In late October 2023, a third-party data breach incident sent shockwaves through the business world, affecting over 57,000 entities engaged in business with Bank of America. This breach exposed sensitive personal and financial information, underscoring the pivotal role that third-party suppliers play in an organization’s cybersecurity infrastructure.
These incidents, commonly referred to as “supply-chain attacks”, involve targeting an organization’s downstream third parties (e.g., partners, vendors) to gain access to valuable systems. In the Bank of America case, the compromised third party responsible for this breach, was Infosys McCamish Systems (IMS), an insurance process management services provider.
This breach resonates with the infamous SolarWinds cyberattack, where Nobelium hackers inserted malicious code into the SolarWinds Orion platform, enabling them to infiltrate numerous government systems, including the U.S.’ Homeland Security, State, Commerce, and Treasury, as well as private systems worldwide.
As corporate IT architectures are arguably a mere reflection of a company’s intricate web of business relationships, these events serve as a stark reminder that organizations are not isolated entities but rather hubs of interconnected and co-dependent partners and third parties. Achieving a robust cybersecurity posture requires more than individual efforts; it demands cultivating a secure ecosystem of thoroughly vetted trusted partners to effectively safeguard the entire supply chain required for product delivery (TPRM).
However, building such an ecosystem poses challenges. Many companies lack the resources to exclusively select leading, cutting-edge, and trusted third parties or may lack the leverage to demand transparency from existing partners.
Drawing lessons from the SolarWinds cyberattack, and amid heightened geopolitical tensions (see Chinese cyberattacks on U.S. infrastructure at an unprecedented scale), the Department of Defense recognized this challenge and responded with the development of a solution for securing the supply-chain ecosystem of the Defense Industrial Base (DIB) called the CMMC.
The Cybersecurity Maturity Model Certification (CMMC) is a comprehensive framework designed to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI), that is shared with contractors and subcontractors of the Department of Defense (DoD) through acquisition programs.
The CMMC 2.0 Proposed Rule Release, published on December 26, 2023, represents the latest evolution of the CMMC cybersecurity model, poised to supplant the preceding CMMC 1.0 with a more pragmatic approach. Following its release, the proposed policy underwent a 60-day open-comment period, which concluded on February 26, 2024. The new regulation is anticipated to be finalized by late 2024 or early 2025.
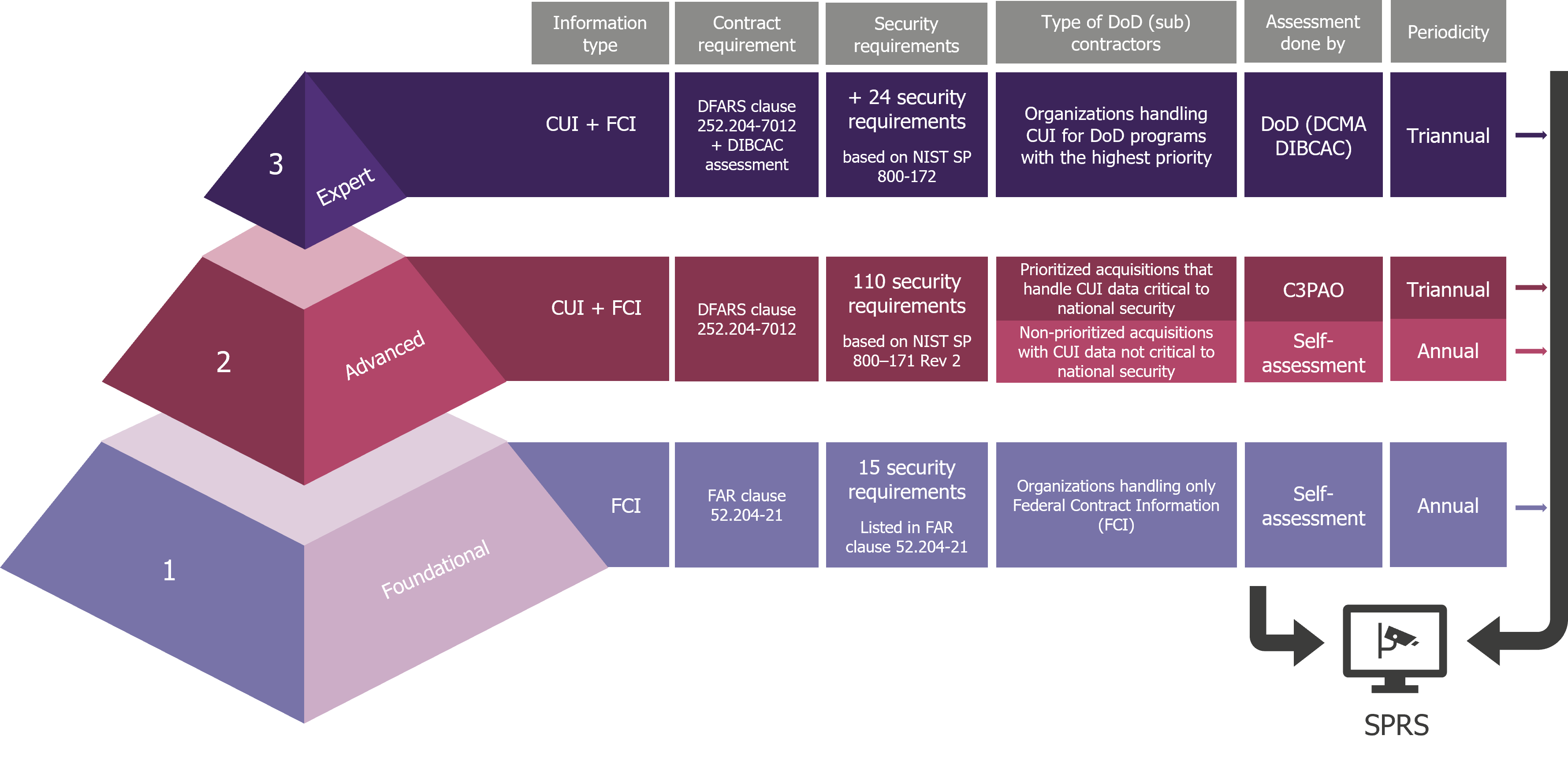
The CMMC 2.0 is aimed at safeguarding sensitive national security information by protecting the Defense Industrial Base’s (DIB) sensitive unclassified information from frequent and increasingly complex cyberattacks. It streamlines requirements to three levels of compliance and aligns the requirements at each level with well-known and widely accepted NIST cybersecurity standards. The specific security requirements and assessment types (self-assessment, third-party assessment, or DoD assessment) vary based on the level.
- Foundational (Level 1): Targets organizations handling FCI (e.g., contract performance reports, organizational charts). Compliance mandates strict adherence to the 15 security requirements outlined in FAR clause 52.204-21, through an annual self-assessment.
- Advanced (Level 2): Targets organizations handling CUI, including Controlled Technical Information, DoD Critical Infrastructure Security Information, Naval Nuclear Propulsion Information, and Personally Identifiable Information (PIIs). Compliance requires adherence to 110 security requirements based on NIST SP 800-171 Rev. 2. Assessments are conducted by third-party organizations known as CMMC Third Party Assessment Organizations (C3PAO) tri-annually or through an annual self-assessment, depending on the sensitivity of the underlying CUIs.
- Expert (Level 3): Targets organizations handling CUI for DoD programs with the highest priority. Compliance entails adhering to the 110 security requirements based on NIST SP 800-171 Rev 2 and an additional 24 security requirements based on NIST SP 800-172. These organizations undergo tri-annual assessments conducted by the DoD’s Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
Organizations must obtain a CMMC Level 2 Final Certification before scheduling a DIBCAC assessment for CMMC Level 3.
The results of all assessments conducted on DIB organizations are consolidated within the Supplier Performance Risk System (SPRS). The SPRS (pronounced “Spurs”) is Department of Defense’s web platform that collects, processes, and retrieves data on supplier performance within the Defense Industrial Base, enabling the DoD to map the DIB’s business network cyber maturity, assess supplier performance, and evaluate risks related to contractual obligations.
By deploying this mandatory certification model, the DoD is at the forefront of establishing a comprehensive, secure, end-to-end supply chain framework within the DIB, hopefully enhancing long-term U.S. national security. Simultaneously, the DoD underscores that security is no longer optional; it is an integral aspect of business operations.
CMMC 2.0 assessments are expected to become available around Q4 2024 (once 32 CFR is finalized). Prime contractors will expect sub-contractors to achieve CMMC compliance before Q3 2025, when CMMC 2.0 takes effect. Starting October 1, 2025, CMMC certification will be mandatory at the time of contract award.
If you require assistance navigating the intricate landscape of CMMC 2.0 compliance or need support on your path to certification, #Wavestone is ready to empower your journey. Reach out today and elevate your cybersecurity readiness into a strategic advantage.


