Cyber issues in the energy sector
The energy sector is made up of vital infrastructures and provides essential services for a country. The sector, shaped by increasing digitalization, is undoubtedly a prime target for cyber attackers with consequences that are liable to create shockwaves throughout the service industry as well as all major infrastructure. Taking electricity as an example, an outage spanning a few days would have grave consequences on transport, health and communication almost guaranteeing they cannot perform their core functions.
A sector undergoing transformation
The energy sector began its transition with the arrival of renewable energy. The shift in the sector is also due to innovative techniques and systems that have been integrated into the power grid to help manage the complex task of balancing energy levels, because it is vital that the energy pumped in and out of the grid at any one time always remain equal. This level of transformation leads to an increased need for flexibility to ensure security of both the power supply and the significant investments in the power grid. These are the objectives that have and will continue to drive concepts such as smart grids, to enable the control of energy consumption and optimization.
In response to these business evolutions (market shifts), the energy sector is undergoing a digital transformation that is disrupting the way energy is produced, processed, stored, transported, and consumed. Overall, information and communication technologies have helped optimize the supply chain. An example being the widespread deployment of industrial internet of things (IIOT) devices. The switch to these devices has led to an explosion in the volume of data in day to day activities. While energy companies must now use this data to be more agile in their decision making by effectively leveraging it, the large volumes of data expose the industry as a whole to a host of data based malicious actions, making cyber security a priority for the energy sector.
Here is a concrete example: remotely piloted, wind turbines and solar panels are by nature connected objects. They must be accessible remotely and therefore secure. However, these new projects do not systematically consider all cybersecurity constraints and related technical solutions (secure protocols, appropriate access technologies, etc.) from the design phase.
An increasingly targeted sector
Let’s look at the “history” of cybersecurity in relation to this sector: the discovery of Stuxnet in 2010 created a shock wave within the energy industry. This attack highlighted unknown vulnerabilities at the time.
In December 2016, some inhabitants of Kiev and its periphery were deprived of electricity for about 1 hour due to the disconnection of the substation of the Pivnichna electricity transmission power grid. The attack began as part of a massive phishing campaign in July of the same year, which exploited a vulnerability in Windows XP. The failure was caused by the remote switching of the circuit breakers to cut power.
Since then, cyber events have become recurring occurrences. Another example: renewable energies are new targets for cyber attackers. In 2019, in Utah in the United States, a wind and solar power system suffered connection losses with the company’s control center for 12 hours, causing power outages in surrounding homes. Cyber attackers had exploited a known vulnerability on unpatched firewalls causing a denial of service of equipment.
In 2021, the executives of Colonial Pipeline, which connects refineries across the United States, decided to block all their distribution operations following the spread of ransomware. The company said they paid $4.4 million in ransom for hackers to provide a computer tool to restore their business [1].
The energy sector is one of the most targeted sectors. According to the X-Force Threat Intelligence Index 2022 [2], the energy sector ranked as the fourth most affected sector in 2021, with 8.2% of all observed attacks, behind the manufacturing industry, the financial sector, and the professional services sector.
In 2021, ransomware was the most common type of attack against energy organizations with 25% of attacks. Oil and gas companies are particularly affected by this phenomenon. Remote Access Trojan (RAT), DDoS and Business Email Compromise (BEC) follow with 17% of attacks each.
While cyber-attacks are most often targeted for profit and espionage, the energy industry also deals with sabotage intentions, sometimes for geopolitical reasons. Some hacktivists can also pose a threat by attacking critical infrastructure. The recent ongoing major geopolitical destabilization events reinforce these risks.
The energy sector has critical infrastructure. In an increasingly interdependent world, any disruption, even initially limited to an entity or geographic area, can produce broader cascading effects as outlined below:
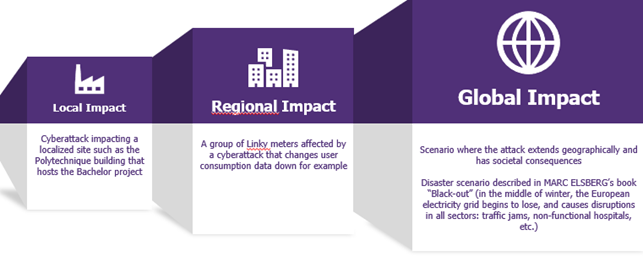
Impact Chain-Wavestone
To fight effectively against these new threats, the States and the European Union have adopted binding regulations to ensure a higher level of cybersecurity on the most critical facilities.
What role for regulation?
In France, the competent authority for cybersecurity is the Agence nationale de la sécurité des systèmes d’information (ANSSI). To respond to the increase in threats, the concept for the defence strategy has been based on the Military Programming Law (LPM) since 2013 in order to secure the Operators of Vital Importance (OIV). ANSSI mainly insists on procedures for the approval, control, and maintenance in security conditions of Vital Information Systems (SIIV).
At European level, the objective is also to protect sensitive organizations such as operators of essential services (OES) in the energy sector. The reference point for cybersecurity is currently the Network and Information System Security (NIS) directive. Its primary objectives are to increase cooperation between EU Member States, by facilitating the exchange of strategic and operational information, and to improve the cyber resilience of public and private entities in key sectors such as energy. When it comes to energy, ENISA wants to protect from large-scale threats with increasingly cross-border and interdependent power grid.
The complexity lies in the operational application of specific measures in industrial environments where equipment and means of production are expected to last several decades. Thus, modifying operational processes and/or equipment to incorporate additional cybersecurity is a concrete challenge. The impacts of this transition are significant both in financial and operational terms. This makes cooperation and sharing even more important for energy stakeholders to find pragmatic and adapted solutions: adapted network architecture, technical solutions compatible with the industrial world, vulnerability management processes and updates built with operational teams for example.
Conclusion
Considering the critical nature of the energy sector infrastructure, it is essential that business and cybersecurity actors in the energy sector communicate on good cybersecurity practices, learn from previous attacks, and contribute to changing the overall level of protection. It is in this context that the first forum dedicated to energy stakeholders «Cyber4Energy» will be held in Marseille on 30-31 March 2022. This event will be an opportunity for professionals to discuss cybersecurity challenges and dedicated solutions available to the sector.
Références :
[2] X-Force Threat Intelligence Index 2022, IBM Security X-Force Threat Intelligence Index 2022 (ibm.com)


