The IAM market has considerably matured as it relates to its coverage of classic “employee” use cases and is increasingly focusing on the “customer” perimeter- both on the part of IAM solution vendors and the companies deploying them. Over the past few years, however, new use cases have emerged that do not fit into either of these two categories resulting in the increasing openness of information systems to different types of partners (suppliers, subcontractors, etc.). Market players refer to these new use cases as the ‘extended enterprise’.
IAM solutions on the market don’t always adequately cover these emerging needs and companies haven’t found the right approaches and governance modes to address them. More often than not, these use cases are managed on a case-by-case basis, without any IAM solution or common global governance.
What is the extended enterprise?
The extended enterprise is a group of entities and economic players working together on common projects. Companies have always needed to collaborate by sharing resources and exchanging data. To achieve this, the employees of each of these companies need to be able to interact securely with external users.
These external users can be suppliers, subcontractors, B2B customers, subsidiaries (that do not share the same IS), and so on. Collaboration can take many forms and can be time limited.
Because of this diversity of scenarios, it is neither possible nor relevant to define a single answer to every IAM project for the extended enterprise. The strategy to be adopted by any company wishing to address this issue will depend on its own context and specific use cases.
An extended enterprise IAM strategy can be initiated by answering two key questions: how should IAM governance and delegation be handled with the various partners? And, what type of solution on the market best covers these use cases?
What type of governance?
There are 4 main approaches to IAM governance in the extended enterprise. The choice of one of these approaches will depend mainly on two criteria: the level of IAM maturity of the various stakeholders and the sensitivity of the resources accessed.
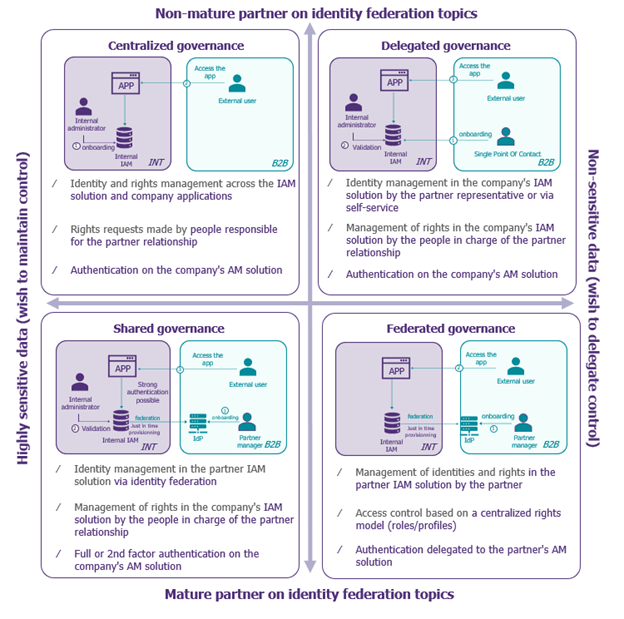
Which vendor’s solution?
A number of functionalities clearly distinguish CIAM editor solutions (customer scope) from Workforce IAM solutions (employee scope). These two types of solutions are at opposite ends of the spectrum referring to the criteria analyzed in the diagram below.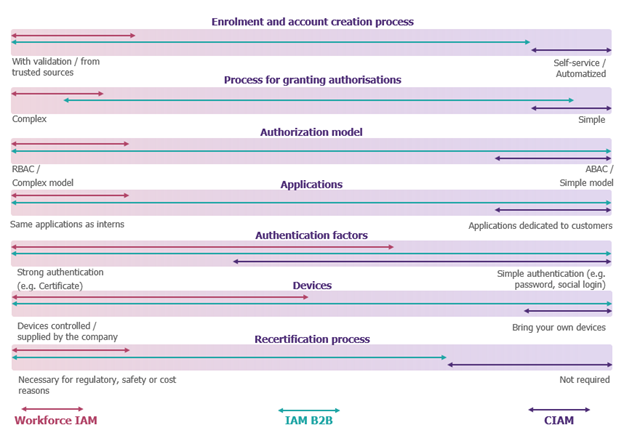
Extended enterprise (B2B) use cases can be positioned over a wide range of this spectrum for each criterion, depending on the context. It is therefore difficult to respond to them with traditional workplace IAM or CIAM solutions, however more and more software publishers are offering new dedicated modules to meet these new needs.
What new technologies to facilitate implementation?
One of the key factors in the success of an extended enterprise project is the ability to decentralize IAM processes and mechanisms. The technological advances presented in the table below make it possible to rethink traditional approaches to identity and access management from this angle. They offer more flexible solutions, adapted to the diversity of use cases encountered, thus enabling greater decentralization, particularly with less mature partners, thanks to identity wallets and passkeys:
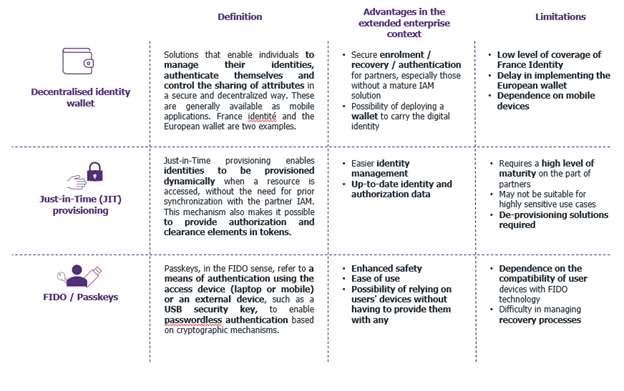
In this quest for solutions adapted to a wide range of use cases, it is imperative to keep abreast of market developments and constantly assess the relevance of proposed solutions to the specific needs of each context.


