Recent advances in artificial intelligence (AI) promise a revolution in every aspect of our lives, both professional and personal. This transformation is affecting every job within our companies, raising questions about the impact of AI in well-established areas such as identity and access management (IAM).
Although opinions are divided between the enthusiastic, the fearful and the sceptical of AI, the most optimistic argue that artificial intelligence can improve our work processes and facilitate sometimes repetitive actions by posing as an enabler to the completion of our tasks.
But can these advances be applied to IAM? Can we delegate the management of our identities and accesses in whole or in part, when the protection of user data has become a major concern?
AI and IAM: a new challenge for companies
A fundamental question arises when it comes to thinking about the relationship between AI and IAM: insofar as IAM systems exist to establish digital trust, whether towards our employees, customers or partners, is it possible to guarantee that AI-based solutions will ensure this same level of trust?
Despite the possible questions, we believe it’s imperative to consider the possibilities offered by AI. IAM teams need to open up to these new challenges and adopt a “Test & Learn” approach based on concrete use cases. Collaboration with IAM editors, integrators or internal Data or AI teams is necessary to explore all the possibilities.
What’s more, we’re convinced that the current environment offers fertile ground for the adoption of this approach:
- Corporate management and businesses are seeking to understand the potential impact of AI on different aspects of the business, and IAM teams need to be able to provide answers.
- The development of Cloud offerings for identity and access management, and the increased convergence of Access Management (AM) and Identity Governance and Administration (IGA) solutions, are creating a favourable environment for the development of AI. Training algorithms can access more data, facilitating the production of value.
- The threat landscape is evolving ever faster – with AI in particular – and IAM teams are faced with ever more needs in terms of compliance, security, user experience and operational efficiency.
So it seems natural to ask whether AI can help solve these challenges by looking at real-life use cases. In this article, we’ll take a closer look at the possibilities offered by AI, the key levers likely to be impacted by its use, and how it might (or might not) change the way we operate around IAM.
The contribution of AI to the 3 key challenges of IAM
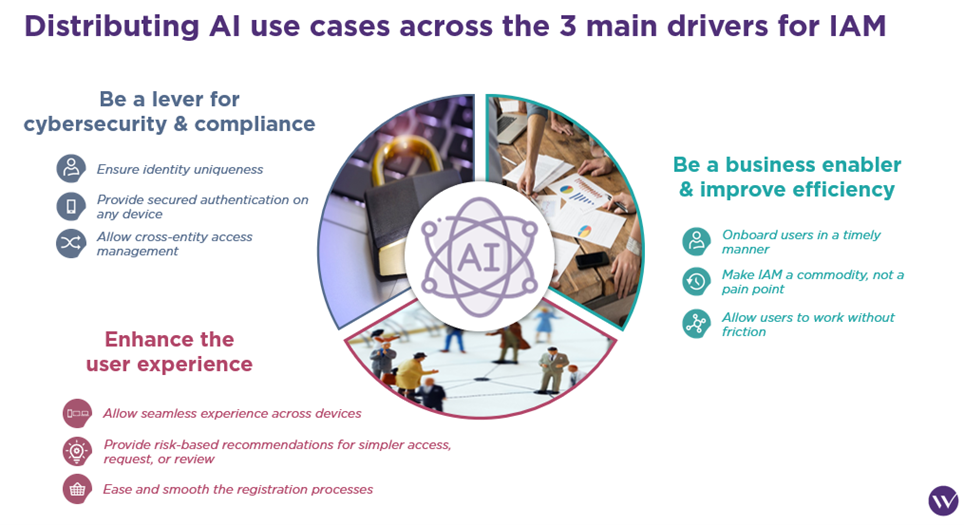
The analysis of different use cases taking into account AI for IAM has been thought around the 3 drivers of IAM:
- Cybersecurity and compliance
- User experience
- Operational and business efficiency
The use cases presented below are the fruit of the reflections of some forty consultants and IAM professionals who were invited to question the contribution that AI can make to IAM through various workshops.
Be a lever for cybersecurity and compliance
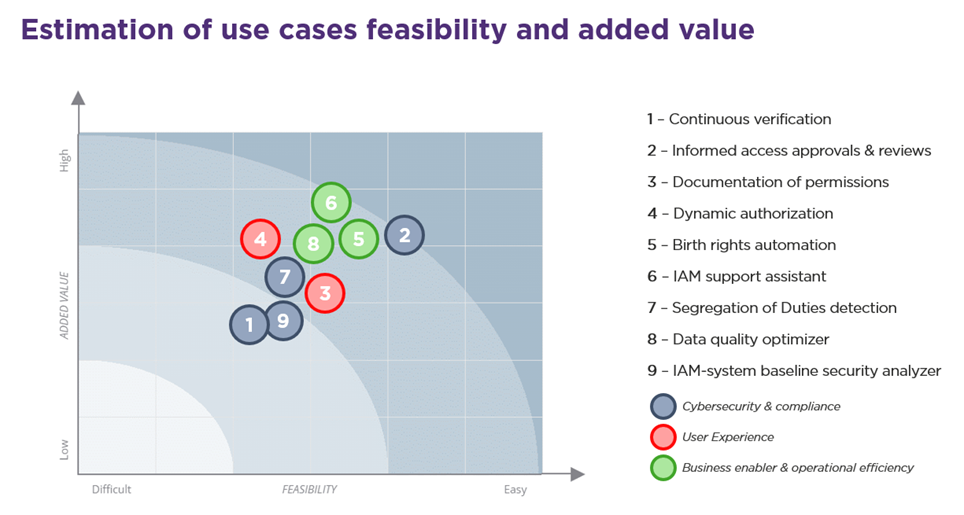
Use case 1: Continuous verification
At present, there are numerous mechanisms in place to monitor a user’s behaviour using various criteria (location, device used, etc.). Adding artificial intelligence to a continuous verification process would maximize the potential for surveillance during and after user authentication by:
- Aggregating a wealth of information about the user (behavioural analysis of keystrokes or mouse clicks, usual connection times, suspicious behaviour within the application, etc.)
- Providing appropriate automatic remediation (request for re-authentication, session termination, alerting security teams, etc.).
A number of software publishers are currently offering or planning to offer continuous verification functionalities. The aim is to use AI to continuously assess risks and apply security policies at login, but also during an active user session. These features reduce the risk of unauthorized access and so-called “post-authentication” threats, such as session hijacking, account hacking or authentication fraud.
Use case 2: Informed access approvals & reviews
Decision-making can pose challenges for both a manager and the user themselves, particularly when it comes to assigning or requesting rights.
Managers, for example, may not always have an in-depth knowledge of the specific rights to be granted to a member of their team, and it may be necessary to seek help in determining the best approach when assigning these rights.
What’s more, reviewing rights is a process that is generally unpopular with the various business units, even more so when it’s done manually. Managers may sometimes opt for a “default” validation of their team’s rights, due to a lack of time or knowledge.
This is where artificial intelligence can come in, offering fast and effective assistance to the managers concerned. It can provide recommendations for a user, taking into account various factors such as the number of people on his or her team with similar rights, the rights recently assigned to collaborators working with him or her, or the rights required for his or her activity. This assistance in assigning and reviewing rights and accesses provides valuable guidance for managers. It reinforces the legitimacy of user access rights, as well as security.
It’s worth noting that AI-based decision support is one of the most popular use cases currently being promoted by software publishers.
Enhance the user experience
Use case 3: Documentation of permissions
It is essential for users to have a comprehensive and detailed understanding of their authorizations and accesses. This enables them not only to know their access rights, but also to identify any gaps in their activities. A simple list of rights can sometimes be confusing for most users. However, the use of generative artificial intelligence could enable the rapid creation of an “intelligent” schema, offering a clear visualization of the rights accessible to the user, with a visual distinction according to certain criteria such as:
- Level of rights (consultation, modification, administration, etc.)
- Area of application (purchase management, payment validation, etc.)
- Right criticality
- Period of validity of rights
- Conditions for granting rights (approval cycle)
- History of rights used
In this way, AI could greatly facilitate users’ understanding of rights, by providing a clear, structured and contextualized view of their authorizations.
Use case 4: Dynamic authorization
Being blocked from accessing a SharePoint document, application or group due to a lack of rights is not a trivial situation, and can severely hamper the user experience, especially when processing times are important. However, when the resources accessed are not critical, artificial intelligence has a real role to play in automating access efficiently. For example, based on the fact that people in the same team or working on the same project have certain accesses, AI could temporarily grant access to a user to avoid any blockage. At the same time, suggestions could be offered to the user to make the request and gain extended access.
In addition, this dynamic approach to authorization may offer advantages in terms of license savings. If the allocation of a right in an application requires the use of a license, a temporary (“just-in-time”) allocation enables the user to use the license only as long as necessary for his or her tasks, before reallocating it to another user. In addition to improving the user experience, this approach can also generate significant budget savings.
Be a business enabler and improve efficiency
Use case 5: Birthrights automation
Joiner-Mover-Leaver (JML) processes are of crucial importance within corporate IAM processes. Among other things, they aim to control and facilitate changes in a user’s status according to a defined set of rules. This includes activating or deactivating access and assigning the appropriate level of rights according to the principle of least privilege, for example, by removing obsolete rights following internal mobility.
Users must therefore not be “blocked” (by a lack or absence of rights) when they arrive or move, as this would have a major impact on their activities.
Artificial intelligence could play a major role in these JML processes, by analysing the background of users occupying the same position/department, who have already received a set of rights on arrival. These analyses could generate suggestions for rights and accesses to be assigned to a new arrival in the same department. In addition, artificial intelligence could suggest improvements to mobility processes by suggesting a set of rights corresponding to the roles assigned in the new department, or even facilitate the evolution of business roles by proposing modifications to their composition.
Use case 6: IAM support assistant
Interactive chatbots are gaining increasing prominence within companies, assisting users in various processes such as incident creation or document retrieval.
However, thanks to artificial intelligence, these chatbots could also provide valuable support to cybersecurity and support teams by speeding up information retrieval. For example, cybersecurity teams could ask the chatbot to provide all user’s sensitive/privileged authorizations, while support teams could ask why a user is pending clearance for an application.
The considerable time currently spent by these teams searching for relevant information, retrieving the right incident tickets and reviewing user histories could thus be significantly reduced. These chatbots would be able to query IAM solutions, incident management tools and other enterprise tools to retrieve the necessary data. This would enable teams to concentrate on higher value-added tasks and resolve incidents more efficiently.
***
Far from being exhaustive, these few examples illustrate the diversity of application areas for AI within IAM. Other use cases could also benefit from AI, such as :
- Detection of incompatible access rights (Segregation of Duties): Identify incompatible rights according to business activities, proactively detect conflicts in user authorizations and propose remedies.
- Data quality optimization: Improve data quality by automatically reconciling large volumes of data, correcting duplicates or orphan data, reporting discrepancies or abnormal volumes, automatically cleansing and correcting data.
- IAM-system baseline security analysis: Evaluate the configuration of the IAM system against standards, best practices, vendor recommendations and external observations, and offer suggestions for strengthening security.
It’s important to note that ease of implementation and interest in all of the use cases mentioned vary according to a company’s . For example, in the industrial sector, the focus may be on process efficiency and safety, sometimes to the detriment of the user experience, due to complex and historical processes based on older technologies.
Nevertheless, in the workshops we organized around the topics of AI and IAM, here’s what emerged in terms of estimated feasibility and added value on the 9 use cases presented above:
What can we expect in the future?
AI enables and will increasingly enable us to respond to the 3 pillars of IAM (security & compliance, user experience and operational efficiency). Some use cases are already being proposed by vendors and will continue to evolve, others are on their roadmap, and still others are limited to technical constraints and remain at the stage of promising ambitions for the time being.
However, to focus solely on promises would be to put blinders on, and it is imperative to recognize and anticipate the risks induced by the use of AI in IAM right now: notably the possibility of deceiving authentication measures, the development of innovative identity-based attacks (high-quality phishing, deep voice fake, etc.) and the ability to exploit data and vulnerabilities within IAM systems and policies. There are also fears of biased decision-making in granting access, and of access management for AI that needs to be interconnected on all sides. These risks are also complemented by the risks inherent in AI: corruption of output data, theft of information by understanding the limitations/weaknesses of the AI model, the possibility of misleading the AI’s recognition capability… These risks have been addressed in greater depth in another article we recommend: Securing AI: the new challenges of cybersecurity.
What’s more, some use cases appear to be highly specific to the context and IAM maturity of each company, which may be a limitation for the time being towards software publishers, who generally target more generic use cases. Companies could then turn to in-house development solutions, but this choice is currently too costly, with no guaranteed return on investment.
Because of the associated risks, the lack of regulation, the fundamental role of IAM and a strong dependence on the context of each company, the current trend in AI in IAM is leaning more towards suggestion and decision support rather than autonomous decision-making, but for how long? The rapid emergence of AI and its increasingly frequent integration into our landscape begs the question of how long we have before trusting AI to get the right level of reactivity, detection and resolution… to cope with AI.


