Industry 4.0, a milestone in the history of the technology race
Let us make a detour through a page of history, before plunging into the heart of our subject :
- In the 18th century, James Watt’s steam engine and coal mining changed the way of working. The use of hydraulic machines made the artisan workshops evolve into much more efficient factories: the 1st industrial revolution was in full swing.
- Then, the 2nd industrial revolution known for Taylorism and mass production is based on the use of electricity and oil. The long assembly lines, dear to Charlie Chaplin, replace the hydraulic and steam engines that are now obsolete.
- The development of new information technologies, from 1970 onwards, supporting operators in the most difficult tasks characterizes the 3rd industrial revolution. In particular, it allowed for increased robotization and production of larger batches.
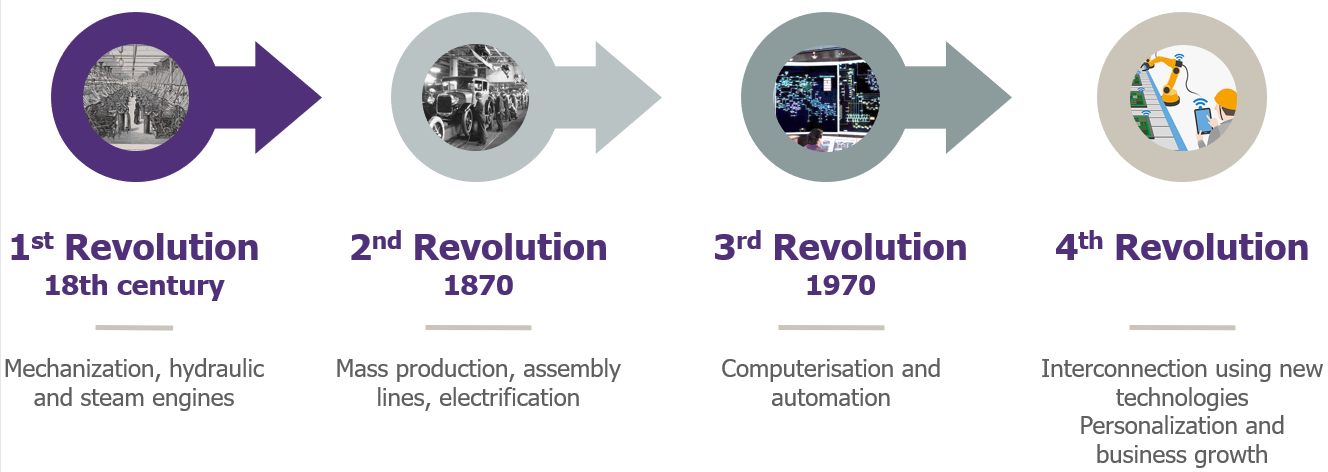
This 4th industrial revolution marks the arrival of new technologies that are increasingly connected, leading to a high level of dependence on information technology.
Industry 4.0 brings together a set of technological advances and technical tools for optimising industrial processes.
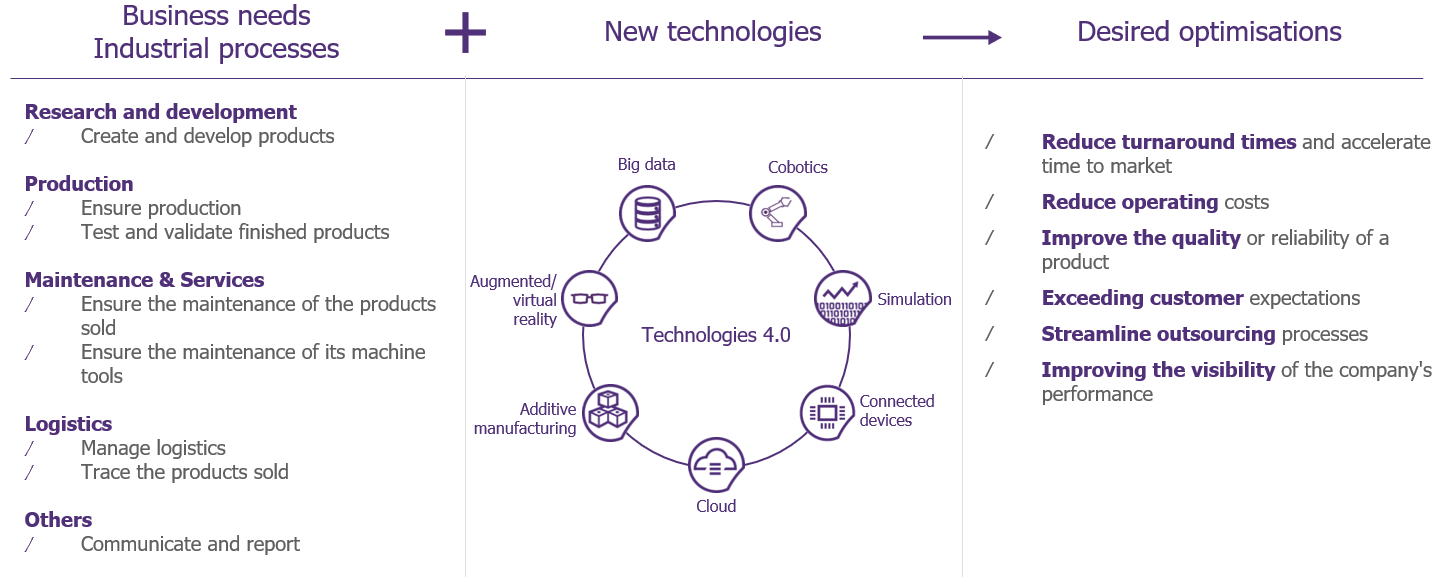
Let’s take a concrete example of a use case:

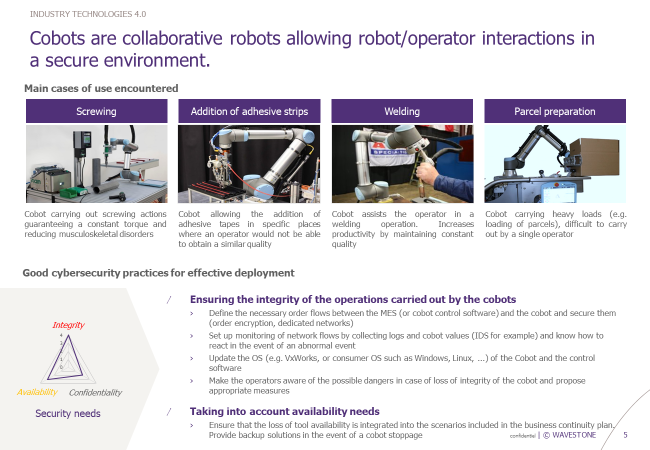
A company needs to accelerate its production rate and to robotise part of its actions to save time. For example, screwing actions. It chooses to use a collaborative robot, also called a « cobot »[1], capable of carrying out actions simultaneously or on the same workspace as an operator. The operator will be responsible for presenting the parts to be screwed to the cobot.
In addition to reducing turnaround time, the implementation of this binomial makes it possible to increase the quality of the finished product.
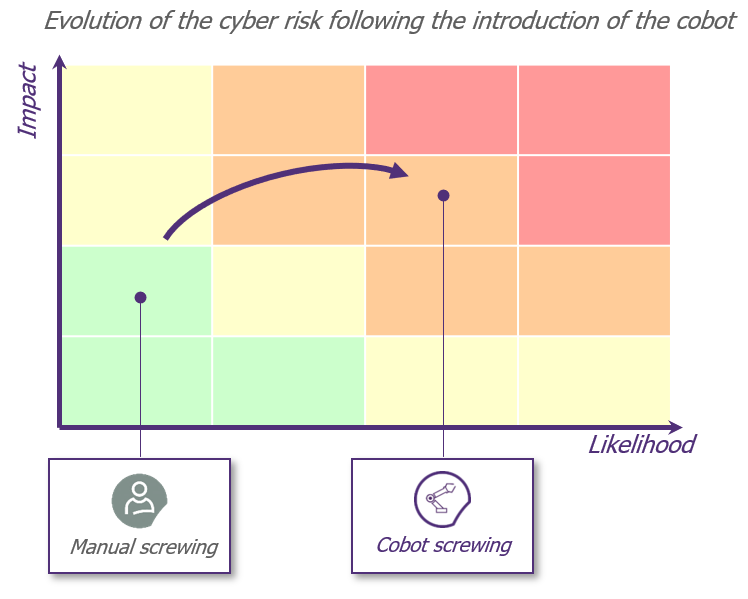
Industry 4.0 use cases increase the cyber risk to business processes. There are two reasons for this: the need for new interconnections of industrial systems with the outside world and the increased potential impact in the event of compromise..
What are the impacts for cybersecurity in this whole story? If we continue with this cobot, the screwing, initially done manually by an operator, is now made easier by the use of the cobot. The cobot has to be connected to receive orders and be updated.
- The manual operation is replaced by a computerised operation that is now exposed to a cyber attack
On a conventional robot, a “safety cage” is present to prevent intrusion by an operator during the operation of the machine tool. On a cobot, as there is collaboration with the operator, this protection does not exist. An impact in case of contact between the cobot’s screwdriver and the operator’s hand would be particularly serious for the operator !
- The introduction of new technologies can increase the severity of a cyber attack
This is not the only consequence of unsafe use of such technology :
- Changing a value in the cobot regarding the screwing torque can lead to a quality defect in case of incorrect tightening ;
- Greater importance of assisted operations means that in the event of a failure, the impact on production will be greater… which will quickly lead to a financial impact.
Let’s sum up a little simplistically :
The question now is how to deal with these risks, without blocking the legitimate demands of operational staff. Spoiler: no, refusing the project is not the solution!
The teams responsible for cybersecurity can anticipate the needs for the implementation of 4.0 technologies by drawing up adapted reflex sheets
From a technical point of view, we can group the advances linked to Industry 4.0 around a few major themes: augmented reality, connected objects, additive manufacturing, etc. Upstream of projects and with a few well-informed industry players around the table, it is possible to anticipate potential demands.
The objective for the cyber security team will then be to draw up a profile of typical use cases, deduce the potential risks and begin to identify appropriate security measures to respond to them. It is also an opportunity to propose “Industry 4.0” checklists to raise awareness upstream of projects.
Concretely, here is an example of a typical reflex card applied to our cobot seen previously :
By preparing upstream, cybersecurity teams are more relevant and effective when a new project is about to start.
Ready to embark on a “4.0” project? This is the ideal opportunity to support the industry in the transformation of its factory by offering adapted cyber security services.
The advantage of “Industry 4.0” projects lies in their ability to make in-depth changes to the foundations, sometimes a little dusty, of systems and networks already installed in the factory.
Does a conveyor project need to exchange information with the outside world? This is an opportunity to propose a secure file exchange server in your industrial DMZ (if you don’t have one, this is also a good time to think about it). Does an augmented reality system need a more stable wireless connection? This is the time to start thinking about strengthening the control of the devices that can be connected to it…
At the risk of repeating the obvious here, the ideal is to arrive upstream of the projects, through a constructive approach, rather than through a 100-page ISSP and guides to standards and technical rules that are not adapted to the cases of use presented.
For the risk analysis of an “Industry 4.0” project, the EBIOS RM risk analysis method facilitates exchanges by sharing strategic scenarios that can be understood by the business
Once discussions have begun on a concrete project, it is useful to carry out a risk analysis to support the discussions. Its depth and method will depend on the size and risks of the project.
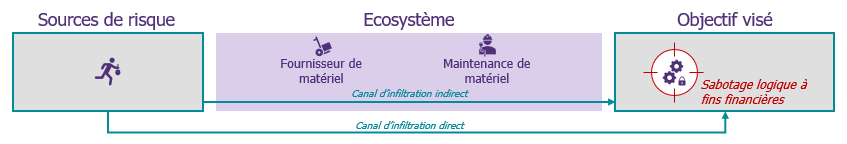
This analysis will make it possible to refine the objectives we wish to protect, take a step back from the existing ecosystem and define the most convincing attack scenarios.
Here are some examples of frequently found scenarios :
- Logical sabotage for financial purposes (long version of the Ransomware scenario): A targeted or non-targeted attack, making equipment unavailable for financial gain.
- Stopping/Slowing down production: Targeted sabotage to gain a competitive advantage, revenge by ideology or just by defiance can be carried out by a malicious competitor, an avenger, a terrorist, an activist or even a thrill-seeking amateur. Also be careful not to forget the errors of manipulation !
- The alteration of the quality of the part produced: rather sophisticated and targeted sabotage impacting the quality of the products to discredit the company or simply create damage.
The conclusion of the risk analysis will make it possible to precisely define the cybersecurity measures to be put in place and the associated residual risks.
To move away from the “fortified castle” model, i.e. to focus on the isolation of its industrial IS and perimeter security, and to propose adapted security measures: finer detection, encryption, MCS … in a way, it’s time to move on to “4.0” measures
Our feedback shows that the definition of an action plan is a balancing act in these “4.0” projects. Indeed, by applying an overly restrictive safety model, based on IEC 62443-3-3 type zones and ducts, we run the risk of misunderstanding between the stakeholders. In fact, not all business solutions are compatible or mature, and many have not yet integrated the standards we would like to see applied.
So what to do? One way might be to propose appropriate security measures, “4.0” measures (for the industrial environment in any case) that have already proved their worth in other environments:
- To prevent a threat from spreading, one shall strengthen detection resources, especially the flows from and to industrial IS. This is the time to take advantage of this opportunity to dock with the Group SOC if it has not already done so.
- To ensure the integrity and traceability of transmitted/received data, encryption and authentication can be implemented. Do you already have a Group PKI? Why not think about extending it to industrial perimeters.
- It is also the right time to strengthen its OCM / SCM process. Is the solution connected with the outside? No more excuses for not installing an antivirus, updating it, installing security patches for your favourite OS, etc. This point should be anticipated prior to purchasing the solution, rather than once the product has already been installed!
- Finally the solution is critical for the business? A cyber-resilience component must be anticipated so that the solution can be quickly rebuilt and restarted in the event of an attack.
As we have just seen, there is no shortage of solutions, but they require adapted support from the cybersecurity teams and going beyond theoretical models. So, let’s take advantage of these “4.0” projects to make our industrial cyber security models evolve without a priori!
[1] https://commons.wikimedia.org/wiki/File:Cobot.jpg license CC : https://creativecommons.org/licenses/by-sa/4.0/deed.en


