Overview
Spring is a lightweight opensource application framework for Java. It allows for easy development and testing of Java applications.
Spring is used to create Java enterprise applications. It provides means to build applications and supports different scenarios.
A new vulnerability was found in Spring Core leading to a Remote Code Execution.
On March 31st, a CVE was released: Spring4Shell (CVE-2022-22965)
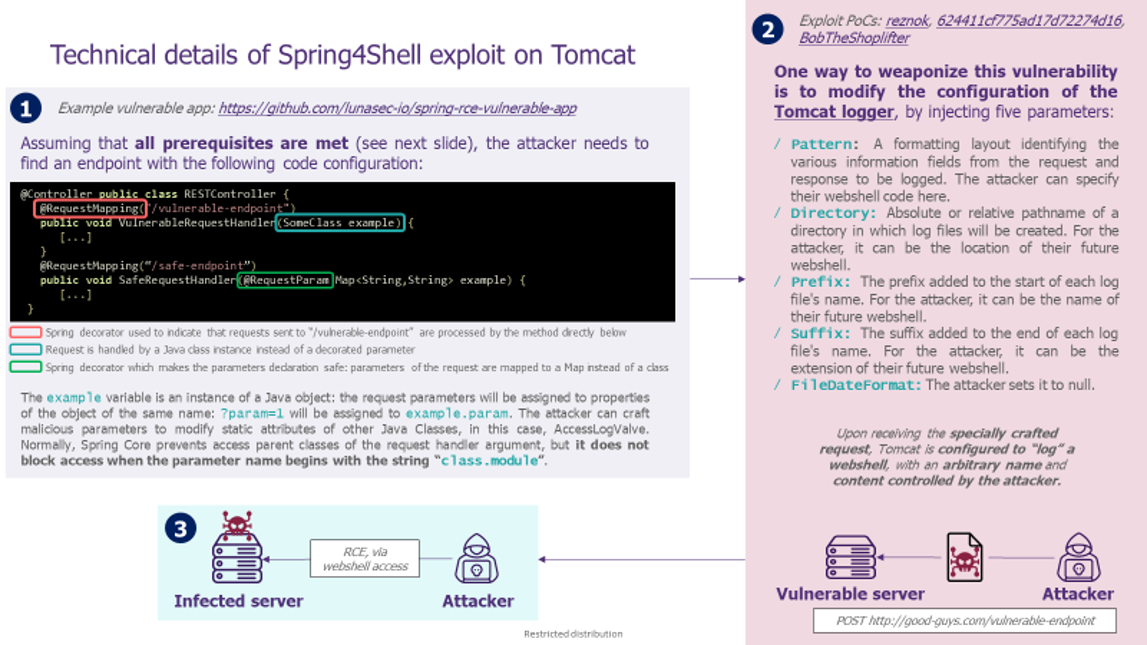
Exploitability
Prerequisites
/ JDK9.0 or higher
/ Spring Framework 5.3.0 to 5.3.17 or 5.2.0 to 5.2.19 & older versions
/ Apache Tomcat as the servlet container
/ Spring-webmvc or spring-webflux dependency
/ Packaged as a traditional WAR
Risks
Once all prerequisites are met, the Spring4Shell exploit allows for unauthenticated Remote Code Execution on the vulnerable host. This initial access may lead to further harmful infection steps by attackers.
A list of applications and vendors that have published a statement indicating if their product was affected is available:
https://www.kb.cert.org/vuls/id/970766
Difficulty
Many researchers are still sceptical as to how achievable this exploit is. It is now clear that due to the heavy prerequisites of the exploit, it should occur in fewer cases than the Log4Shell exploit. However, once the prerequisites are met, exploiting the vulnerability is pretty straightforward and has fewer constraints than Log4Shell (egress traffic is not needed).
Real-world examples
Some real-world examples meet the prerequisites. Some researchers have found that the Handling Form submission sample code provided by Spring in one of their tutorials is vulnerable to the Spring4Shell exploit.
Mitigations
Main recommendation: Update applications to Spring Framework 5.3.18 or 5.2.20 if possible
Manual workaround:
This section is applicable only if it is not possible to update the applications as mentioned above.
A temporary fix may be manually applied to mitigate the possibility of the Spring4Shell exploit: the following class must be created under the project package of the application system. After making sure the class is loaded by Spring, the project must be recompiled. This workaround only works against exploits known at this time, it’s effectiveness may not be guaranteed in the long term.
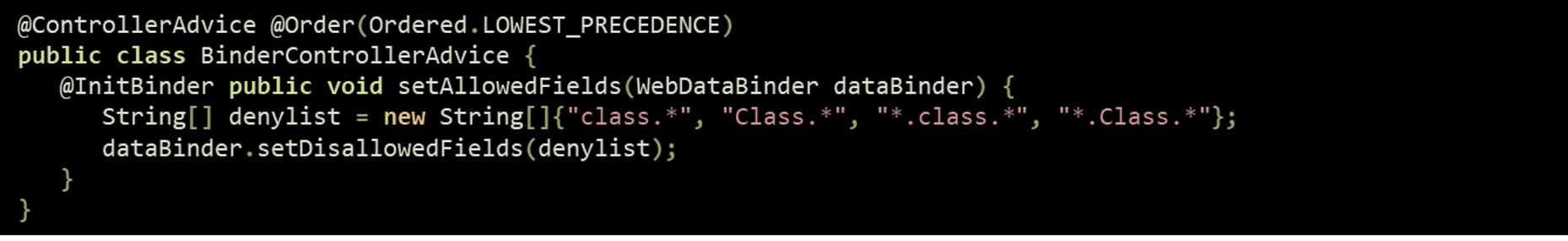
Good practice:
Point of attention:
The Spring4Shell exploit only provides command execution on the vulnerable host: it allows for initial access on a server exposed to the Internet. Commands will be executed in the context of the running application. A healthy, up-to-date infrastructure, as well as a good application of the least privilege principle, may greatly mitigate Spring4Shell’s impact.




