The first article was about vulnerabilities in Business Continuity Plans (BCP) and an overview on recent major cyber attacks that paralyzed a significant amount of an Information System (IS). This second article introduces some leads and means to improve cyber-resilience strategy.
Strengthening crisis management
Cyber crises are specific: they are often long (several weeks) and sometimes difficult to grasp (what has the attacker been able to do? For how long? What is the impact?). Often, affected external parties such as lawyers, authorities, suppliers, and sometimes even clients themselves are not well-prepared on the subject matter. Thus, it is necessary to adjust existing plans that have not been designed to cater to the cyber threat aspects.
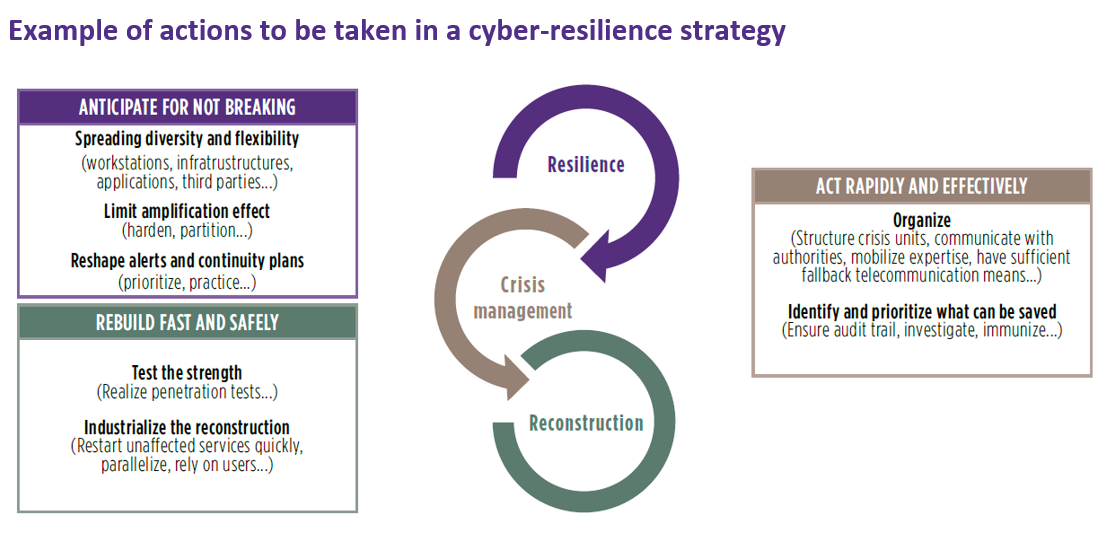
Even if they is an operational player in cyber crisis management, the CIO should not be over-utilized in either the investigation or the defense measures if it is detrimental to overall production and recovery. Anticipation of these kinds of measures is vital to the recovery effort. It is necessary to clearly identify the teams which need to be mobilized to respond to the crisis in a timely manner, and to organize the parallel interventions on both the investigation and the construction of the defense plan.
Beyond the organizational point of view, the CIO will have to ensure that they also have the investigation tools (mapping, search for attack signature, independent crisis management IS, capability to analyze unknown malware, etc.), remediation tools (Capabilities to rapidly deploy technical corrections, fragmentation of the IS to save what could be saved, IS surveillance toolkit) and reconstruction tools (access to backup, access to minimal documentation, capabilities to deploy workstation) required to understand the position the attacker took in the IS, to repel it and to ensure it doesn’t return.
Writing a crisis management guide that defines the essential steps, the macro-level responsibilities, and the key decision points can be done as an added bonus. With that, it is essential to conduct crisis exercises to ensure readiness for when one actually occurs.
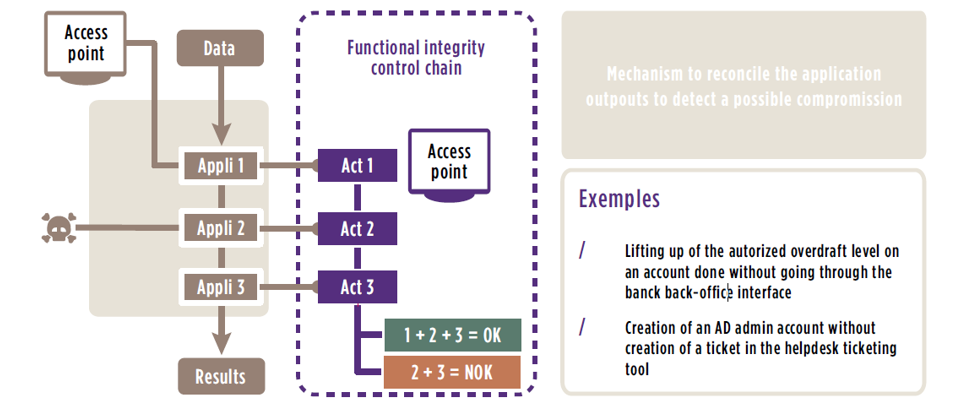
Here is a functional integrity control chain :
Rethinking continuity plans
Continuity plans have to evolve to adapt to cyberthreats. Sometimes, this means they may have to be completely rebuilt.
There are many possible solutions that can cover all types of continuity plans.
The user recovery plan, for example, can evolve to integrate USB keys containing an alternative system which could be used in case of logical destruction of employee workstations. Some organizations have also decided to provision an allotted number of workstations directly with their suppliers to have them delivered quickly in case of physical destruction.
The IT continuity plan, on the other hand, can include new solutions which could be efficient in the event of a cyberattack. The most publicized one aims to build “non- similar facilities” by duplicating an application without using the same software, operating system, or production teams. It is an extreme solution, very costly and difficult to maintain, but one that is considered for specific, critical applications in the financial industry – most notably, payment system infrastructure.
Other less complex solutions such as adding functional integrity control in the business process have also been considered. The concept relies on the implementation of regular controls, at various levels and at different places within the application chain (“multi-level controls”). This enables quick detection of attacks. An alert could be raised in case of an interaction with technical layers, such as a modification of a value directly inside a database, without passing through regular business workflows (via graphical interfaces), for example. In another case, these mechanisms can also be applied to infrastructure systems by reconciling admin account creation request tickets with the number of accounts really in the system.
As a more intermediate complexity level solution, it is possible to implement a “floodgate”, or as a system and network isolation zone. This floodgate – for example, the industrial IS – can be activated in the event of an attack and could isolate the most sensitive systems from the rest of the IS.
These, often major, evolutions must be part of an existing recovery strategy review so that one can assess their vulnerability and the interest of deploying new cyber-resilience solutions, particularly on the most critical systems. The evolution of Business Impact Analysis (BIA) to include this dimension can be a key first step.
Without cybersecurity, cyber-resilience is nothing
Implementing these new cyber-resilience measures requires significant efforts. Note that these efforts can be wasted if both these recovery solutions and the regular systems are not already appropriately secured and under detailed surveillance. The CISO is the key player to ensure that these often started but rarely finalized initiatives come to fruition. Help from the Risk Manager (RM), or the Business Continuity Manager (BCM) if such a position is in place, will be valuable. It is widely acknowledged today that it is impossible to secure a system 100%, which means that organizations have to accept the inevitability of an attack occurring, at which moment the RM or the BCM will make full use of their role.
Protect, detect, respond, remediate, and rebuild. These are the pillars of a strong cyber-resilience program which can only be attained if the BCM and the CISO roles combine their full range of capabilities and work hard, hand-in-hand!


