The NIST Cybersecurity Framework (CSF) is widely recognized as a landmark in the evolution of the cybersecurity industry. Given the rapidly-changing cybersecurity landscape, it is vital to keep up-to-date with new developments. To this effect, NIST recently released the long-awaited version 1.1. However, more needs to be done.
In response to industry feedback, including Wavestone’s continuous involvement in the framework development (see our most recent contributions here and here), NIST is now working hard to allow the guidelines to more easily apply to organizations, thanks to sector-specific “Profiles” (e.g., Manufacturing Profile released in September 2017).
The Financial Services Sector Coordinating Council (FSSCC) recently held a workshop hosted by NIST in Washington, D.C., to further develop the Financial Services Profile of the framework. It gathered not only industry members but also regulators such as the FED and the OCC. While it is still preliminary, here are few takeaways…
A new risk-tiering methodology
First and foremost, the profile introduces the concept of risk tiering similar to that of the FFIEC Cybersecurity Assessment Tool (CAT), but with qualitative rather than quantitative criteria. It proposes thirteen questions to determine the organization’s criticality level from 1 (Critical) to 4 (Relevant) based on criteria such as systemic importance, as well as geographical and geopolitical considerations. This criticality level then determines applicable “diagnostic statements” to assess.

The methodology aligns well with industry best practices and is tailored to financial services. However, the sequence of questions to determine an organization’s inherent risk is likely to have most if not all financial institutions rated at Level 1 or 2. For example, any organization collecting and/or managing end-consumer Personally Identifiable Information (PII) would be designated a Level 2: Significant risk. While coverage of PII and privacy in general is welcome in a context of increased privacy concerns, it may not be so relevant from an inherent risk perspective.
Qualitative assessments, such as the one proposed here, are relevant for smaller institutions, but bringing cybersecurity risk management practices closer in maturity to those of credit and market risk management would require leveraging quantitative assessment methodologies. The recent paper Cyber Risk for the Financial Sector: A Framework for Quantitative Assessment from an IMF economist points in that direction.
Significant changes to the Framework Core and diagnostic statements
The profile builds on to the Framework Core with two new functions: “Governance” and “Supply Chain/Dependency Management.” These additions put more emphasis on key areas, but at the cost of changing the well-known “Identify-Protect-Detect-Respond-Recover” structure, which is helpful for communicating with business and senior management.
The profile does not stop here, as it also increases the number of Categories and Subcategories, +8 and +20 respectively. While these additions are mostly relevant, they are not specific to Financial Services and could therefore be added to the Framework Core itself.
Based on this structure, the profile defines 300 diagnostic statements leveraging again the FFIEC CAT and other resources from NYS DFS, FSB, and CPMI-IOSCO.
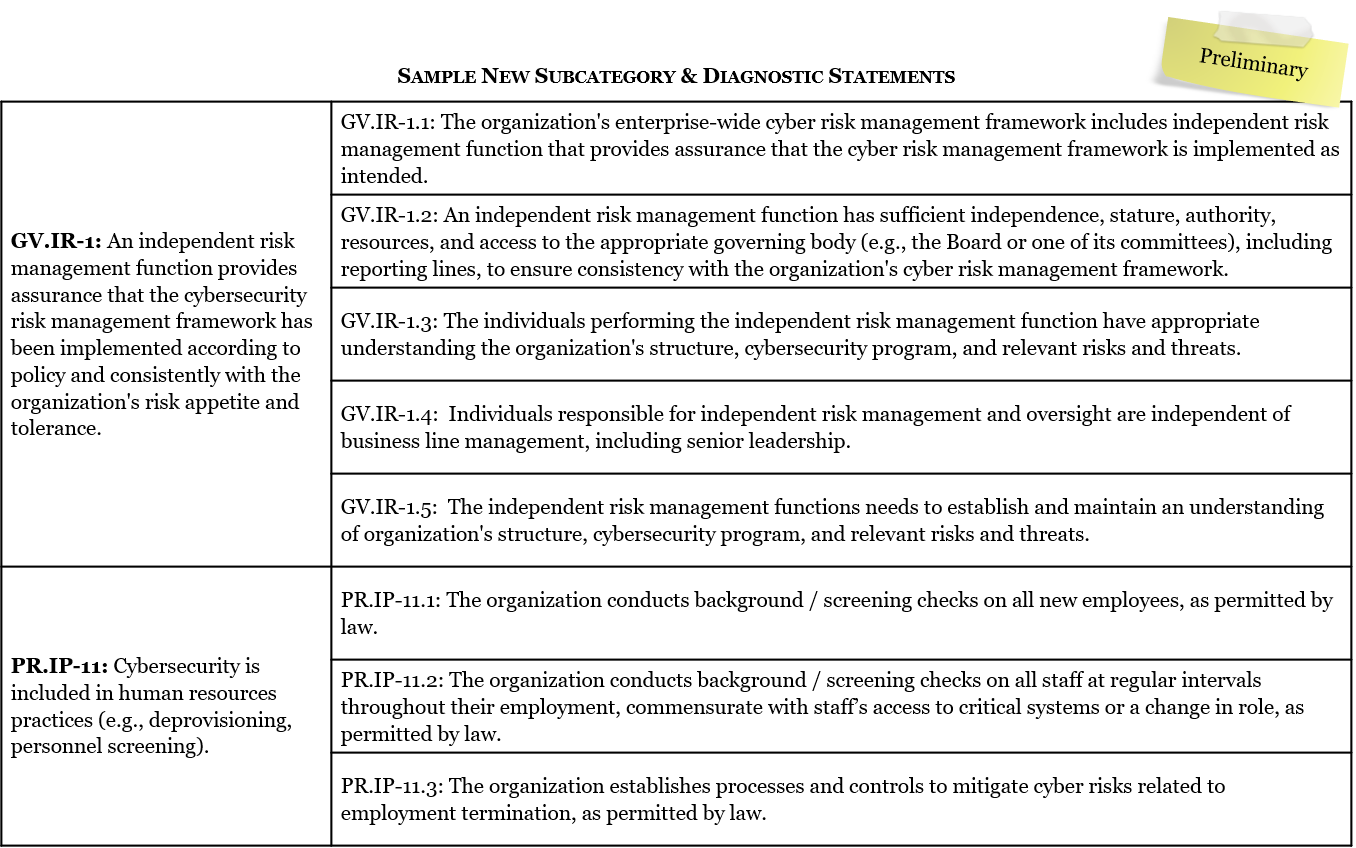
More precise assessment criteria
When utilizing the NIST CSF, the FFIEC CAT, or any other generic framework or tool, most firms at some point end up defining specific potential answers to assessment criteria. Indeed, firms may have protection mechanisms in place, but they may not be consistently deployed across all assets. Similarly, while a measure may not yet be in place, a clear path forward may have been defined. Such scenarios are relevant to reflect an organization’s cybersecurity maturity.
The profile addresses this issue by proposing seven possible answers which successfully address common scenarios: “Not Applicable,” “Yes,” “Yes-Risk Based,” “Yes-Compensating Controls Used,” “Partial-Ongoing Project w/Action Plan,” “Not Tested,” and “No.” This addition is certainly an important step toward more consistent framework use and a foundation for maturity measures across organizations and across industries.
The need to think global
The proposed profile is currently presented as U.S.-centric. Indeed, most questions in the risk-tiering section and most diagnostic statement references relate to U.S. references. While this focus would be helpful for initial adoption in the U.S. market, it could be a barrier to expansion moving forward. Country-specific references are helpful, but the Profile itself should be kept as generic as possible, with U.S. references provided as add-ons only. FSSCC peers could then develop other add-ons at the country or region-level.
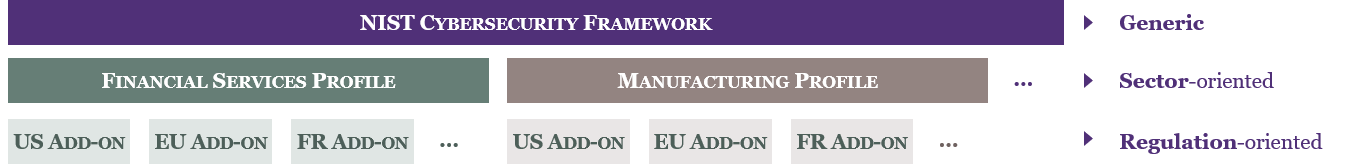
Moreover, the proposed profile must further address the challenge of managing different maturity levels across geographies. Given the pervasive nature of cyber risk, shouldn’t organizations ensure a consistent maturity across geographies unless sufficient segregation is ensured? As challenging as it sounds, the magnitude of risk certainly justifies this approach.
As regulations are introduced worldwide and organizations are more and more global, managing complexity and avoiding inconsistencies necessitate a common framework. The Financial Services Profile as intended by the FSSCC has an important role to play in this respect. More than a pragmatic approach to leverage the NIST CSF, it aims at greater regulatory harmonization and streamlined regulatory compliance efforts. It is laudable and certainly long-anticipated by organizations.


