After having discovered the premises of securing Industrial IS through the mapping of these systems and their partitioning, we will now explain their administration.
Administration – the nerve center of network architecture
Good administration of an IS is essential to guaranteeing its availability and security. When carrying out an IS security program, you must be clear about the objectives you want to achieve. The good practices we observe in the field include:
- Creating an administration network isolated from the production network with both central and local scope whose aim is to protect administration flows and avoid integrity losses on flows used to manage sensitive operations;
- Protecting the administrative equipment to prevent an attacker from controlling these critical elements directly;
- Standardizing, as far as possible, practices and equipment to facilitate the deployment of secure, or even centralized, administration architecture, and to maintain security levels over time. This can be achieved by pooling resources within a central, dedicated team.
To note: here, we are discussing only the administration of industrial IS infrastructure. Production PLCs, for example, are administered by the business functions in terms of configuration and will pass through the dedicated configuration and maintenance team, when updates are required.
The first step is to create the structure of the isolated and overarching administration network. This objective can be achieved by putting in place the following measures:
- To optimize and pool resources, and especially to assure the DRP[1], the administration network must be constructed around one or more datacenters.
- In order to reduce the risk of an attack propagating by using an infected site as a springboard, the WAN[2] network placed between the datacenter and the industrial installations can be configured as a hub and spoke[3] network, which ensures the separation of each installation.
- To guarantee the integrity and confidentiality of administrative flows, these must be isolated within a specific VRF[4] or VPN[5] administration network between the datacenter and each site. Putting in place such a dedicated administration network requires, in particular, the use of telecoms and security equipment, as well as dedicated interfaces on the servers.
- For the most important sites, the risk of intrusion via the user LAN[6] can be reduced by setting up an administration LAN which is only accessible from the datacenter’s administration LAN. However, such architecture must provide a resilient solution in the event that the WAN is cut to allow sites to access it directly and also for equipment that simply cannot be maintained remotely.
- Companies with multiple sites can also use a standardized housing that embeds all the security functions required for the site to be interconnected. This facilitates configuration and security maintenance.
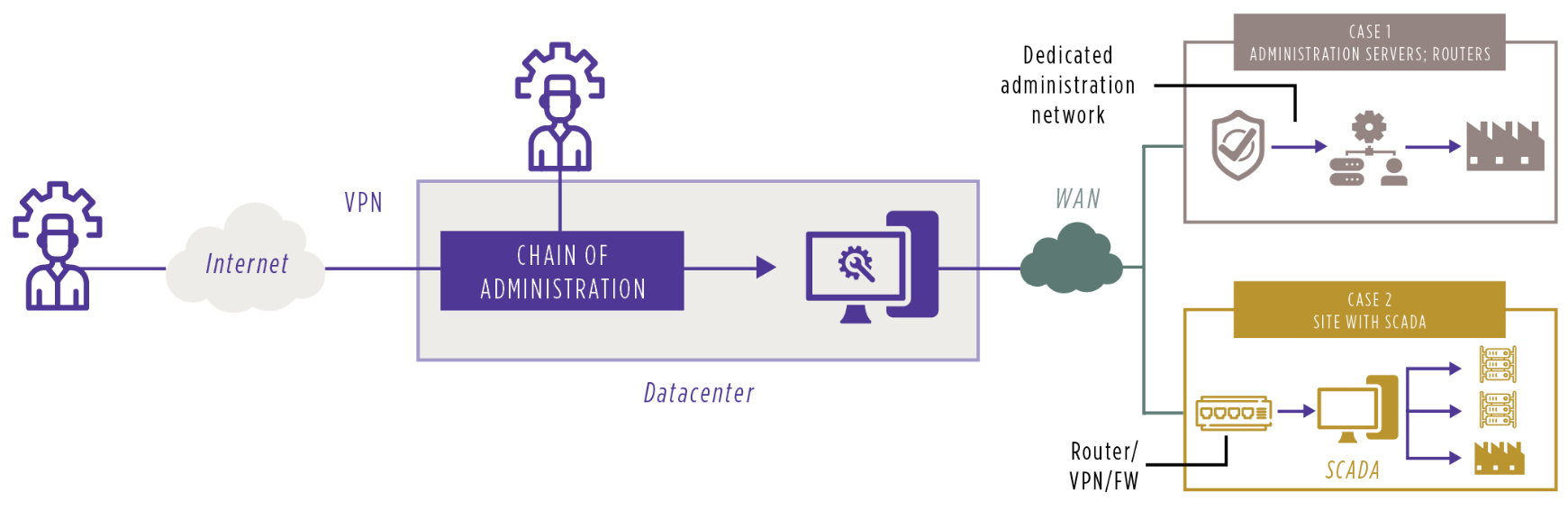
Diagram showing the interconnection of a site with or without a SCADA
The second step consists of connecting the administration tools and equipment to be administered to this network, while protecting it from compromise.
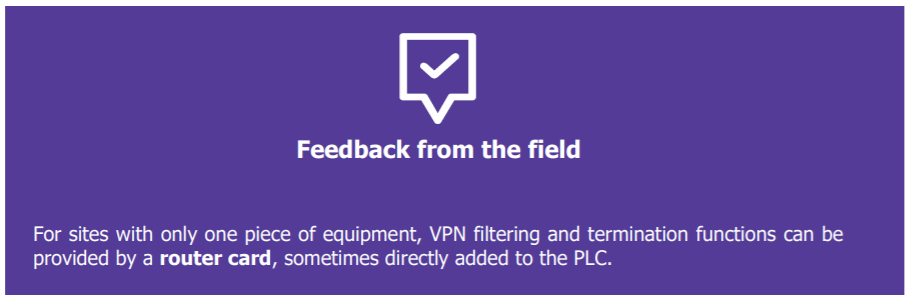
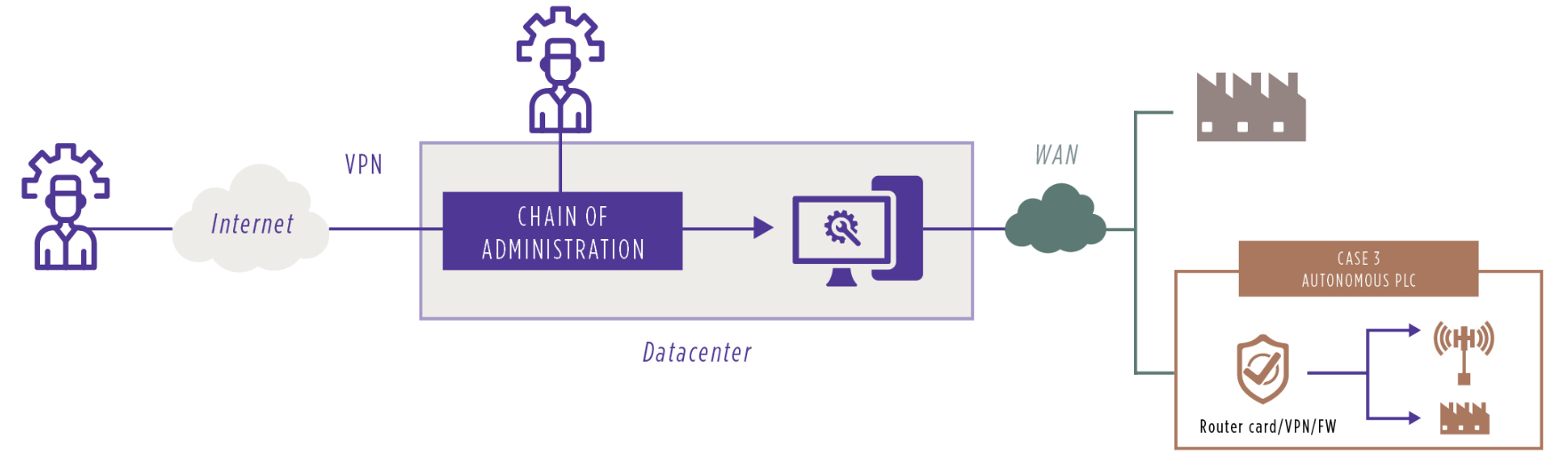
Diagram showing the interconnection of a standalone site
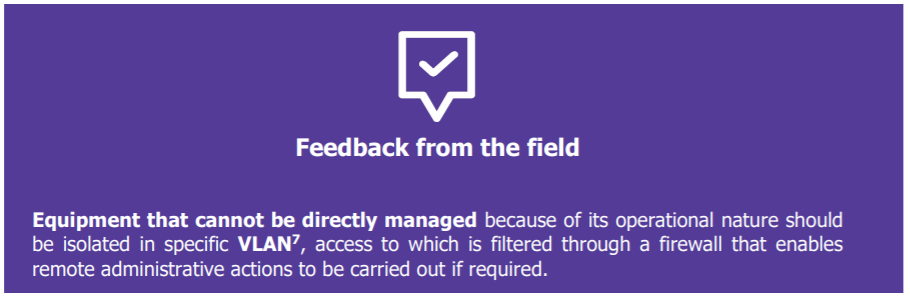
There may also be a variety of reasons to keep part of the IS fully disconnected. A disconnected IS removes the ISS risks, leaving only business risks. Disconnection also lowers the level of exposure and therefore the risk of intrusion. A risk analysis should be carried out to determine how to proceed. The associated infrastructure will need to be modified: moving from simple local administration to dedicated administration – which can be costly. These various network bricks, then, enable administrators to access the industrial equipment. However, they must also be given access to the necessary tools.
Administrator tools: how to meet needs while guaranteeing security
Because corporate and industrial ISs are generally managed separately, they each use their own tools – although these may be based on identical products. This type of configuration meets several objectives. It:
- Assures access control on the administration interfaces, reducing the likelihood of appropriating a means of attack and the fraudulent use of the tools;
- Tracks administrator activity to reduce the potential impact of an attack, by providing a means of detection and response, and facilitating investigation following an event.
This requires the implementation of an administration chain.
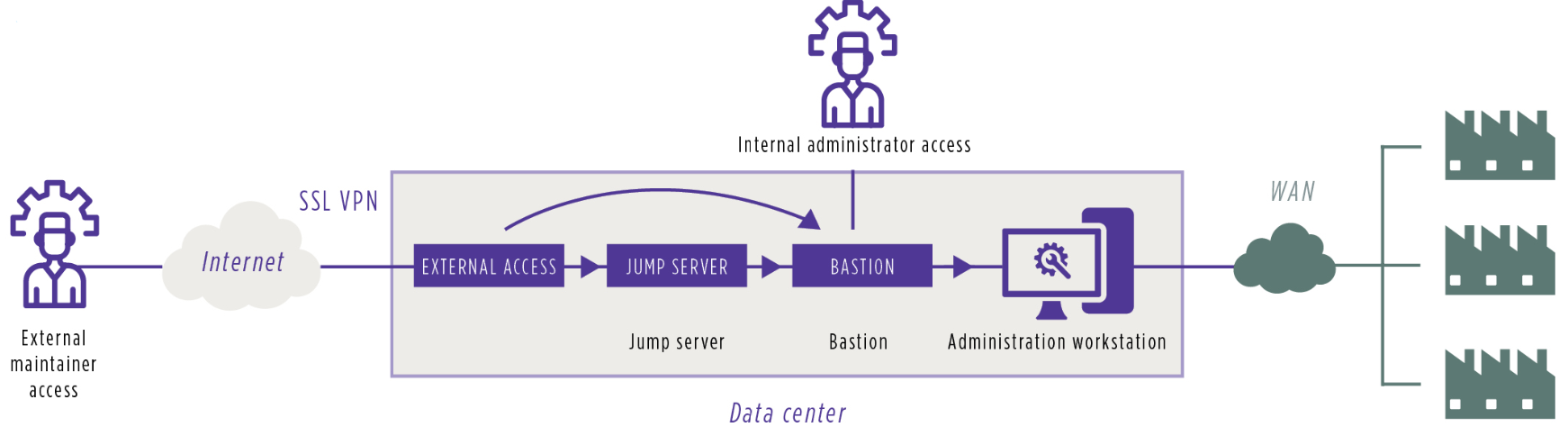
Diagram showing the main functions involved in a chain of administration
To centralize access and maintain close control of authorizations, an administration bastion must be set up. Generic accounts are handled by the bastion and protected in its digital safe. This also ensures the traceability of activity and reduces the risk of theft from generic, privileged accounts. The bastion can also secure administration flows by performing protocol translation (for example, from Telnet[8] to SSH[9]).
Equipment, especially telecom equipment, whose security levels are sufficiently mature (including detailed management of rights, traceability, individual accounts, etc.) can be directly administered without passing through a bastion.

The establishment of a dedicated administration workstation, where the tools needed for corporate management will be housed, requires a process to be put in place for their installation. This will ensure the workstation can remain secure and that the list of tools being deployed on the IS can be documented.

Planning for external maintainers
Lastly, it’s essential that access by third-party maintainers is secure in order to limit the risks that arise from improper or unmanaged access, such as infection of the IS after the installation of an unauthorized tool, data loss triggered by a malicious third party, the unavailability of equipment, etc.
An external access point with strong authentication will be needed to confirm the identity of users. Such an access point allows maintainers to access a rebound server which is controlled and hardened by the customer, while also ensuring the traceability of activity. Here, more sophisticated customers deploy solutions that allow the third-party access to the IS for the duration of the intervention only – and then only once access has been approved internally.
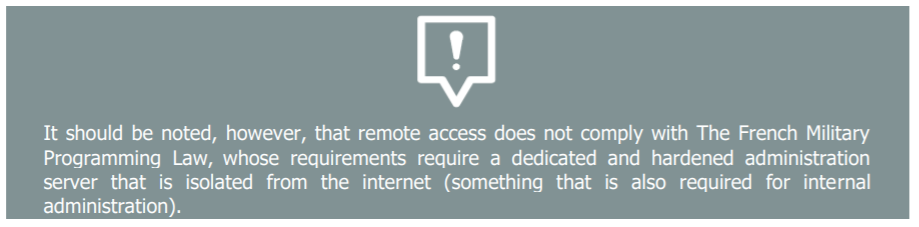
The configuration and maintenance servers that are dedicated to the site and PLCs must be rigorously monitored to keep them up to date and secure, especially in terms of the tools deployed on them.
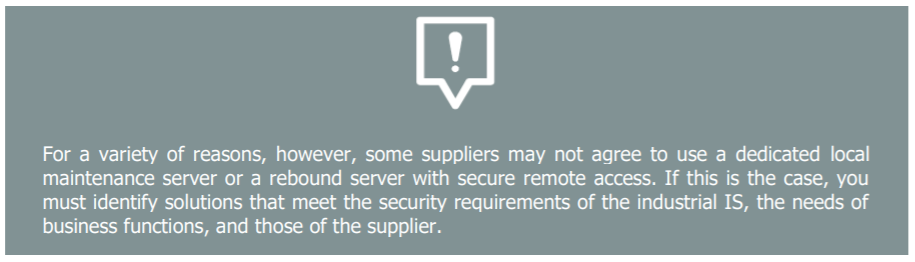
For more detailed information, note that there is an ANSSI[11] working group dedicated to the cybersecurity of industrial systems. Its PIMSEC framework[12] recommends a range of security requirements that can be incorporated into contracts with industrial IS service providers.
We now have knowledge of our equipment and the solutions to secure and manage it. However, cybersecurity issues evolve over time, so it is essential to guarantee a level of security over time and to deploy adequate means of detection. How can this be done? This will be the topic of our next article!
[1] Disaster Recovery Plan.
[2] WAN i.e. Wide Area Network.
[3] Hub and Spoke i.e. A network around the datacenter.
[4] Virtual Routing and Forwarding
[5] VPN i.e. Virtual Private Network.
[6] LAN i.e. Local Area Network.
[7] VLAN i.e. Virtual Local Area Network
[8] Telnet i.e. Terminal Network, Telecommunication Network, or Teletype Network.
[9] SSH i.e. Secure Shell
[10] RDP i.e. Remote Desktop Protocol
[11] ANSSI i.e. The French National Cybersecurity Agency.
[12] PIMSEC i.e. ANSSI’s framework for security requirements for industrial systems integrators and maintenance providers.


