This article is intended primarily for an informed public, mastering the use of cryptographic keys in an IS and their management in organizations.
Increasing security requirements for both industrial environments and connected objects have led to a profusion of cryptographic keys in companies that are sometimes difficult to manage. These are used to encrypt and decrypt documents and exchanges as well as to verify the authenticity of messages and files, for example, when updating a component’s software, to ensure its integrity.
One solution, to the problem of the complexity of managing numerous cryptographic keys within a company, is to implement a KMS (Key Management System). This tool helps protect data, product, and process security in the form of a centralized cryptographic key management tool.
Beyond standardizing processes, the KMS can help solve problems such as the generation of large numbers of different keys, key storage and access, and key depreciation.
Why use a KMS?
KMS (Key Management Systems) are cryptographic key management systems that allow companies to manage their encryption keys centrally and securely. KMSs are designed for organizations managing a large number of cryptographic keys and improve the security of their environments by standardizing processes and providing APIs for crypto functions (signature, encryption, decryption). Organizations with large IT networks and those in the industry with connected objects such as sensors, actuators, embedded systems, or selling connected products are also particularly concerned.
The importance of good key management is crucial to cybersecurity. Encryption, signature, or verification processes are essential for many organizations, even if they sometimes appear transparent to operational staff. It is important that encryption keys are optimally managed, to avoid, for example, insecure key storage or the use of the same key for multiple devices.
This article will take a closer look at what a KMS is, how it works, and why it may become essential. Several types of KMS will be presented, as well as the advantages of using them and the difficulties of integrating them. Finally, this article looks at some of the keys to targeting companies that can benefit from this type of tool.
To get more information on the KMS architecture, you can watch Paul Chopineau conference at the Miami S4x24 https://youtu.be/J5aeAYxcc24?feature=shared.
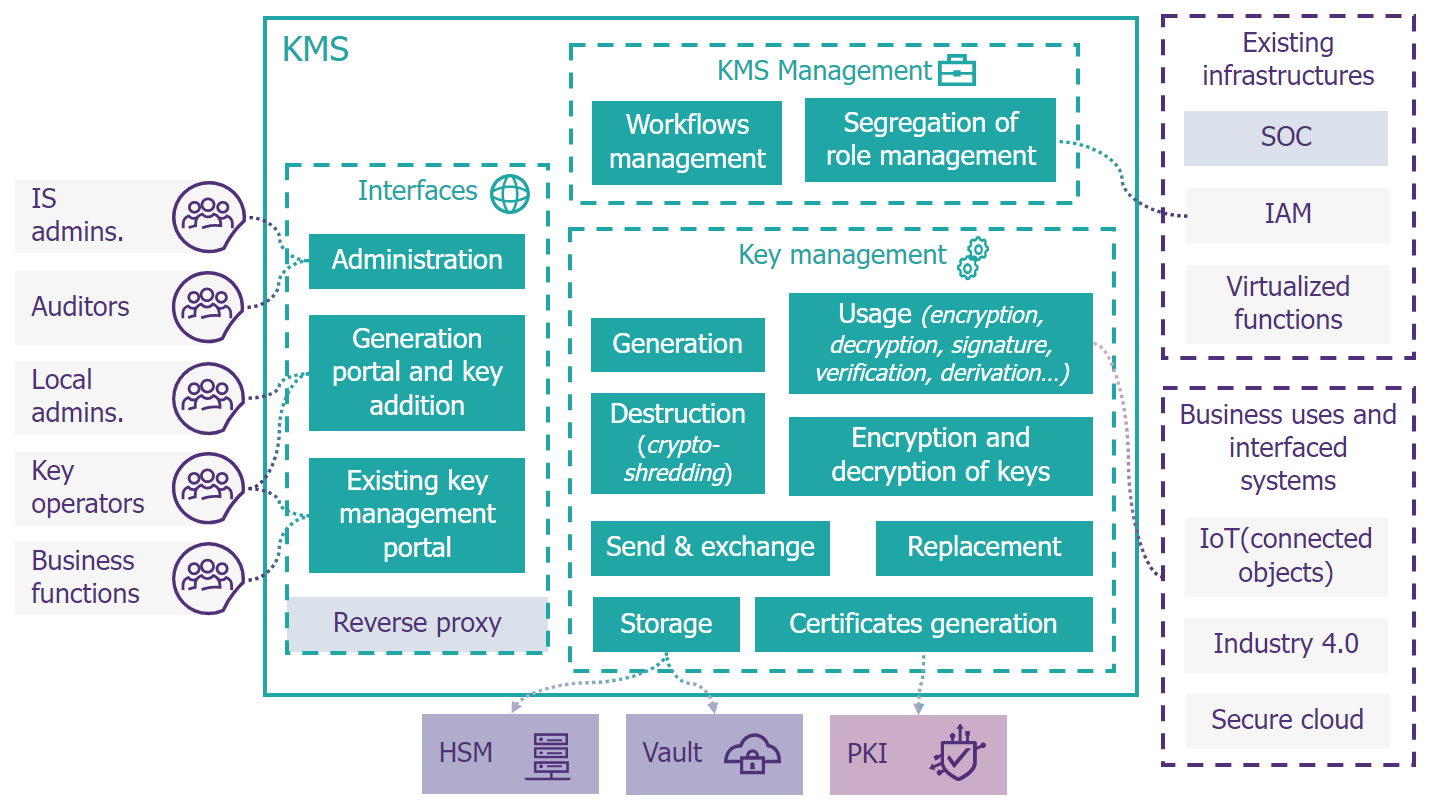
Figure 1 : Typical KMS architecture
The different ways to deploy a KMS
There are several ways to implement a KMS depending on the options offered by the manufacturer. Some Key Management Systems are offered in SaaS mode while others can be installed on the company’s servers (on premise) or in a hybrid mode- where the keys are stored on premise, but the application is in the cloud.
Implementing KMSs through cloud solutions enable encryption keys to be managed from a computer or server. These products are more scalable and agile, and easier to deploy and update. Key security, however, will depend on that of the cloud service, even if it is possible to introduce over-encryption.
On-premise KMS are software and hardware solutions that enable cryptographic keys to be managed using an organization’s internal servers and HSMs. They are generally more customizable and sometimes better adapted to specific needs than KMS deployed in SaaS mode. On premise KMSs, however, take longer to integrate and cost more to purchase (initial CAPEX). They also have the advantage of enabling a company to ensure sovereignty over its cryptographic keys. On premise KMSs are therefore best suited to companies with very stringent security requirements and a greater capacity for initial investment.
Finally, hybrid KMSs could represent the right balance between optimum security and ease of deployment. The aim is to retain control over the keys, which in this case are stored on site, but to benefit from greater ease of deployment and scalability thanks to a cloud-hosted application. Deployment of the application is made easier, but the hardware resources for key management (HSMs) still need to be installed. A hybrid KMS includes key security approaches of an on-premise solution with software that makes it dependent on the cloud service. Care must be taken, however, to protect against fraudulent exploitation of keys from cloud infrastructures, which could be more difficult to detect than with an on-premise KMS.
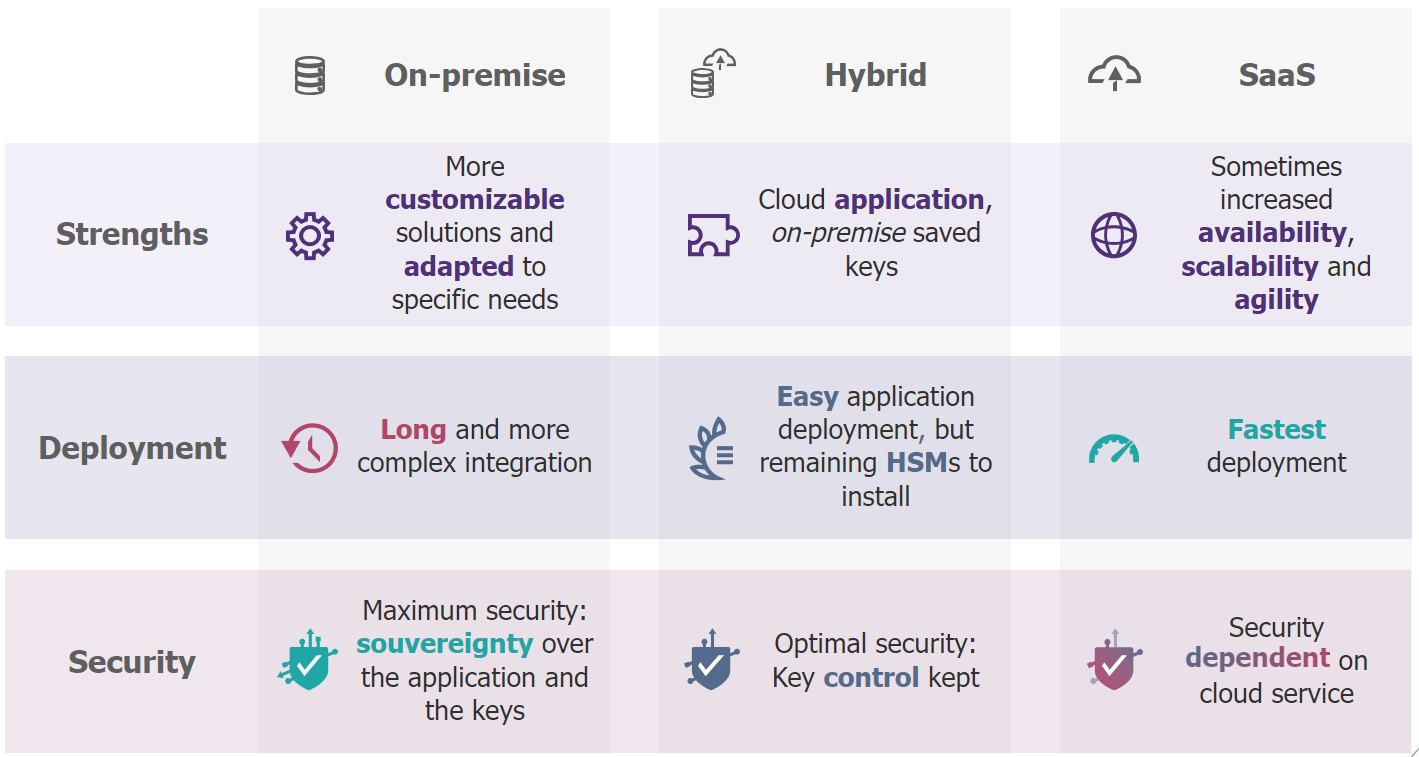
Figure 2 : The three possible implementations for a KMS
It is also possible to classify products on the market according to provider type.
Firstly, there are the products of the major cloud players:
- Amazon with AWS Key Management Service (AWS KMS),
- Microsoft which offers Azure Key Vault,
- Google with the Cloud KMS (Key Management Service),
- IBM which offers a KMS (Key Management Service) integrated into IBM Cloud Private.
Their products integrate perfectly with the services provided by these major providers, including their secure key storage tools, such as Google’s KMS, which enables keys to be created in the cloud and stored in HSM.
Specialized companies are also positioning themselves in the market:
- Cryptomathic with its CKMS (Crypto Key Management System),
- Entrust, whose product is called KeyControl,
- HashiCorp, with its product Vault,
- Utimaco, whose KMS is called KeyBridge,
- Thales, for example with its Trusted Key Manager (TKM).
In particular, these companies offer to run their tools on software resources, such as KMS from Microsoft, Amazon, and Google for HashiCorp; or VMware for Entrust. But also, hardware resources, such as HSM, which provide a superior level of security against physical attacks.
Finally, the market has also been joined by integrators, such as Atos with its Trustway DataProtect KMS suite, designed for on premises installation on company hardware.
Finally, Thalès, which positions itself as a hardware provider, publisher, and integrator, offers several key management products for companies. These work in tandem with those offered by more specialized players, as well as with their customers’ preferred cloud services.
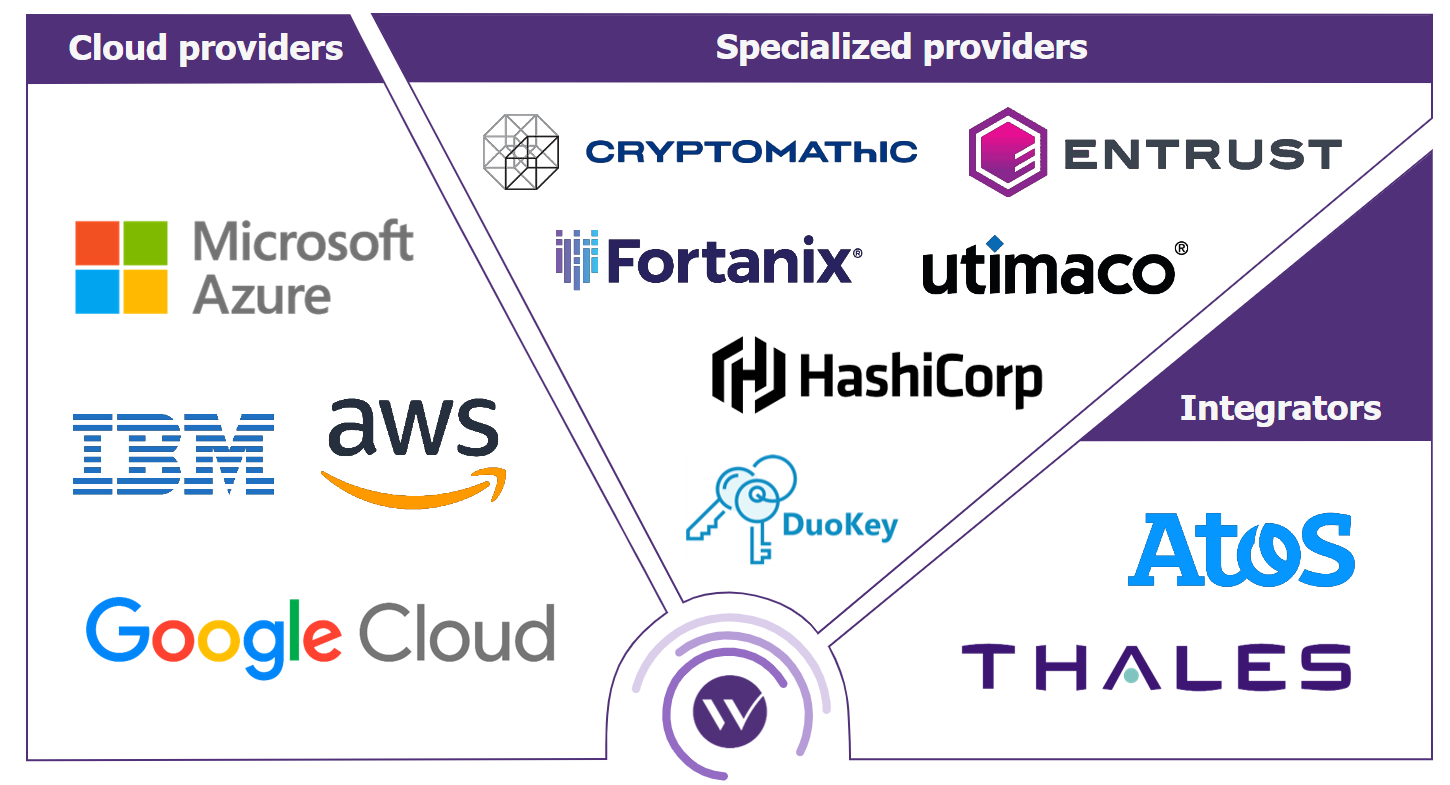
Figure 3: Three main types of KMS providers
The advantages of using a KMS
KMS (Key Management Systems) are tools whose full potential has still to be explored, of which can prove particularly useful for managing a company’s encryption keys centrally and securely. Here are just a few of the advantages of using KMSs.
Firstly, keys will be easier to deploy. KMS enables new cryptographic-encryption keys to be generated quickly and automatically, which is particularly useful when many different keys need to be generated for transmission to products, connected objects or industrial systems.
In a context where connected object keys are often not renewed and are managed in a non-standardized way, KMS will enable companies to introduce the level of security that will enable them to comply with future regulations on IoT systems. The same applies to the encryption of sensitive data in a database, which is the use case that gave rise to KMS products in the first place.
To improve key storage and access, KMS offer centralized APIs and interfaces, integrating permissions management with identity and access management (IAM), which can be particularly useful for companies with many types of keys and users of encryption keys. The challenge will be to convince providers and partners outside the company to enter keys via the KMS. This will be an element to be negotiated in future framework contracts.
KMS also enables one to manage the depreciation of encryption keys, automatically replacing them with new ones when they expire, are compromised or simply become obsolete, for example following a change in the security policy. This ensures that data remains secure at all times.
In short, KMS are invaluable tools for efficiently and securely managing a company’s encryption keys. They improve compliance with regulations and security standards by ensuring that key management procedures and the keys used comply with established standards.
Traps to avoid when implementing a KMS
Setting up a KMS (Key Management System) is a major undertaking, which can be hampered or even halted by the following factors:
- Deployment costs: KMS can be very costly to deploy. These include license fees, as well as hardware resources such as HSM for key storage, which need to be sized according to usage (frequency of access, volume).
- Complexity of implementation: setting up a KMS can be complex, especially for companies with a large number of encrypted devices or systems, for whom it will be of high added value. Setting up a KMS can be complex, particularly for companies with a large number of encrypted devices or systems, for whom it will add considerable value. Numerous integrations may need to be set up to communicate with the KMS API, depending on the different use cases.
- Specific change management procedures: it will sometimes be difficult to convince all the company’s users of the importance of implementing a KMS, and to encourage them to use this tool effectively. To solve this problem, a communication and training strategy is needed to make users aware of the importance of encryption key security and the usefulness of the system.
- Skills that are rare on the market: IT architects, cryptography specialists, or project managers capable of managing large-scale cybersecurity projects. These are all profiles that are hard to source, and which will be all the more numerous to recruit the more cryptographic keys are used within the organization. Calling on external expertise will therefore be highly profitable and difficult to avoid.
KMS, an essential solution for secure encryption key management
In conclusion, KMSs are an essential solution for securely managing a company’s encryption keys. Whether a large enterprise with a large number of encrypted devices or systems, or a small business with similar issues, a KMS can greatly help to centralize and secure crypto key management.
As an example, take the case of a freight company. It must manage numerous components in its vehicles, such as sensors to ensure compliance with the cold chain, or simply devices for tracking products. These objects connect to public or corporate networks, transmit encrypted data, and are regularly updated. Firmware must therefore be signed when an update is deployed, and encryption keys for data transmitted by sensors must be securely stored to ensure their integrity and confidentiality, as well as being available to operators in the event of a sensor modification. The KMS is particularly useful for all these processes, both to automate them and to facilitate the work of operators, and to ensure that each person involved only has access to the keys he or she uses. The tool will take care of key generation, or key recovery, if the keys have been generated externally, and then all the other stages in the key life cycle.
It should be noted, however, that assessing the suitability of this technology needs to be taken seriously. Upstream studies and a tendering procedure will be necessary to ensure that the right tool is put in place. By carrying out these procedures with a precise vision of business uses, the company can be sure of not having to change its system later on.


