FOCUS TECH
BLINDSIDE
Facing the EDR behavioral supervision, attackers develop techniques for successful attacks by staying under the radars. One of these techniques is called Blindside. This technique works on many EDRs relying on a hook and was revealed by Cymulate.
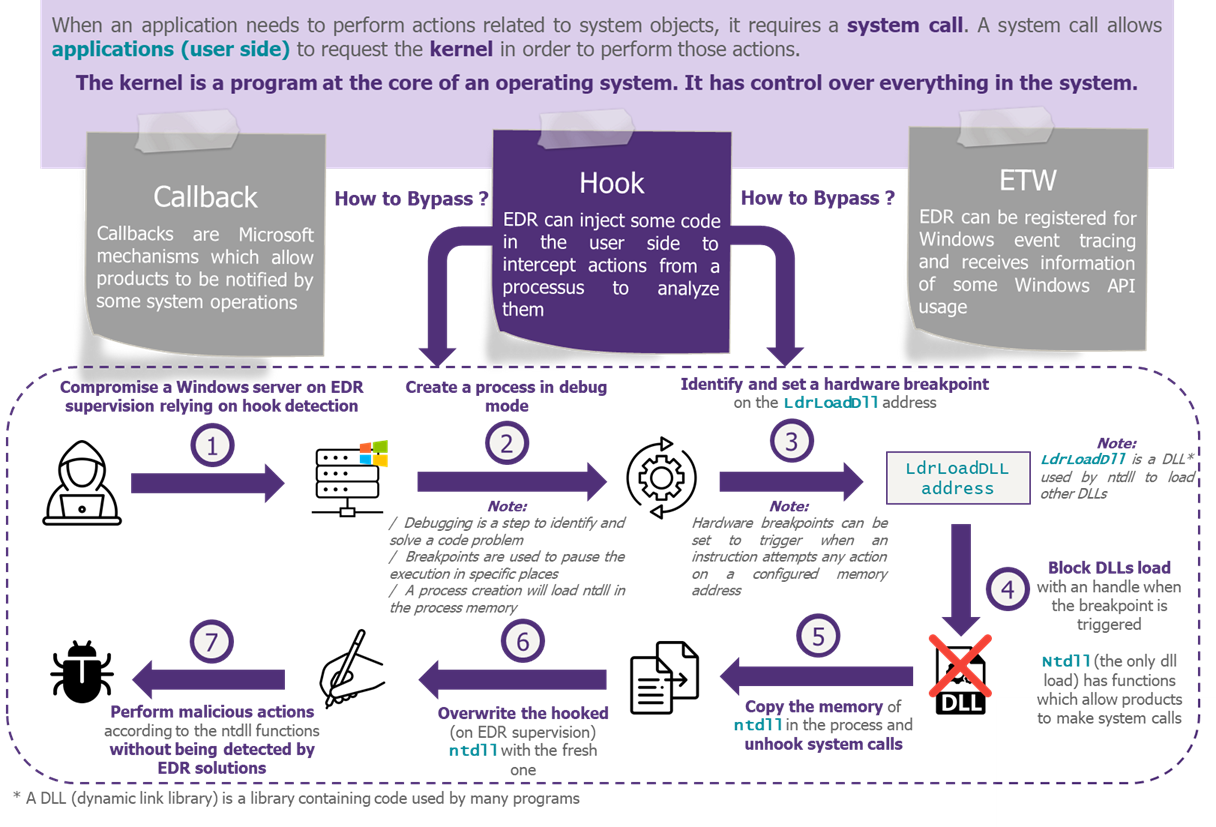
According to Cymulate, the author of Blindside, the technique is not immune to detection. Some mitigations can be implemented such as:
- Monitor the use of the SetThreadContext function: the function context can inform on breakpoint setting (write inside debug address registers)
- Monitor the presence of suspicious debug functions
- Edit EDR settings for checking debug registers
It remains difficult to bypass EDR solutions as their detection methods vary between vendors. Nevertheless, it is important to remember that it is possible and that the security should not rely solely on the solution.
CERT-W: FROM THE FRONT LINE
THE FIRST RESPONDER WORD
READING OF THE MONTH
SOPHOS: MATURING CRIMINAL MARKETPLACES PRESENT NEW CHALLENGES TO DEFENDERS

Maturing criminal marketplaces present new challenges to defenders, Sophos 2023 Threat Report
VULNERABILITY OF THE MONTH
PROXYNOTSHELL: WHEN APPLYING MITIGATIONS KEEPS YOU VULNERABLE
CVE-2022-41040 & CVE-2022-41082
Published by NVD: 02/10/2022
Products: Microsoft Exchange server
Versions: on-site/on premise 2013, 2016 and 2019
Score: 8.8 HIGH
Microsoft Exchange is a mailbox server exclusively running on the Windows operating système.
In September 2022, a vulnerability to compromise the underlying Exchange server was discovered. It was named ProxyNotShell after its similarities with the ProxyShell vulnerability. To exploit ProxyNotShell, attackers need to have an authentified access to the Microsoft Echange server. The exploitation of the vulnerability allows attacker to deploy a webshell on the targeted server, giving them an initial access.
Around November, a number of mitigations (Hotfix) were released awaiting for a patch. As a result, some 60 000 servers worldwide still are vulnerables since the few mitigations rules can be bypassed by attackers.
According to CrowdStrike, Play ransomware group, which has been active since last June, took advantage of this in using a new exploit to bypass the URL rewrite mitigations for the Autodiscover endpoint. Early December the managed cloud hosting services company Rackspace technology complies to having been attacked after a successful exploit of the vulnerability in Microsoft Exchange Server.
The Microsoft Exchange server should have at least the KB5019758 patch. If not, the main action to perform is to immediately install the updates on the vulnerable servers. If some factors make the installation impossible, it is adviced to disable OWA until it can be applied. In addition, it is strongly recommended to disable remote PowerShell for non-admin users and use EDR tools to detect if web services are spawning PowerShell processes.
SEE YOU NEXT MONTH!!



