Within any infrastructure or application, privileged accounts are particularly sensitive accounts. Securing them is a key issue. This is especially true for SaaS services, where the shared responsibility model requires an organization to protect its data and identities, and the Microsoft 365 suite is no exception.
In fact, if there’s one thing you need to protect, it’s your administrators!
Whether it concerns authentication methods, third-party application permissions via APIs (allowing a third-party application to synchronize data with an external storage service, for example) or changing retention policies, an administrative action can significantly affect the data and security of the tenant on a larger scale. If it is necessary to make this point even more explicit, a Global Administrator has the ability to access all data or manage all the settings of Office 365, Windows 10, Azure AD… but also Azure!
What are the native functionalities in the Microsoft platform?
Which rights models within Microsoft 365?
To date, Microsoft 365 has two main levels of rights. These two levels schematically allow the delegation of administrative rights by adapting to different organisational models (small / medium / large, centralised / decentralised):
- Azure AD roles: Administration of Azure AD and Microsoft 365 services;
- RBAC roles: Administration of objects within services.
Level One: Using Azure AD roles to manage services
The person behind the opening of the tenant automatically takes over the role of General Administrator. He can then appoint other administrators to accompany him in his tasks. As far as possible, Global Admin’s rights should not be used in order to limit overexposure of the administration accounts. It is good practice to limit this general role to a maximum of 3-4 accounts. In addition, for almost all actions there is an equivalent service administration role (e.g. SharePoint Administrator, User Administrator, etc.).
These service administration roles are also known as Azure AD roles. Each service can be viewed as an Azure AD application. An administrator would thus be equivalent to the owner of the service in question. At the time of writing this article, Microsoft offers 59 different roles, which provides a good level of segregation of rights in most cases.
However, the default roles provide access to the entire Admin Service for the entire tenant and may in some cases provide access to the underlying data (e.g. for SharePoint Administrator, Exchange Administrator and User Administrator).
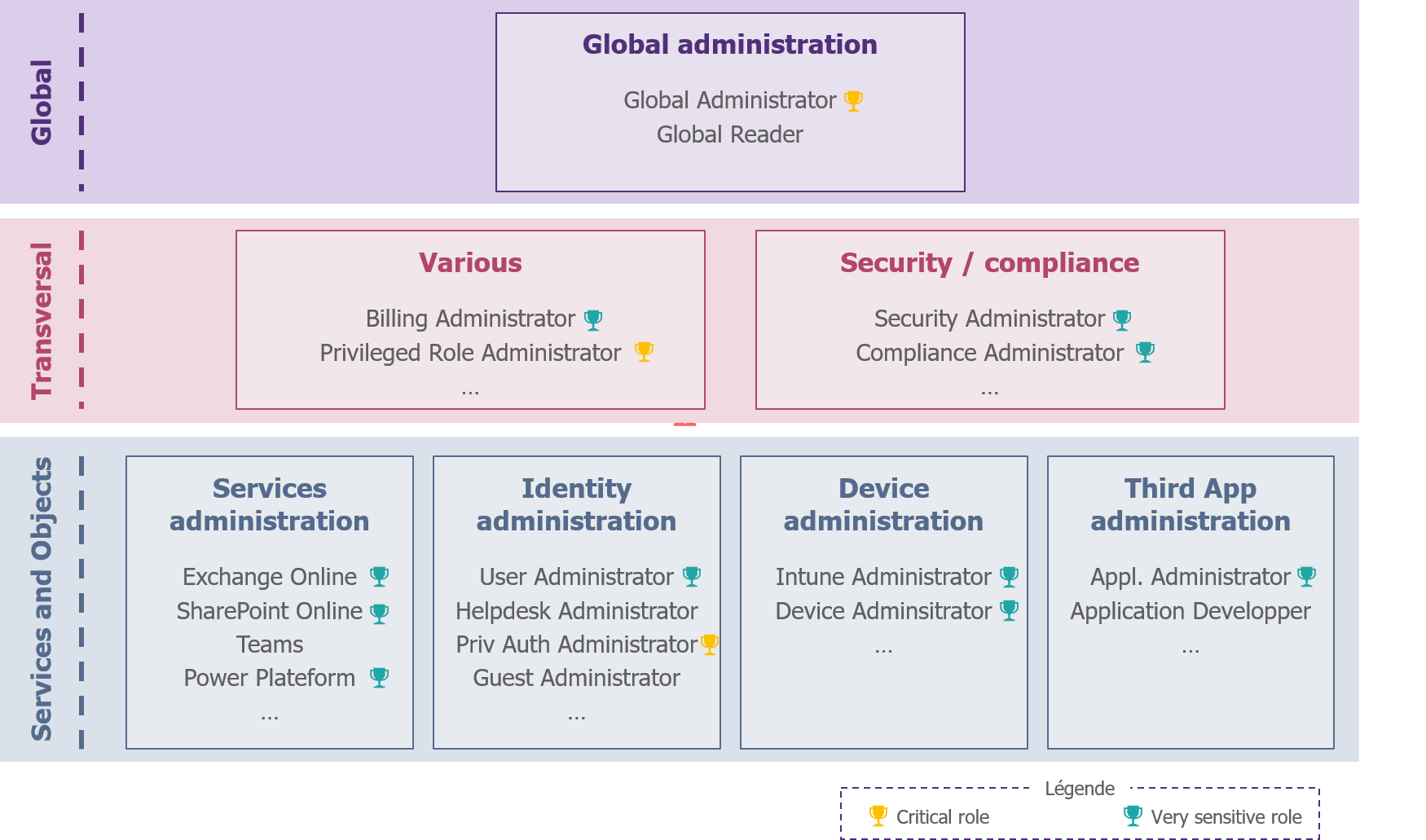
Figure 1 – Example of sensitive rights
In the case of advanced maturity, it is possible to go further in the segregation of rights by creating personalised Azure AD roles. In concrete terms, this means deciding what permissions this role has (e.g. “microsoft.directory/applications/create” allows you to create applications in Azure Active Directory).
The downside will be that it will be more complicated to audit the administration and that it will be necessary to monitor the evolution of services to ensure that permissions remain consistent with the needs of administrators.
Second level: Using the RBAC model to manage objects
Certain services such as Exchange Online, Intune, Security and Compliance Centres or Cloud App Security offer specific RBAC rights models.
As its name suggests, Role Based Access Control (RBAC), allows for the implementation of more refined permissions management; with the ability to define roles for defined perimeters (e.g. for certain user groups). For example, it will be possible to create “Helpdesk A” and “Helpdesk B” in Exchange Online to give support rights to two separate teams on a perimeter A and a perimeter B.
How to provision the accounts of administrators?
The first question is how to create an administrator’s identity. Two strategies are possible:
- The creation of an account in the organisation’s identity repository, which will then be synchronised with Azure AD (ex: wavestone.com);
- The creation of the account directly in Azure AD. This account will then be called “cloud-only” (example: wavestone.onmicrosoft.com).
Regardless of the administration role, it is recommended for a SaaS service such as Microsoft 365 that the account be located as close as possible to the administered resource. Here, this amounts to using cloud-only accounts. The objective is twofold: to protect against a possible unavailability or of a compromise of the organisation’s identity repository.
How to assign permissions?
The second question is how to assign the right privileges to the administrative roles created.
In the case of service administration
In order to assign an AAD role, it is possible to use 3 methods (via the portal or the corresponding PowerShell command):
- The Azure portal (portal.azure.com): this is the method that should be favoured, as it allows the association of rights as close as possible to the resources and the use of PIMs, which we will discuss in the rest of the article;
- The Microsoft 365 portal (admin.microsoft.com): it is possible to carry out the assignment of roles directly through the main administration portal. However, this method is not compatible with PIM;
- The use of third party IAM tools: these solutions now have connectors with Office 365 to perform identity and privilege provisioning. These solutions offer less granularity, are not compatible with PIM and are a source of common errors. For example, synchronisation is typically one-way, resulting in the administration account reappearing if it is only deleted in Azure AD.
Note that it is also now possible to assign an Azure AD role to a security group (Cloud only) via a preview feature. This may simplify certain administrative models, such as where the Unified Communications team needs the SharePoint Administrator role and Teams Administrator. However, be careful with the management of this group.
In the case of the administration of objects
For RBAC roles, the definition of roles is done directly in the administration platform of the service concerned. It is then possible to assign the role in question manually or to a security group, in the portal or via an IAM solution.
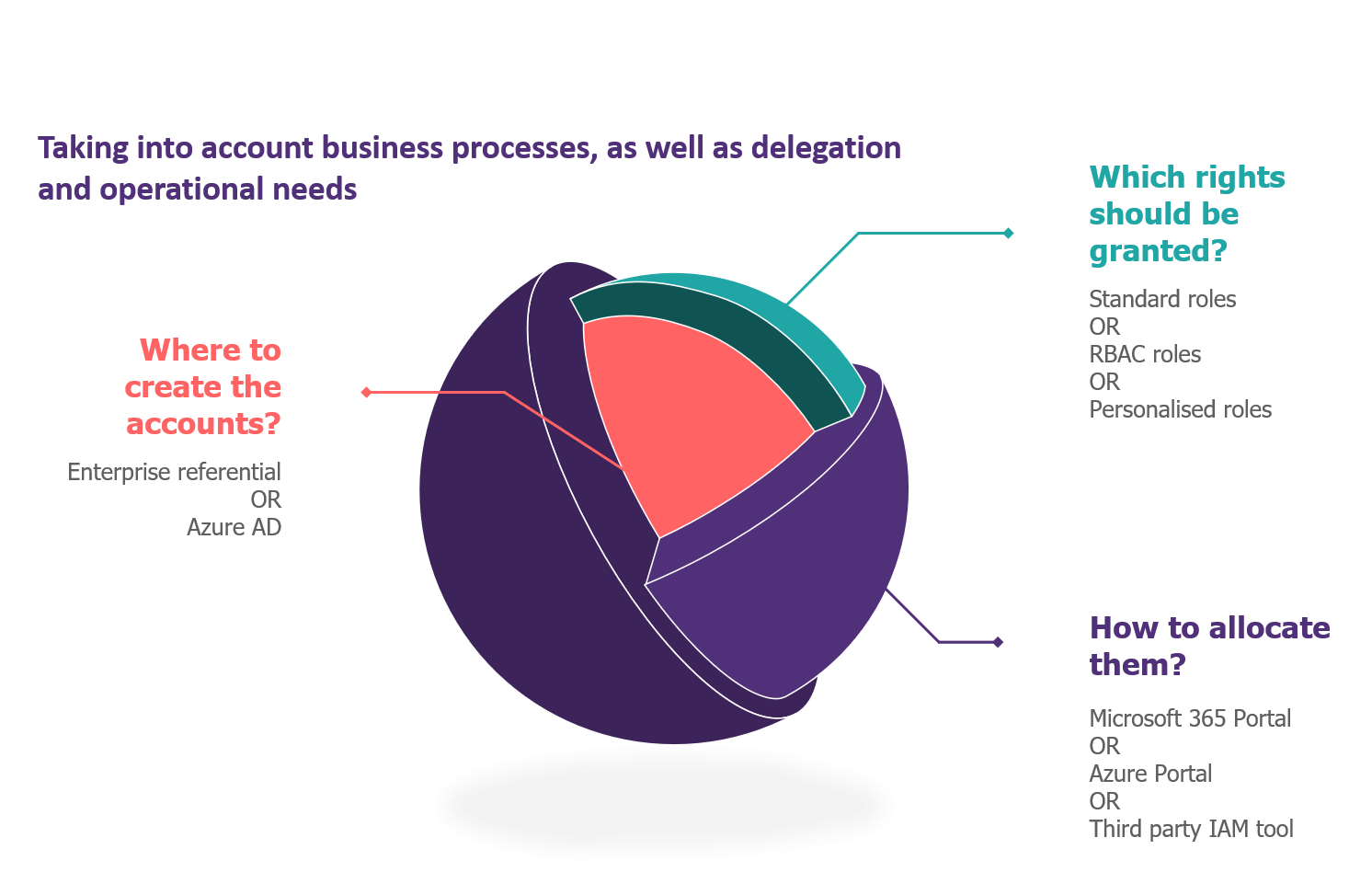
Figure 2 – Natives functionalities of the solution
How to build and implement your administration model?
What strategy to define your rights model?
The construction of a delegation model must be based on the principle of least privilege. The core of the work is to make an inventory of the cases of Office 365 administration usage and to match your teams with the available rights.
This can be an opportunity to rethink the organisation of teams dealing with the working environment. Two observations are quite significant:
- Mobile terminals and workstations are intended to be managed by unified solutions (UEM) such as Intune, Workspace One or MobileIron, and therefore by the same team.
- Security and compliance tools are increasingly integrated natively in Office 365. It is therefore necessary to break down the wall that existed between the workplace world and the security world, in order to create a team with the same ambition: to create and maintain a controlled and secure platform.
Office 365 has the particularity of bringing together a multitude of different services, such as file or information storage (SharePoint, OneDrive), communication tools (Exchange, Teams) but also security (Defender, Information Protection, etc.). It is therefore essential to group the services into categories and define a correspondence matrix between team and administration roles.
Concretely, we advise you first to use the default Azure AD roles for service administration, and then to define more granular roles with RBAC and custom roles.
It is also interesting to identify the most sensitive roles, such as those allowing access to data or security settings (for example: Global Admin, Exchange Admin, Security Administrator and Application Administration) in order to be able to adapt the security of these roles.
How to delegate administration rights on objects in a multi-entity context ?
Before talking about security in the strict sense of the word, there is another question. Although the configuration of services and security parameters can only be done centrally, local teams need to carry out support actions: creation or modification of an internal or guest account, resetting of authenticators, creation of a Microsoft 365 group or a distribution list, etc.
The service administration roles, the Azure AD roles, do not offer privilege segregation by perimeter; an Exchange Online administrator will therefore be able to handle all mailboxes. It will not be conceivable to give them in complex organisations or in regulated contexts. Several strategies are available, depending on the maturity and complexity of the organisation.
In the case of small structures, it is easiest to use the native functionalities:
- RBAC roles: RBAC Exchange and Intune roles generally provide the right level of granularity to manage objects in native portals;
- Administrative Units: Administrative Units, finally in GA since the end of September, are the equivalent of RBAC for Azure Active Directory. They take the form of containers in which an administrator can create or modify objects, which makes sense for support activities.
In the case of larger structures, good practice is not to manage objects (users, mailboxes, groups, SharePoint sites, etc.) directly in native portals. What is needed is an interface that allows all these objects to be managed, while taking into account the business logic and the target administration model. Below are three examples of interfaces:
- In-house development of a “Custom Automation Engine”: this interface will be decorrelated from the IAM and very often a large powershell / Graph API machine;
- Integration of a connector to the current IAM solution in order to present a complete management of the objects by disregarding their direct hosting;
- Investment in a SaaS Management Platform (SMP): software publishers have specialised in the creation of management tools for Office 365, combining object administration, licence management and security and operational supervision functions. Among these solutions, which are still relatively unknown, are ManageEngine, CoreView and Quadrotech.
Please note: this interface, dedicated to support teams, will be distinct from an interface open to all users allowing them to centrally create guest users, SharePoint sites, Teams, etc. In concrete terms, this second interface could be integrated with ITSM tools, SMP or even be developed based on Power Apps and Graph API.
How to protect access to these accounts ?
10 measures to secure administration accounts
Depending on the security licenses, mainly the EMS bundle, Microsoft provides a number of controls to secure administration accounts.
Most of these could also be obtained via third-party tools.
Basic measures to secure the administration account
- A dedicated administrator account
An administrator must have an account dedicated to administration, different from the office automation account. It should be cloud-only where possible (e.g. wavestone.onmicrosoft.com).
- Multi-Factor Authentication
Multi-factor authentication is no longer an option today, and even less so for administrators.
This measure is available for everyone, for all licences:
- Via MFA for Office 365 (also called MFA with per-person inheritance) which forces a challenge at every connection;
- Via Security Defaults which forces an additional factor to be registered for all users and imposes the MFA for administrators at each login;
It is also important to ensure that legacy authentication protocols that do not support MFA are disabled. These would allow single sign-on to be bypassed.
It will also make sense to limit the types of additional factors available; what is the point of securing administration accounts if the second factor is the administrator’s Gmail address.
Highly recommended security measures
- Unlicensed Office 365 account
Without a licence, it will not be possible for an administrator to access the different services and data of the platform, or to have a mailbox.
Please note that some services, such as Power Apps or Power BI, require a licence to access the administration portal. In practice, it can be interesting to create a security group that allocates the necessary licences for administrators.
- Conditional Access (with Azure AD P1)
Conditional access allows you to evaluate the context when accessing an Office 365 service and to authorise access accordingly. For example, access can be blocked depending on the type of workstation used (whether managed by the company or not), the network on which the user is connected, the application in question or the user’s administrative role.
In a Zero Trust logic, there should be no differentiation between the internal and external network, especially for administrators, but rather focus on the status of the workstation and the risk of connection.
- Password Protection (with Azure AD P1)
Azure AD Password Protection provides controls over passwords. It will thus be possible to prohibit the use of a current password or a derivative (with a list predefined by Microsoft or maintained by the organisation).
A good practice is to apply this protection to all Cloud-only administration accounts as a minimum.
- Azure AD Identity Protection (with Azure AD P2)
Azure AD Identity Protection adds a notion of risk in the evaluation of user access and behaviour. Concretely, it will be advisable to define the following policies;
- Risky users: Force password change for an administrator likely to be compromised (with a Medium or High risk);
- Risky sign-in: Forcing an MFA challenge during risky access (e.g. anonymous or unusual IP).
- Azure AD Privileged Identity Management (with Azure AD P2):
Azure AD Privileged Identity Management is a service to control the assignment and use of administrative roles:
- Allocate just-in-time rights by giving an eligible role instead of a permanent one;
- Submit role activation to third party validation;
- Set up an end date for an administrative role;
- Force recertifications of administrators.
It will be relevant to distinguish the so-called sensitive roles from the others during implementation.
The monitoring of eligible administrators allows, as a bonus, to become aware of the real use of administration rights and therefore to clean up the list of administrators more easily.
It should be noted that the PIM functionalities have recently been extended to the different groups, which makes it possible to set up “Just-in-time” for more exotic cases such as RMS / AIP Super-Users.
To go even further
- Supervision of administrator actions to detect abnormal behaviour
Once all these security measures are in place, all that remains is for you to implement supervision to detect non-compliance with the previous rules and abnormal behaviour.
And for this, nothing better than to refer to our article on the subject to understand the available logs.
- Setting up a Privileged Access Workstation
Administration is by definition a critical action. It must be carried out within a perimeter of trust. The provision of PAW, or administration post, will enable us to achieve this objective.
The configuration of the administration station should be simple (no local administration rights, restricted Internet browsing, blocked USB ports, pre-installed PowerShell modules, etc.). But restricting the connection of an Office 365 administrator from this workstation may cause more problems. There are several possibilities for this:
- In a modern context, a simple answer is to rely on Microsoft tools: define an administration workstation profile in Intune and assign it to the administrators. With a conditional access rule, it is possible to require a compliant workstation when connecting.
- In a more traditional model, it is possible to set up an authentication silo with administrators and associated workstations. In this way, we would have a model similar to the third-party model well known to AD teams.
- Other approaches are also possible, even if more complex: association of a certificate and a reverse proxy or even a bastion.
- Keep up to date with good practices and news
It cannot be repeated often enough that Office 365 is a Cloud platform and is constantly evolving. Keeping up to date will continue to increase its level of security over time.
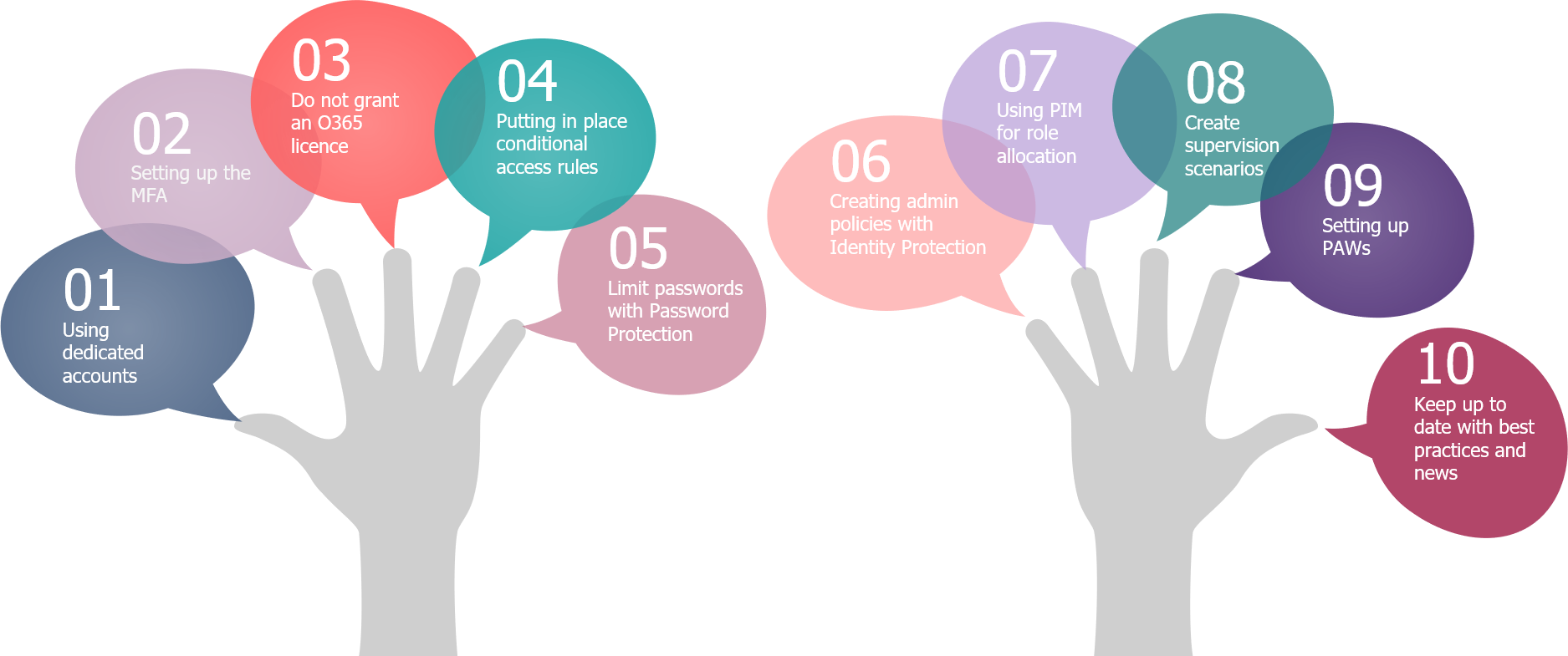
Figure 3 – The security of accounts, measures that can be counted on the fingers of one hand
Focus on glass breaking accounts
A good practice in the administration of the Microsoft platform is the setting up of administrator accounts that allow control over the platform to be regained in the event of an incident. These are called glass-breaking accounts. These accounts should allow full control over the Office 365 tenant and are therefore assigned the role of Global Administrator.
These accounts must be secure; however, we must not forget their specificity which consists in using them in the event of an incident. Thus, the security imposed on these accounts must remain compatible with the urgent nature of their use. These accounts must therefore comply with the following recommendations:
- To be cloud-only accounts
- No MFA configured (or at least a third party MFA)
- Storage of the password in a safe which only identified members of the security team or Office 365 can access
- Setting up alerts to check that these accounts are not used outside of an incident procedure requiring the use of glass breakage.
It is also recommended not to use a specific naming convention for these accounts, they should not catch the eye of a possible attacker!
Conclusion
Security on Office 365 is based on technical measures to protect administrator accounts, as well as the implementation of a target administration model, which includes clear governance and processes, tools to implement this delegation of rights, and mechanisms to maintain it over time.
But whatever protection measures are implemented, security rests first and foremost with the administrators of the solution. Awareness raising and controls for administrators will be essential.
Administrators must bear in mind that their accounts give access to extremely sensitive information and actions: they are therefore the preferred target of hackers!
As O365 is constantly evolving, each new feature introduced by Microsoft may also bring with it its share of security problems that need to be studied and taken into account. Take the opportunity to update your documentation: O365 risk analysis, service configuration, delegation model…always without forgetting to allow your administrators to train!


