The Cyber Resilience Act (CRA) represents a significant step forward in ensuring the cybersecurity of products with digital elements within the European Union. As digital products increasingly integrate into every aspect of daily life, ensuring their security becomes paramount. The CRA thus represents a steep change in the security of products as the first regulation of this kind worldwide. Wavestone, as a key player in cybersecurity consultancy, is particularly invested in this regulation due to its involvement in the exploratory studies that shaped the CRA.
In a few words, if you either manufacture, import or resell a product with digital elements, you will surely be affected by the CRA, and need to ensure compliance. This article is intended to shed light on: What does this regulation entail? Who is affected? How can compliance be achieved?
What is the cyber resilience act and what does it entail?
To understand the necessity of the Cyber Resilience Act, it’s crucial to consider the broader context of cybersecurity in Europe. The CRA is an ambitious regulation designed to ensure the security of EU citizens by addressing the currently observed low levels of cybersecurity in products with digital elements through a European Union policy intervention. In response, comprehensive studies focusing on the cybersecurity of digital products were conducted, leading to the proposal of legislation defining the obligations for the whole products supply chain actors, from manufacturers to distributors.
Wavestone’s involvement in this process underscores its commitment to enhancing cybersecurity standards. We participated in an in-depth exploratory study commissioned by the EU, engaging with a broad spectrum of stakeholders involved to varying degrees in the products ecosystem, including national authorities, EU bodies, hardware and software manufacturers, trade associations, consumer organizations, researchers, academia, and cybersecurity professionals.
Through Wavestone’s position as a global, and particularly European leader in the field of cybersecurity, several interviews, focus groups and workshops were conducted. Valuable insights were gathered from a wide range of different interlocutors, providing a comprehensive view that takes into account the perspectives of all stakeholders and allowed the foundation for the development of the CRA.
Definition and Scope
The Cyber Resilience Act is a legislative proposal defining the obligations of manufacturers, importers, and distributors of products containing digital elements marketed in the EU, all of which must bear the CE mark across all sectors. As defined in the regulation, this includes “any software or hardware product and its remote data processing solutions, encompassing components that can be marketed separately”. The regulation’s aim is not only to secure standalone products but also to ensure the security of data transmission chains and central infrastructures through the application of this standard.
To this notion of product is added a notion of criticality, therefore the CRA differentiates two types of products: products with digital elements and critical products with digital elements. As detailed below in “Checklist for CRA compliance”, it will affect how compliance can be achieved.
A few examples of products with digital elements include consumer products, smarts cities and non-essential software. Critical products with digital elements include for example industrial control systems and firewalls. The detailed list of concerned products can be found in the regulation’s annexes.
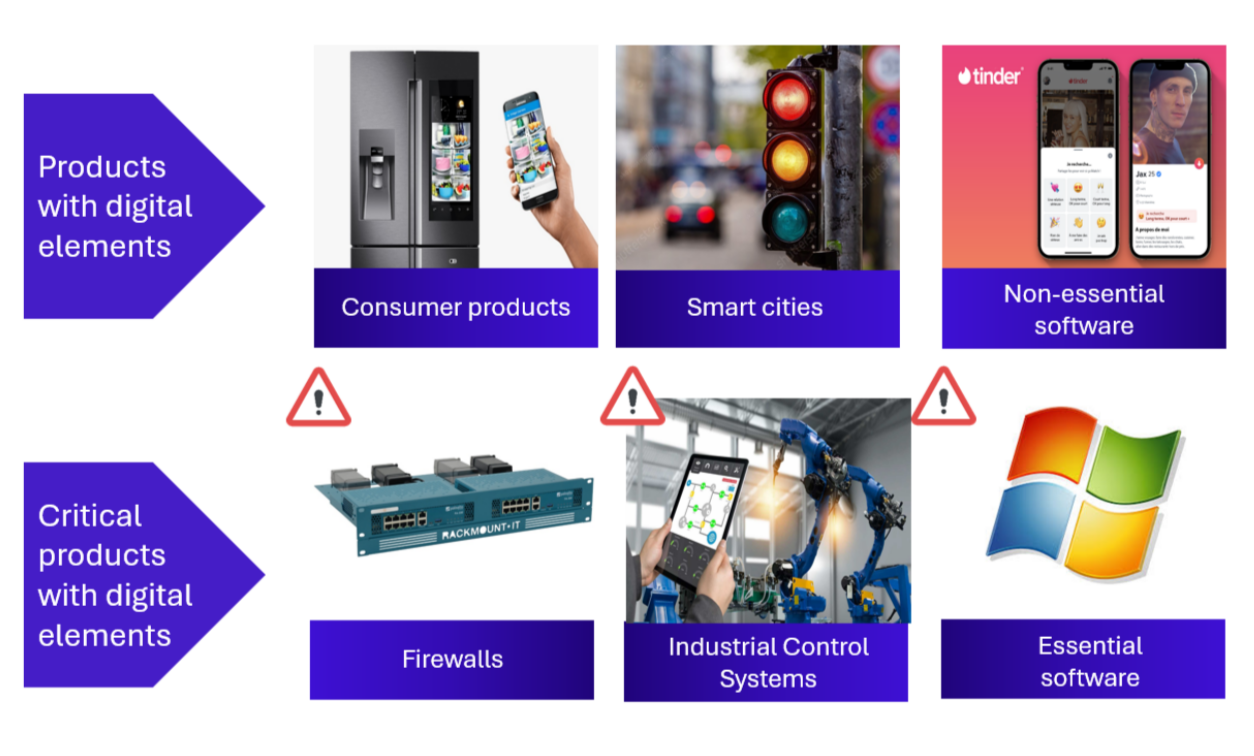 However, as is detailed below in “A complex ecosystem”, the CRA does not apply universally; products in some specific sectors do not have to comply to the requirements
However, as is detailed below in “A complex ecosystem”, the CRA does not apply universally; products in some specific sectors do not have to comply to the requirements
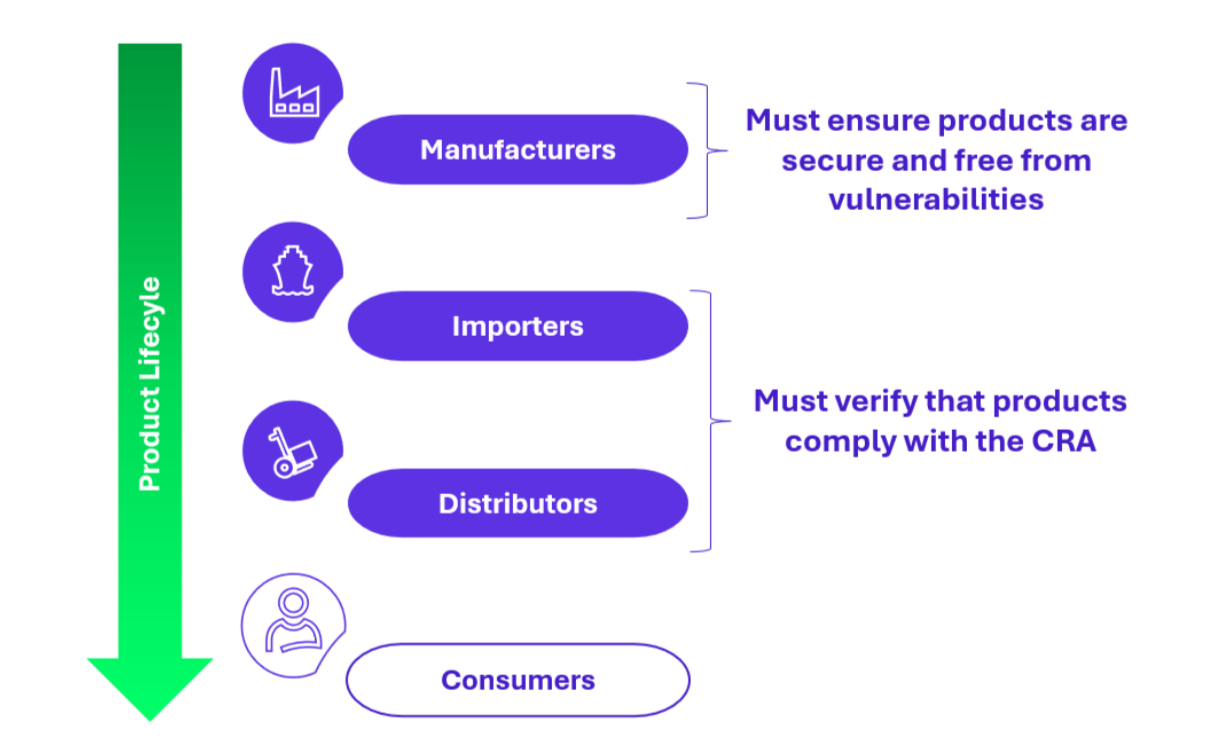
Stakeholders and Responsibilities
The CRA impacts the entire lifecycle of digital products, from development by manufacturers, importers, distributers to the final consumer, but also the vulnerability management from conception to the product end-life, through a share responsibility.
Essential Requirements
As said earlier, the CRA’s objective is to allow a sufficient level of cybersecurity in products with digital elements. To do so, it introduces essential requirements built on three pillars:
- Product Security: Ensuring products are designed, developed, and manufactured to meet appropriate cybersecurity levels and are free from known exploitable vulnerabilities.
- User Documentation: Providing documentation to ensure safe use from commissioning to end of life.
- Vulnerability Management: Identifying and documenting vulnerabilities, conducting regular security tests, and implementing a vulnerability disclosure policy.
In the event of non-compliance with the essential requirements, sanctions may be applied on any of the three stakeholders. Like GDPR, each Member State shall determine the penalties applicable to infringements of this Regulation. Penalties are based on the company’s annual turnover and the severity of the infraction, with fines reaching up to 15 million euros or 2.5% of the total worldwide annual turnover for significant breaches.
How to achieve compliance with the CRA?
Timeline of the CRA
The CRA has been a long-term project, with almost 10 years from identification of the need to application, reflecting the complexity of establishing comprehensive cybersecurity regulations:
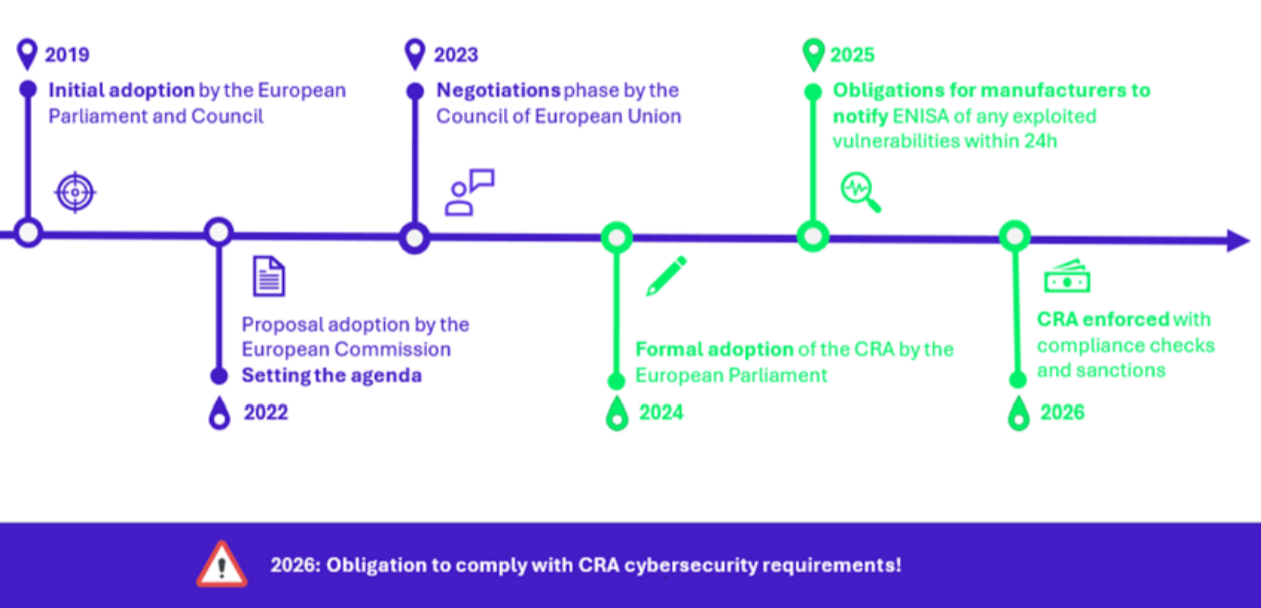
Businesses have until the 2026 to achieve compliance, with interim obligations. Similar requirements can be found in other regulations, such as NIS2, but contrary to other regulations, the CRA does not need a national transposition. The CRA was passed by the European Parliament in March 2024, and it is awaiting a vote by the European Council to become a law.
A complex ecosystem
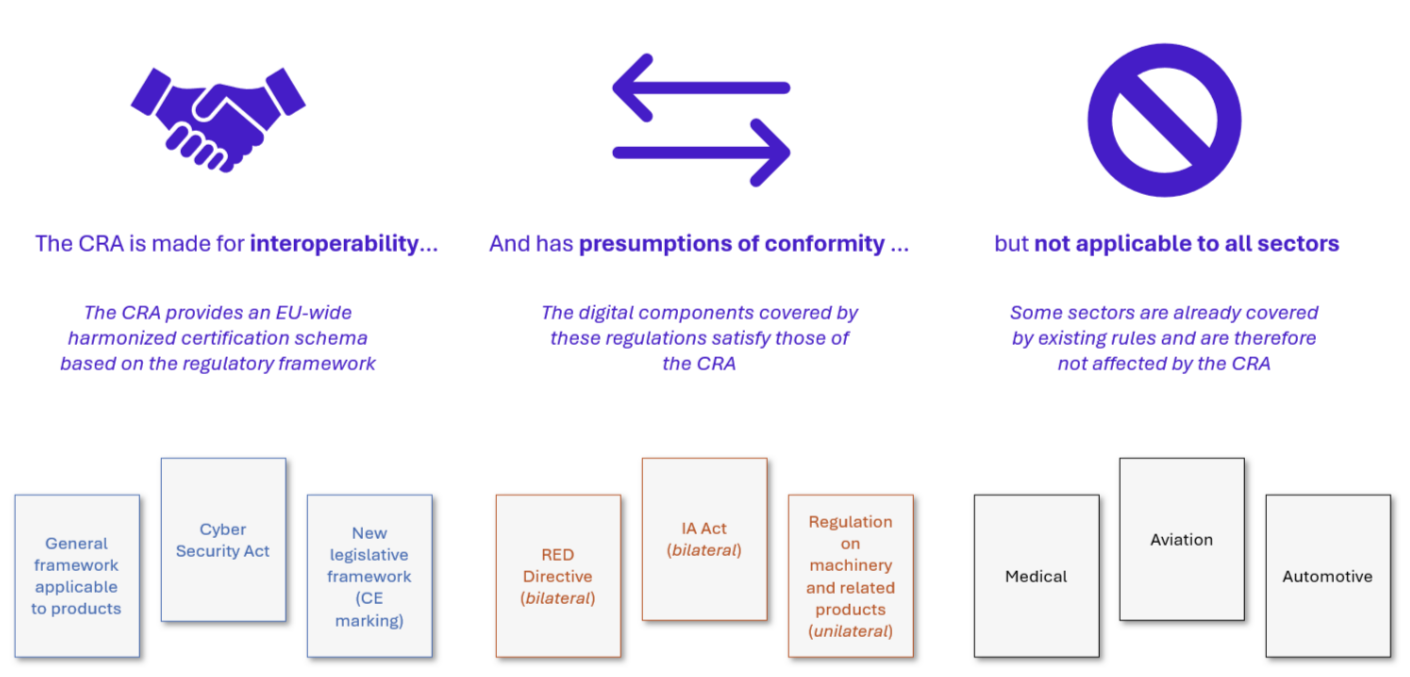
One of the major concerns raised during the preparation of the Cyber Resilience Act was how to navigate the multitude of existing regulations and achieve regulatory harmony, particularly in sectors where safety, privacy, and cybersecurity standards intersect.
The CRA aims to foster interoperability by aligning with the general product safety framework, the Cyber Security Act’s requirements for ICT products, processes, and services, and the CE marking standards for European compliance.
To streamline compliance, the CRA includes presumptions of conformity with existing regulations such as the RED Directive, the AI Act, and certain sector-specific rules.
However, the CRA does not apply universally; some sectors, such as medical, aviation, and automotive, are already governed by established regulations and are thus exempt from the CRA’s provisions.
Checklist for CRA compliance
Compliance with the CRA involves a thorough understanding of the regulation’s core text and two annexes, which detail: the list of concerned products, essential requirements, the obligations for manufacturers, importers, and distributors and national competent authorities and sanctions.
The certification process varies based on product criticality:
- For non-critical products : a self-assessment is necessary
- For critical products : third-party assessment is necessary, meaning the product compliance to the CRA will be assessed by a certified entity. At the time of writing this article, the exact certification schemes have yet to be specified but in France, the CESTI certification is in discussion.
Five main checkpoints are to be considered to achieve compliance:
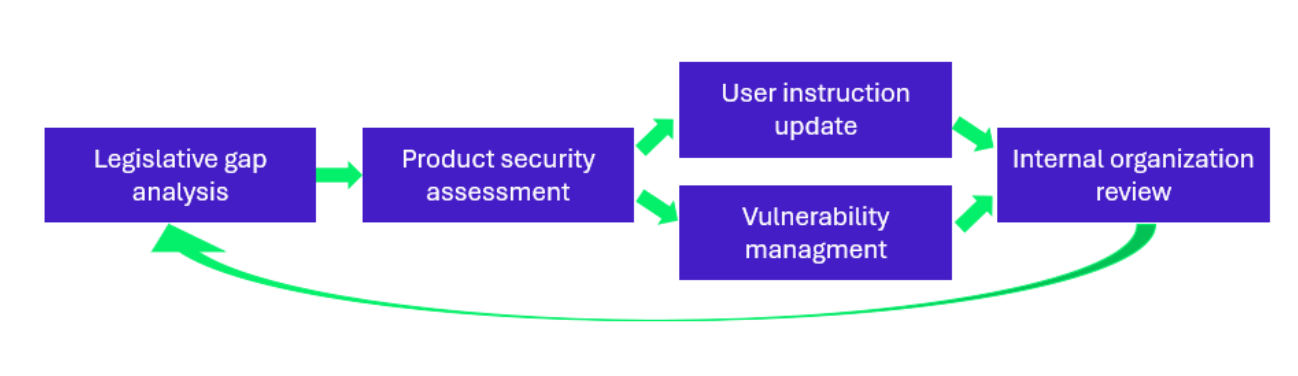
- Legislative Gap Analysis: Identify discrepancies between current practices and the requirements of the CRA by reviewing existing cybersecurity policies, processes, and controls to pinpoint areas needing improvement.
- Product Security Assessment: Conduct thorough assessments to ensure product identification and security.
- User Instructions Update: Provide clear and comprehensive user documentation by ensuring that all products are accompanied by documentation in adequation with the regulation standards.
- Vulnerability Management: Set up a process for identifying and sharing vulnerabilities.
- Internal Organization Review: Implement a permanent procedure to ensure compliance, covering the above-mentioned key points and enforce a watch on product or legislation changes that may imply new gaps to remediate.
In conclusion, the Cyber Resilience Act represents a comprehensive framework to enhance the cybersecurity of digital products within the EU. Compliance with this legislation requires thorough preparation. For businesses, adhering to the CRA is not just a legal obligation but also an opportunity to enhance their standing in a market increasingly aware of cybersecurity issues.


