This article is the first of a series of 2, tackling the implementation of the Enterprise Access Model, an administration model proposed by Microsoft to secure the administration of Cloud environments.
Today, most companies use public cloud to host numerous workloads from business to functional services. Although this brings benefits, the Cloud also introduces new paradigms, which need to be understood clearly in order to be secured.
Historically, enterprises have relied on a 3-tier model for securing Active Directory environments. This model segments the network into three distinct tiers: Tier 0 for highly sensitive systems and data, Tier 1 for server administration, and Tier 2 for end-user workstations and devices. While this model has proven effective in on-premises environments, the shift to cloud-based infrastructures requires a reevaluation of its applicability.
This article delves into a recent, concerning trend: the global compromise of Entra ID, originating from the compromise of a helpdesk account. Such an attack can have severe repercussions, even more so than an AD Domain Administrator compromise. We will explore the mechanisms behind these attacks, their implications, and, most importantly, how we should protect against this kind of privilege escalation and implement an adapted and secured administration model.
Understanding Entra ID, Active Directory, and Azure Permissions
As shown in Figure 1, Active Directory and Entra ID (formerly Azure Active Directory) are two Identity services with different structural properties and IAM protocols. While Entra ID focuses on identity and access management across both cloud and on-premises environments, providing authentication and user management, Azure permissions extend to the broader management of cloud infrastructure and services. Understanding the distinctions and interconnections between these tools is essential for maintaining robust security and effective access control in modern enterprise environments. 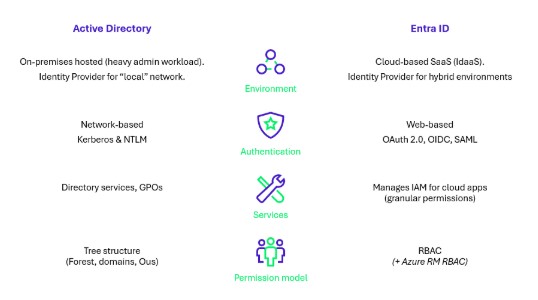
Figure 1: Active Directory and Entra ID key differences
Between Active Directory, Entra ID, and Azure- each manages its own permission model:
- Active Directory uses a unified permission model for all its objects, from users to servers.
- Entra ID uses Role-Based Access Control (RBAC) to manage its tenant’s objects (e.g., users, devices, applications).
- Azure Resource Manager (RM) uses RBAC to manage Azure resources
However, there is a bridge between Entra ID and Azure RM thanks to the single tenant’s relationship to an Azure organization: the Entra ID’s Global Admin role is assigned by default the User Access Administrator role in the Azure RM service. As a result, it can grant itself full permissions in Azure.
Although there is a link between Azure and Entra ID, it’s important to remember that the roles in Entra ID and Azure RM can be assigned independently. For example, a standard Entra ID user with very limited permissions on Entra ID can hold the highest privileges in Azure RM, which is a critical point of vulnerability exploited in attacks.
Privilege escalation in Entra ID can lead to an extensive compromise of Azure RM (including all resources and infrastructures), Microsoft 365, workstations, Windows servers, cloud networks, and more.
The most privileged roles in both systems are:
- Entra ID: Global Administrator
- Azure RM: Owner (which can be scoped from Management Groups down to resources)
These significant differences mean that the concepts from the traditional AD 3-tier model cannot be directly applied to cloud environments. We must rethink and adapt these concepts to ensure they are relevant and effective in cloud-based contexts, particularly by adequately addressing the specific requirements and risks associated with cloud environments.
A real-life global Entra ID compromise
To focus on Cloud Administration compromise and privilege escalation, a small number of hypotheses will be taken:
- The victim has an Entra ID tenant as Identity Provider.
- The victim uses Intune to manage its entire workstation fleet.
- The victim has an Azure subscription for its Virtual Desktop Infrastructure activities.
- A helpdesk account is compromised (the source of the attack is not relevant, but it is important to note that this is a likely scenario that could have been the result of several different compromise like phishing, credential theft, workstation compromise, social engineering, etc.).
1 Compromising a helpdesk account
- Following our last hypothesis, the attacker has gained control of a helpdesk account, that can reset passwords and MFA.
2 Initial Attempt to Reset Global Administrator Account
- The attacker initially attempts to reset the Global Administrator account, seeking the quickest path to becoming the Global Administrator of Entra ID.
- This action is blocked by default by Microsoft. The Global Administrator role is a “privileged role”, and only specific privileged roles are authorized to reset its password or modify its attributes. Microsoft updates here its list of privileged built-in Entra ID roles.
3 Targeting a High-Value Standard User Account
- Restricted to resetting standard Entra ID user passwords, the attacker identifies a user with the username “VDI Admin”, who is the Owner of an Azure RM subscription used for workstation administration services.
- Despite MFA being enabled on the account, the attacker successfully resets both the password and MFA mechanisms, gaining access to the account.
4 Searching the available subscription
- With the VDI Admin password reset, the attacker logs in and accesses the subscription. Through reconnaissance, they discover access to a key vault containing credentials for a service account.
- The service account is identified as having the “Intune Administrator” role in Entra ID.
5 Utilizing Intune Administrator Privileges
- The attacker logs in as the Intune Administrator, gaining permissions related to workstation administration, including the ability to run scripts on any workstation.
- They deploy a script on the Global Administrator’s workstation to extract authentication cookies from the Global Administrator’s browser.
6 Compromising the Global Administrator Account
- The attacker obtains the Global Administrator’s authentication cookies and uses them on their own workstation to impersonate the Global Administrator.
- This grants the attacker control over the entire Microsoft Entra ID tenant, which includes compromising the Microsoft365 tenant, the Azure RM environments, and all other Microsoft cloud-based tools relying on Entra ID.
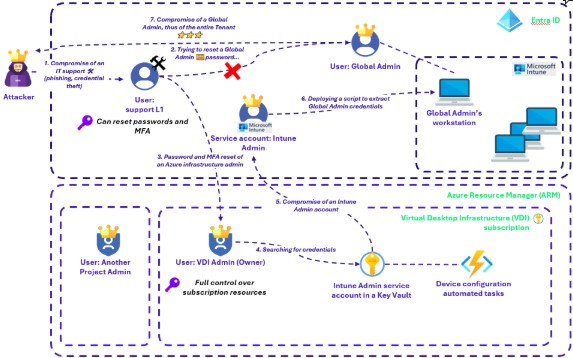
Figure 2: A global Cloud compromise path
By following these steps, the attacker, beyond being able to compromise the entire cloud infrastructure, can deeply affect a company’s business through unauthorized access to emails & documents, backups, endpoints and corporate network. This attack demonstrates the critical importance of securing high privilege accounts that have permissions that could lead to a global compromise.

Figure 3: Impact of a compromise at the Control Plane level
How to ensure this does not happen: Implement the Enterprise Access Model and scope your Control Plane
As discussed in the first part, cloud directories, particularly Entra ID, exhibit key differences from Active Directory. Consequently, the traditional three-tier model requires adaptation to be fully effective in cloud environments. To address these challenges, Microsoft has introduced a new administration framework specifically designed for cloud environments: the Enterprise Access Model.
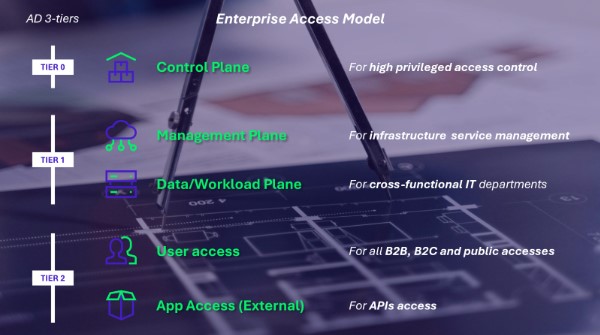
Figure 4: The Enterprise Access Model
While there are some modifications, the core concept remains the same: sensitive resources must be isolated to ensure that a compromise in one plane (formerly tier) does not lead to a compromise in another. This leads us to a crucial question: how should we scope our Control Plane within our Information System to effectively isolate it and mitigate the risks of a global compromise?
The answer lies in identifying the systemic components within our Information System — those whose compromise could lead to a widespread breach. Losing one project is far less critical than a global compromise of the entire Information System.
In our cloud environment, numerous components interact to support projects, from CI/CD infrastructure and deployment pipelines to various IAM tools (such as Identity Providers like AD, Entra ID or Okta, IGA, etc.), along with cross-functional security tools (like EDR, Bastion, and MDM for example). While these are generic components likely present in many systems, there are also numerous environment-specific ones to consider.
We must assess the impact of compromising high-privilege accounts within these components. For instance, if an attacker gains control of a high-privilege account for the CI/CD infrastructure, they could potentially alter the CI/CD processes and/or run a specific pipeline to deploy unauthorized changes in the cloud, which would allow them to gain global access. Thus, these high-privilege CI/CD accounts should be part of the Control Plane. Similarly, consider the EDR solution: if a high-privilege administrator can execute scripts across all workstations, potentially stealing authentication cookies, accessing critical data, or rendering all workstations inoperable, then this high-privilege account must also be included in the Control Plane.
By carefully scoping and securing our Control Plane, we can significantly reduce the risk of a global compromise within our Information System.
Synthesis
As we have seen, the risk of global compromise in a Cloud environment is significant. While cloud computing offers enhanced flexibility, resilience, and cost optimization, it also introduces new paradigms and operational methodologies that must be mastered to ensure security.
The traditional 3-tier model from the on-premises world, particularly from Active Directory, is not suited for organizing administration in the cloud. To address this, Microsoft has introduced the Enterprise Access Model (EAM). This model expands the 3 tiers into five distinct planes, with the most critical being the Control Plane. However, just as with the 3-tier model, isolation measures are crucial in the EAM, requiring the identification of critical components and high-privilege accounts within your Information System as a top priority for cloud security.
The next article in this series will provide concrete examples of attack scenarios that can lead to a global compromise of cloud environments. It will also include security recommendations to enhance cloud administration and prevent such risks from becoming security incidents.
Thank you to Louis CLAVERO for contributing to this article.


