We’re using more and more online services—both at home and at work. This transformation in usage calls for a review of authentication methods—and there are two main needs that must be balanced: the user experience (and how to maintain it), and security (and how to protect access to services).
Calling time on passwords
Authentication means using an agreed method to prove that someone is the person they claim to be. From the earliest times, the most widely used method has been, almost certainly, the password. However, passwords are an irritation for users and have numerous security limitations.
A collective sense of having “had enough”…
We all imagine, from time to time, not having to rack our brains for the right password when we connect to our most used applications. But it’s clear that this remains just a fantasy at present.
The promise of single sign-on is a long way from being a reality in corporate settings, and the increasing popularity of password vaults reveals something of the challenges faced by users: the multiplicity and patchy relevance of password policies, obligatory password changes, not to mention the irritation of having to reset passwords.
Having said that, the password’s main advantage remains its universal applicability and familiarity.
…but with a limited degree of security
Many cyber-attack scenarios rely, at some point or other, on a password—ideally that of a privileged account—being compromised. Various techniques are employed: high-volume combination tests (Brute Force), intercepting communications (Man in The Middle), and reconstituting passwords from their footprints (Rainbow Table).

Security measures to guard against these attacks exist (such as encryption, hashing, salting, and blocking accounts), but these are not always implemented systematically—or satisfactorily. As the saying goes, “From a corporate point of view, passwords are like nuclear waste: just bury them deep and hope they don’t leak.”
In addition to the technical weaknesses already discussed, user behavior presents a major risk: reusing the same password for different applications, passwords that are too weak or easy to guess, incrementation, etc. When a password is reused for several applications, it acts as the weakest link—thus weakening the whole chain.
Ultimately, the poor user experience and limited level of security offered by passwords are forcing companies to look for new authentication methods.
What are the options?
Authentication methods are generally divided into four categories:

What I know
These authentication methods are based on a key or code that the user knows. They represent the bulk of the solutions used today in both professional and private setting. Today’s solutions include traditional passwords, PIN codes, and secret questions. The latter, however, are rarely used, because they are either too generic (for example, “What’s your favorite color? “) or too difficult to remember.
What I own
Here, security is based on a specific piece of equipment being in the user’s possession. In particular, we are seeing the following in use:
- Smartphones
Smartphones allow—both in professional and private settings—the securing of the most sensitive operations: accessing internal company networks, confirming online payments, or carrying out non-typical banking operations.
Smartphones can be used to achieve authentication in a number of ways:
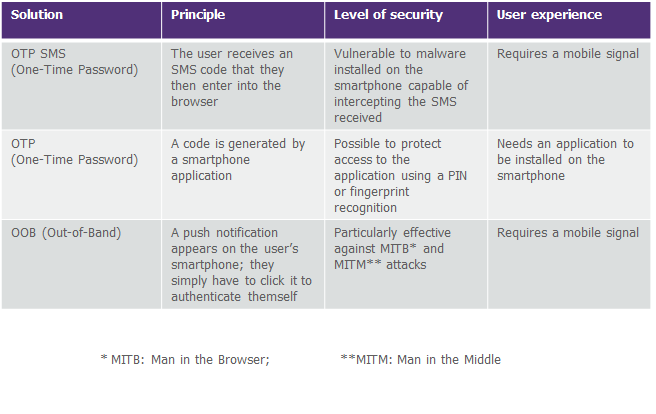
- Authentication tokens
A token often takes the form of a mini-calculator that makes it possible to generate a single-use code (OTP), with the token itself protected by a PIN code chosen by the user. Historically widely used in companies (for VPN access in particular), and occasionally in the private sphere to connect to particular customer areas, tokens are, nonetheless, giving way to smartphones, which provide a less expensive method.
- Smartcards
Smartcards contain a certificate that is used to prove the holder’s identity. A card reader is essential for this type of authentication; moreover, certificate management requires infrastructure and life-cycle-management procedures (covering issue, withdrawal, loss, etc.). Normally reserved for the corporate world, their use tends to be limited to specific groups or uses (IT administration, financial operations, etc.).
- U2F keys
This item comes in the form of a standard USB stick, but instead of storing files, it stores a unique key linked to the user. Based on a standard developed by the FIDO Alliance, the solution combines a robust level of security (including resistance to phishing attacks) with a good user experience (the keys can remain connected to one of the device’s USB ports) because a simple key press is sufficient for authentication. Note, however, that this does not involve fingerprint recognition.
- A connected object, such as a watch
This last solution—the most innovative in this category— allows users to connect via a connected object that they already own. As an authentication method it’s little used in corporate settings, but Apple, for example, offers an option to unlock a computer by simply approaching a device with another Apple connected object.
Solutions like this, based on the possession of a device, are differentiated mainly by their degree of ergonomics. In any case, it’s essential to manage “enrollment” (the linking of the object to its holder), replacement, loss, and theft of the relevant device.
Who I am
The physiological characteristics of a person, such as a fingerprint, the vein pattern of a hand, irises, faces, the signature of a voice, or even a heart rate, also make it possible to authenticate a user. The use of these solutions, for most people, is limited to opening their workstation or smartphone (via a fingerprint or face recognition). However, companies have used such solutions for a number of years to control access to rooms or highly sensitive areas.
What I do
Keystroke rhythms, mouse movements, using a phone, or touching a screen, are different ways to distinguish a legitimate user from an impostor or robot. These behavioral, biometric solutions require a large amount of data in order to be reliable, but this is improving, thanks to new Machine-Learning-based approaches. These solutions are used more as security measures that complement authentication (detecting robotic-attacks, account sharing, etc.).
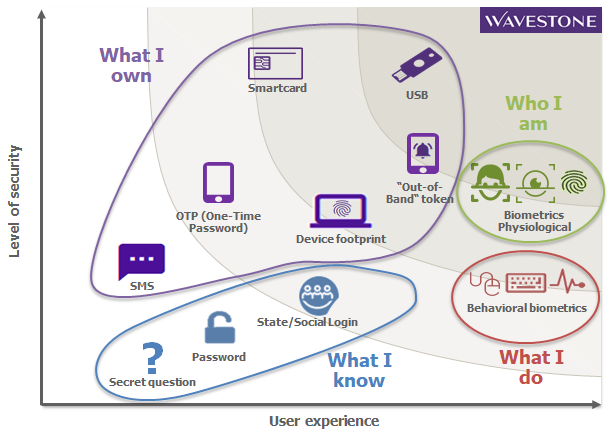
As a summary, the figure below shows the different authentication solutions according to their level of security and ease of use.
User experience and security, a circle that can’t be squared?
We believe that it is possible to reconcile the user experience with security. Below we set out four possible routes to achieving it.
Route 1: simplifying the use of passwords
While it seems too fantastic to imagine the use of passwords being completely abandoned, some of their failings can be addressed. The frequency of data entry can already be reduced via identity-federation mechanisms that provide access to both corporate and partner services. In addition, chatbots are emerging to simplify the password resetting process, and are helping drive significant improvements in user experience. As for security, raising users’ awareness about the proper use of passwords is still an essential activity if risks (from social engineering, spam, phishing, password theft, etc.) are to be reduced.
Route 2: adapting the security requirements to the context
Just as you have to adapt your road speed to the weather conditions, the concept of risk can guide us in the level of security needed to authenticate a user. Thus, to access non-sensitive information, a simple password will suffice; but more sensitive operations (a bank transfer involving a significant amount, for example) will require the user to be authenticated with greater certainty, using a combination of several authentication factors. Other criteria can be taken into account to assess risk, for example the PC or smartphone being used, the geographical location, the time of connection, or even whether the user is exhibiting their habitual behavior.
Beyond the authentication phase, the level of risk can also influence the time allowed before issuing a new authentication request (no need to retype a Facebook password as long as the user stays on the same PC or smartphone, reauthentication via webmail every X days only, etc.).
In the end, then, authentication is no longer seen as an event but as a continuous process.
Route 3: let the use choose the authentication method
Rather than imposing a single authentication method on all users, Bring Your Own Token (BYOT) lets users choose the one that best suits their needs. The idea is to offer a choice of solutions with comparable levels of security.
Today, Facebook and Google offer BYOT as a second authentication factor, using a registered smartphone or secure USB key, for example.
In the world of work, this method remains less developed at present, but it’s easy to imagine such a method being offered to specific groups: those with particular work mobility requirements, the technological appetite for it, etc.
Route 4: make use of accounts that exist already
It’s more and more common for people to use their social media accounts (Facebook, Google, or LinkedIn, for example) to connect to e-commerce sites or other websites. A Social Login enables the creation of an account on the new site to be simplified, and limits the number of passwords to be remembered.
However, not all online services are designed to use a Social Login. Public or parapublic services for example, favor a State Login which allows users to log in using a tax, health, or similar identifier, and to carry out a range of online administrative activities. And these uses are in continuous development.
In conclusion
While passwords are not set to disappear completely, the search for alternatives is gathering pace: uses and technological solutions are evolving rapidly, consortia and new standards (such as OAuth2 and OIDC) are emerging, and, these days, the user experience, as well as security, is core to the thinking.


