With the European Union’s ban on the sale of combustion engine vehicles set for 2035, the electric mobility market is rapidly expanding. Alongside it, electric vehicle charging infrastructures (EVCI) are developing at a fast pace: cumulative investments by 2030 could reach €50 billion for private chargers and €30 billion for public chargers.
However, unlike traditional gas stations, these are highly computerized and connected systems. Indeed, digitalization allows for a smart ecosystem and direct operational gains. This includes features such as smart charging, which allows for financial and energy savings by optimizing electricity consumption depending on grid strain. The driver’s experience is also improved, as they can use their smartphone to easily locate connected chargers and interact with them.
All these functionalities present specific cybersecurity challenges that we will analyze in this article. We will outline strategies that Charging Point Operators (CPOs) can implement, focusing on public charging stations. Indeed, public chargers are more exposed and thus, are the most complex case study from both operational and cybersecurity perspectives.
What are the cyber risks in the charging ecosystem?
Why are cyber risks significant, and what is their nature? To understand this, we need to examine the charging ecosystem.
The central player in this ecosystem is the CPO, who is on the front line of cyber risks. CPOs are responsible for the direct operation of charging stations, both on-site and remotely. Typically, they use a cloud-hosted software solution called a CSMS (Charging Station Management System).
The role of the CSMS has been highly standardized thanks to efforts by the Open Charge Alliance (OCA), a consortium that developed the OCPP (Open Charge Point Protocol). OCPP handles more than just maintenance and monitoring; it allows the CSMS to communicate with the charger in real-time to manage the charging process (reserving the station, driver authentication and authorization, billing, etc.). This introduces a cybersecurity risk: compromising the CSMS could lead to a widespread compromise of the CPO’s entire charging network.
However, to fully map out the possible risks, we must also consider other industry players who share cyber risks with the CPO.
First, charging stations manufacturers play a key role. Responsible for charger design and production, they also handle software updates and provide patches for vulnerabilities. In some charger models, manufacturers maintain permanent remote access for maintenance purposes via a secondary OCPP connection. If not properly secured, this connection can pose a risk to the CPO.
To ensure the remote connection of charger networks to the CSMS, Wide Area Network (WAN) solutions are frequently used. This can involve a 3G/4G link, or integration into a preexisting on-site network. In both cases, the link is not under the CPO’s control, making them dependent on the cybersecurity maturity of the telecom provider they choose.
Additionally, the CPO must integrate their information system with the site owner. Indeed, chargers can be in a variety of environments: highway rest areas, corporate parking lots, shopping malls, public roads etc. Depending on the use case, the stations may be interfaced with building systems (such as occupancy sensors or smart meters) or with user authentication and payment systems. Typically, the CPO has no authority over these systems and their security.
This multiplicity of actors tends to increase the attack surface on the CPO’s information systems. A breach could result in the leakage of customer data or serve as a foothold for a broader cyberattack targeting the CPO and/or its partners, with significant financial and reputational impacts.
On a local scale, potential attacks are also severe, including cyber-physical risks (e.g.: a malicious modification of charging parameters, which could lead to battery overheating and potentially a fire) or grid destabilization risks (e.g.: the malicious activation or deactivation of multiple chargers at once, potentially overloading the power grid).
These scenarios are likely to become more plausible with the growing popularity of extreme fast chargers (especially for heavy-duty vehicles) and bidirectional charging implementations, which allow parked vehicles to feed stored energy back into the grid.
Implementing new standards: is it enough to address the risks?
As the charging market rapidly grows, it is becoming more structured, and new standards are emerging. This presents an opportunity to provide a unified cyber response to the risks we have discussed.
Take ISO 15118-20, for example. Published in 2022, it specifies robust communication mechanisms between vehicles and chargers. In addition to the already mentioned smart charging and bidirectional charging use cases, ISO15118 introduces Plug & Charge: this feature allows the charger to automatically authenticate a vehicle and process payment, eliminating the need for payment cards or RFID tags.
The primary goals of ISO 15118 are thus to streamline usage, improve energy efficiency, and ensure interoperability. However, its adoption could also bring security benefits, notably through the implementation of a global Public Key Infrastructure (PKI) for charging stakeholders: vehicle manufacturers, mobility operators, and CPOs.
Meanwhile, the development of OCPP is also expected to accelerate, following the official approval of OCPP 2.0.1 as an international standard (IEC 63584) by the International Electrotechnical Commission.
However, it will take time before these standards become widely adopted. Several major players, such as Tesla, have developed proprietary protocols with similar features. Moreover, most existing chargers and vehicles are not compatible with ISO 15118 or OCPP 2.0.1 and need to be replaced.
Thus, we cannot rely solely on standards to address cybersecurity risks: it is imperative to find ways to secure current infrastructures.
Note : to know more about Plug & Charge and smart charging, feel free to check out the articles by EnergyStream, Wavestone’s energy blog (only available in French):
- Le Plug & Charge : une nouvelle solution d’authentification et de facturation sécurisée
- Les défis du déploiement du Plug & Charge
- Panorama des usages du smart charging
So, how can CPOs secure their architecture?
Standards are only one part of the puzzle: it is primarily up to CPOs to implement a comprehensive cybersecurity policy. But how can they tackle the complex risks we have discussed?
The first step is to understand and document their architecture and solutions. This may seem basic, but there is currently no reference architecture model for charging infrastructure. In this article, we will be model the architecture using four zones, as presented below:
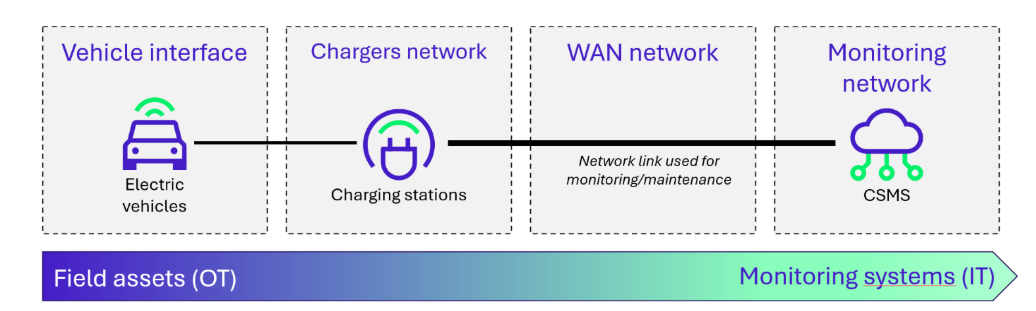 Figure 1. Base architecture model for public chargers in commercial contexts.
Figure 1. Base architecture model for public chargers in commercial contexts.
To secure this architecture end-to-end, we will look at key measures to secure each zone.
We can, however, disregard the vehicle interface for now. Until ISO 15118 becomes widely adopted, current charging connectors are not integrated into the information system and therefore are not a risk vector.
For the charging network, cyber hygiene measures and network segmentation are crucial. Chargers are often vulnerable systems, due to the use of default accounts, weak passwords, open network ports, and unencrypted storage systems. The CPO must implement best practices for hardening and firmware updating, for each manufacturer and model they use.
Network segmentation usually involves the use of firewalls and VLANs, depending on the local network topology and external systems that need to be integrated. Using a local controller can help isolate chargers more easily from untrusted networks. This controller can aggregate all charging stations on a site and serve as a proxy with the CSMS.
As the WAN network is often outsourced, it is essential for the CPO to encrypt the flows between the chargers and the CSMS. The main existing solution today is the use of TLS with server-side and client-side certificates, as provided in the latest versions of OCPP.
Finally, how to secure the CSMS? It can generally be assimilated to a cloud-based IoT platform and approached similarly. Priority should be given to code security best practices and proper identity and access management (following the RBAC model). In the future, we can imagine that the CSMS will also play an active role in detecting cyber threats: analyzing logs and OCPP communications could be facilitated by the implementation of AI-based solutions.
Conclusion: what should be the reference architecture for CPOs?
Although new standards promise to streamline architectures, the charging ecosystem remains complex due to the diversity in business contexts. This is why we encourage CPOs to adapt the best practices from this article to their use case. The architecture diagram below should be seen as a starting point, rather than a definitive target.
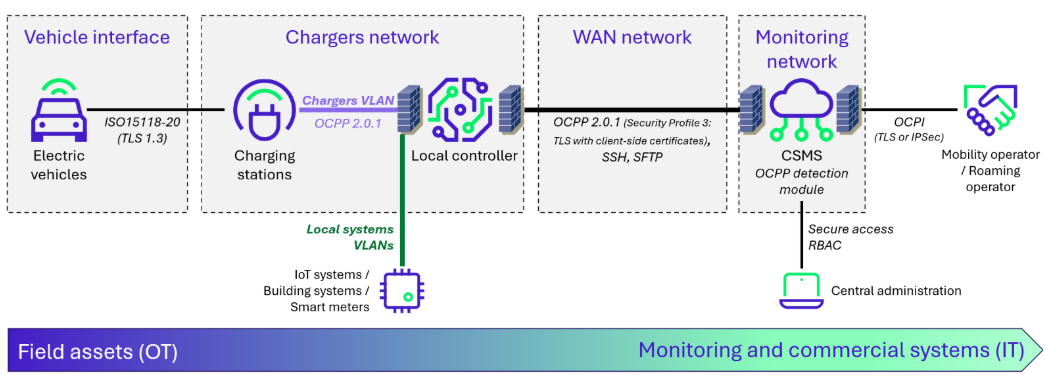 Figure 2. Secure architecture model for public chargers in commercial contexts.
Figure 2. Secure architecture model for public chargers in commercial contexts.


