IEC 62351 is an international cybersecurity standard for Smart Grid communication and control systems. Its aim is to help grid operators protect themselves against threats endangering this sector, while adapting the recommendations to the realities of the industrial world.
In fact, many of the systems, equipment, and communications channels in such a network are:
- Limited in terms of memory and computing power.
- Located at remote sites with little or no staff or internet access (as opposed to an industrial system within a factory, for instance).
- Incompatible with wireless technologies, due to the electrical environment of substations and the higher reliability required by certain applications.
- Deployed for a long period of operation, which creates constraints in terms of maintaining security and interoperability with other systems.
In an intelligent electrical system, two network infrastructures coexist: an electrical network and an IT network.
The electrical network connects the equipment used to generate, transmit and distribute electricity. This includes power stations, transformers, power lines, substations, and electricity meters.
The computer network is used to monitor, control, and optimize power system operations. The aim of IEC 62351 is to secure this IT network.
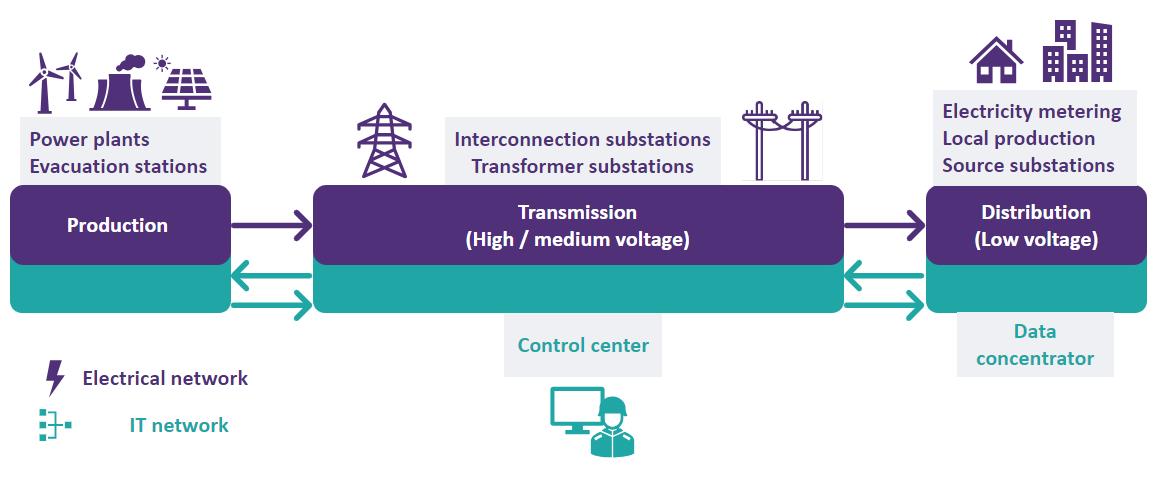
Electricity and IT networks coexist in parallel in a Smart Grid context.
Today, the proliferation of industry standards means that one must wonder what this standard offers in relation to others, or whether it is appropriate for a customer to seek compliance with certain sections of the standard.
A standard to be used as a guide to good practice
To date, no organisation offering certification to IEC 62351 has been identified, although some certification authorities do offer conformity assessments (technical tests and associated recommendations).

Organizations offering conformity assessments IEC 62351
However, the main purpose of the standard is to provide cyber teams with the tools they need to integrate cyber security into the technical specifications of industrial systems, for use by operators and suppliers. Conformity tests can be based on sections 100 of IEC 62351.
Overview of the standard
The introductory section of the standard was published in 2007 in an industrial context that has changed considerably since then. The last section was published in January 2023 and a new section is currently being drafted. The 11 main documents that now make up the IEC 62351 standard, and their regular publication schedule, demonstrate a willingness to adapt to changes in the industrial context.
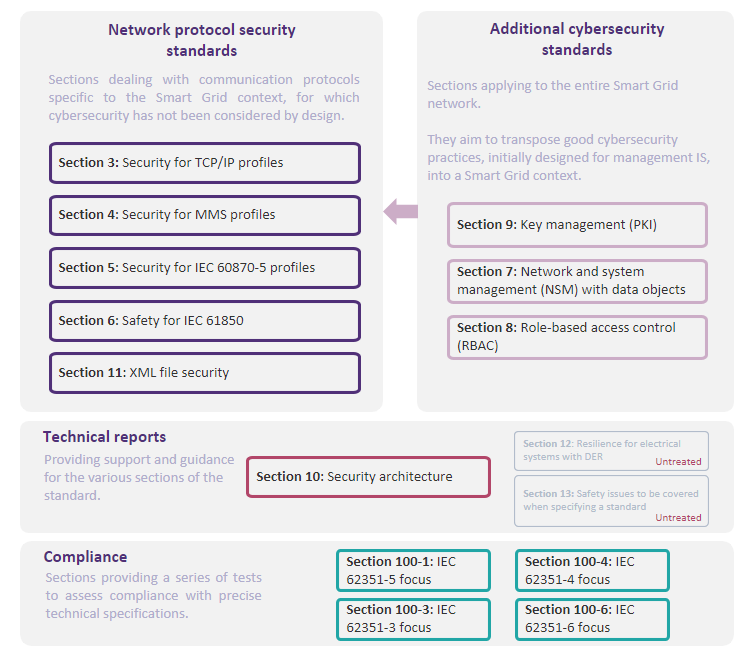
The IEC divides the standard into 4 main sections.
IEC 62351 complements existing cyber standards
To address Smart Grid cybersecurity issues in a coherent fashion, a combination of ISO/IEC 27001, IEC 62443, and IEC 62351 standards is required.
The ISO/IEC 27001 family of standards applies to any organization with an information system: it is still applicable to the companies considered here. The standards will provide an overall applicable organization as well as general security measures.
The ISA/IEC 62443 standard, which applies to industry, provides measures for industrial systems and components. It will ensure that the specific features of industrial systems are considered, at the boundary between IT and OT.
IEC 62351 is dedicated to IoT, with a very specific field of application: communication in an electrical environment.
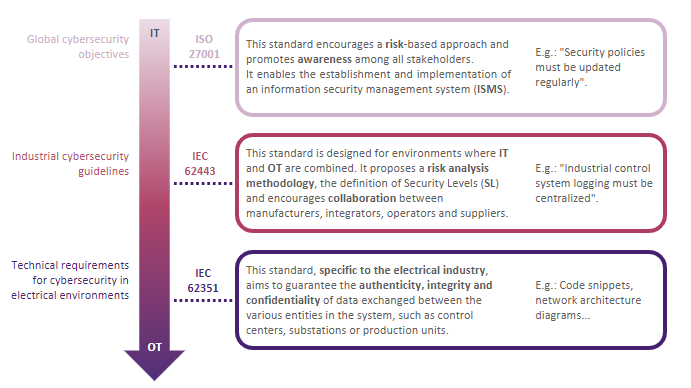
These standards cover increasingly technical and sector-specific subjects.
In particular, the standard details security measures for communication protocols specific to the sector
The communication protocols, defined in other standards, are useful for gathering information from equipment in the field and, in turn, for sending commands. Despite their key function, these protocols are not secured by design. The IEC 62351 standard allows security mechanisms to be implemented, using mechanisms already present to limit interoperability impacts. The concerned protocols are:
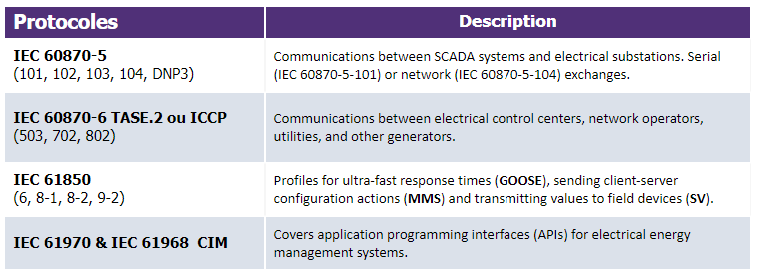
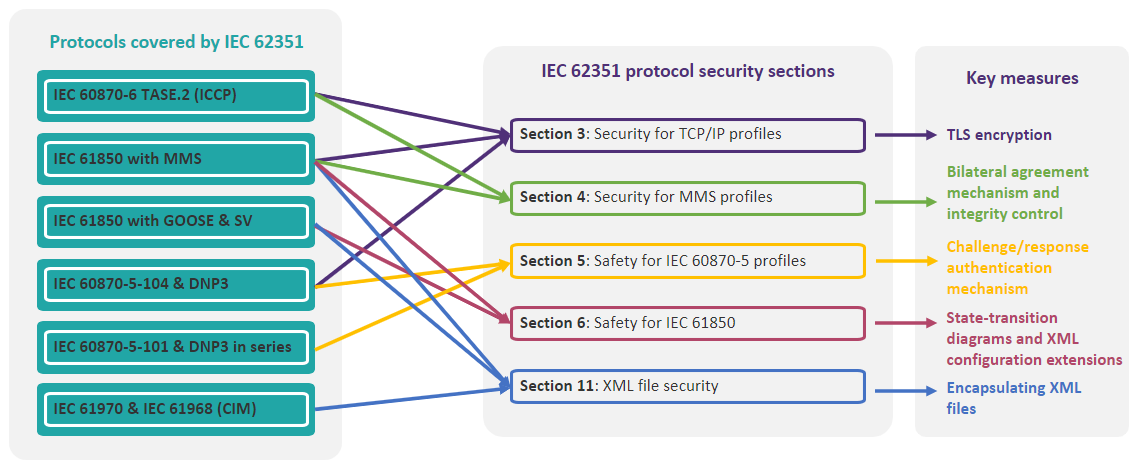 A chapter of IEC 62351 may deal with one aspect of the safety of several protocols. For example, aspects relating to the TCP/IP model are covered jointly in section 3 of the standard.
A chapter of IEC 62351 may deal with one aspect of the safety of several protocols. For example, aspects relating to the TCP/IP model are covered jointly in section 3 of the standard.
IEC 62351 was drafted by the same technical committee (TC57) that developed these communication protocols. The idea is to integrate security mechanisms into protocols that are completely lacking them. By considering their strong presence in the industry and their inherent constraints, the standard’s specifications promote interoperability. There’s no need to change hardware. The standard provides the right tools to secure protocols when required.
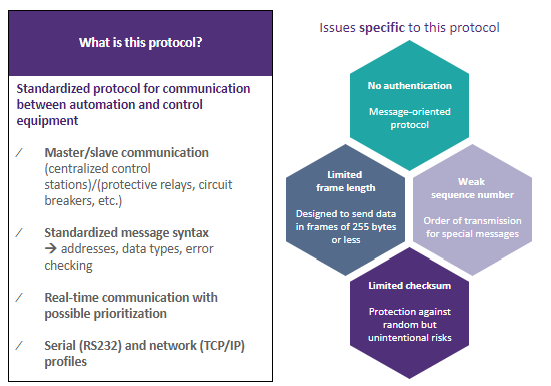
To illustrate the cybersecurity specifications to be found in IEC 62351, the example of section 5, dealing with the IEC 60870-5 protocol, shall be considered:
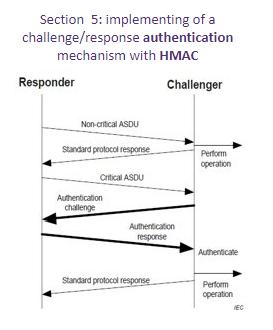
Concluding remarks
The IEC 62351 standard outlines best practices for securing electrical networks, with concrete measures for their implementation.
This standard can be used by CISOs to define concrete measures to be implemented on their most critical systems, and as a basis for drafting requirements towards their suppliers, to be integrated into specifications.
Glossary
|
ASDU |
Application Service Data Unit: actual data in a PDU corresponding to the application layer of the OSI model. |
|
CIM |
Common Information Model: standard defining the representation of managed elements in an IT environment, using objects and links. |
|
DER |
Distributed Energy Resources: power generation using small-capacity plants connected to the low or medium-voltage grid. |
|
GOOSE |
Generic Object-Oriented Substation Event: event data transfer mechanism for all electrical substation networks. |
|
MMS |
Manufacturing Message Specification: international standard for the transfer of real-time process data and supervisory control information. |
|
SCADA |
Supervisory Control and Data Acquisition: real-time data acquisition and control system |
|
SV |
Sampled Values: protocol for high-speed, real-time propagation of analog and digital sampled values from IEDs to other devices in the substations network. |


