-Cloud settings, without meddling in the scanning part, which is left to AppSec and CSPM tools.
However, almost two years after Gartner’s study was released, ASPM has steered towards a direction that somewhat diverges from their initial vision. ASPM providers have started integrating proprietary scanners inside of their solutions so that their customers would not have to acquire third-party ones. A great article from James Berthoty rightfully argues that since Gartner’s definition of ASPM can simply be deemed an evolution of ASOC, there’s no reason to call it anything other than ASOC.
Arguably, the only legitimate reason to evolve from ASOC to ASPM would be a new type of tool aiming to conquer a need of the AppSec market which has not been fulfilled yet: an all-in-one platform for application security. By simply connecting your source code and your environments, this platform would scan everything, aggregate the findings, and simply output the most critical issues and how to remediate them. This could be especially relevant for organizations with no prior security stack looking for a full AppSec solution, whereas those who want to keep their current toolchain may opt for an aggregator version of ASPM instead.
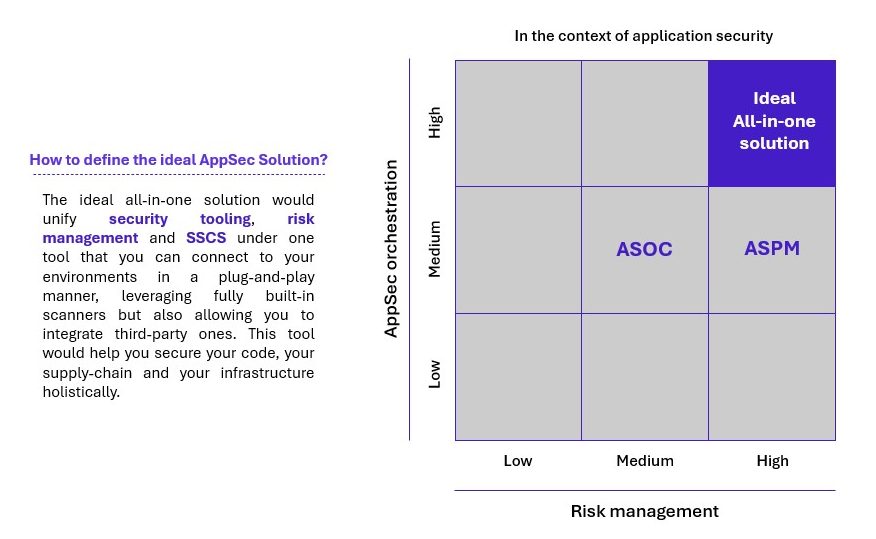
Fig 3 – Defining the ideal ASPM
To conclude
Gartner originally predicted that by 2026, over 40% of organizations developing proprietary applications would use ASPM to manage risks in their applications. While this prediction might be slightly ambitious, the need for better application security tooling and a centralized security management platform is also rising quickly.
To realize its full potential, ASPM must be part of a broader DevSecOps strategy. Organizations need to establish the right processes, governance, and CI/CD foundations to fully benefit from it.


