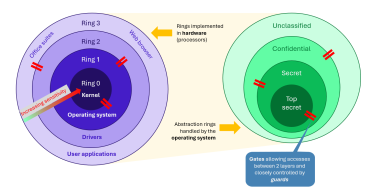
The 2 types of protection ring. On the left, the hardware implementation used to protect the system. On the right, a transposition for the user context, with classification levels ranging from ‘unclassified’ to ‘top secret’, which are managed by the operating system.